Naz Bozdemir
2024-05-15 12:43:43
www.hackerone.com
Modern pentesting approaches use independent security researchers working under strict NDAs and advanced software platforms to streamline the process. However, with many vendors focusing on other core security products and services, it’s important to make sure that the pentest offering you choose provides you both the trust, compliance, and verification you need and the findings you’d expect from skilled security researchers. The most common pentesting approaches include:
- Traditional Pentesting via Consultancies
- Traditional Pentesting as a Service (PTaaS)
- Community-driven Pentesting as a Service (PTaaS)
- Automated Pentesting
This blog will focus on community-driven PTaaS vs. automated pentesting, and which pentest methodology is best for your organization based on unique goals and requirements.
What Is Automated Pentesting?
Automated pentesting, including autonomous approaches powered by generative AI (GenAI) algorithms and advanced machine learning models, uses predefined scripts or tools to systematically scan and assess systems for vulnerabilities based on recognized signatures or patterns. This method rapidly identifies “known unknowns” and can be deployed frequently to ensure more regular security checks.
|
Pros |
Cons |
|
|
What Is Community-driven PTaaS?
Community-driven PTaaS represents a modern evolution of pentesting, harnessing the collective expertise of a global community of vetted security researchers. Using a Software as a Service (SaaS) delivery model, it provides immediate results and fosters enhanced communication, all powered by advanced platform capabilities.
This method not only adheres to regulatory mandates, but also cultivates a collaborative relationship between security teams, developers, and pentesters, leading to comprehensive security assessments and incremental improvements in the code security over time.
|
Pros |
Cons |
|
|
Community-driven PTaaS vs. Automated Pentesting
Effectiveness
In pentesting, effectiveness measures the impact of the testing process and outcomes, guaranteeing that the tests yield meaningful, actionable, and high-impact results. The elements addressed below underscore the depth, precision, and thorough nature of a modern pentesting alternative, ensuring a structured and methodology-driven assessment of an organization’s security posture.
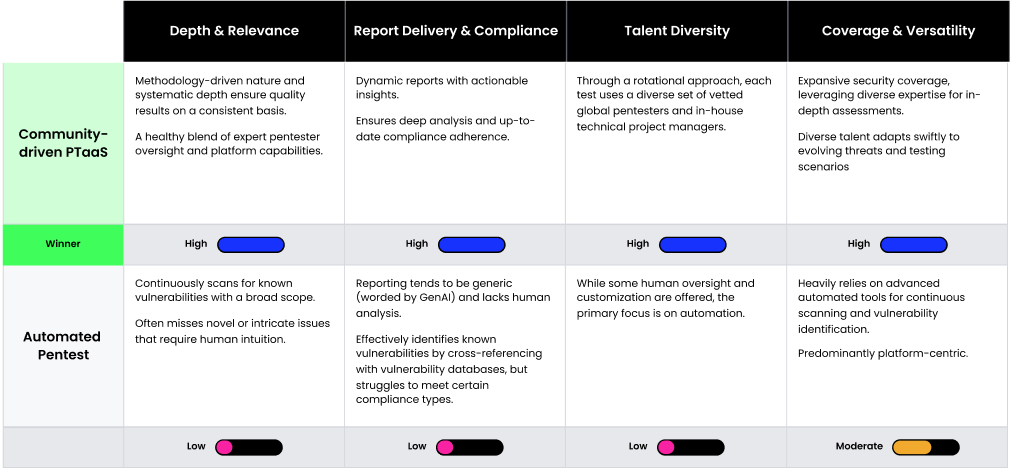
“We wanted to know what we didn’t know. We didn’t want to just rely on the results of the custom- ordered penetration tests. The complexity of our systems didn’t allow researchers to find in-depth scenarios during fixed, time-bound engagements.”
— Joe Xavier, VP of Engineering, Grammarly
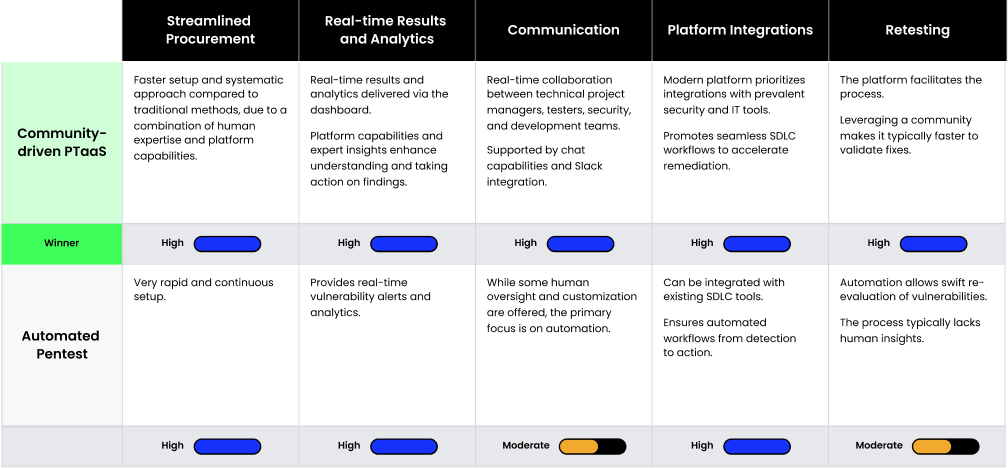
Efficiency
In the context of pentesting, efficiency is not just about meeting objectives—it’s about doing so through coordinated, easily repeatable processes. Together, the components listed below assess whether the pentesting process, from procurement to results delivery and remediation, is streamlined, ensuring an integrated execution that optimizes both time and resources.
Value
Security leaders are challenged to showcase the value of pentesting against its cost. In evaluating community-driven PTaaS and automated pentesting, keep in mind that the impact of each pentesting method varies based on its application, the caliber of expertise involved, and the precise goals underpinning the test objectives.
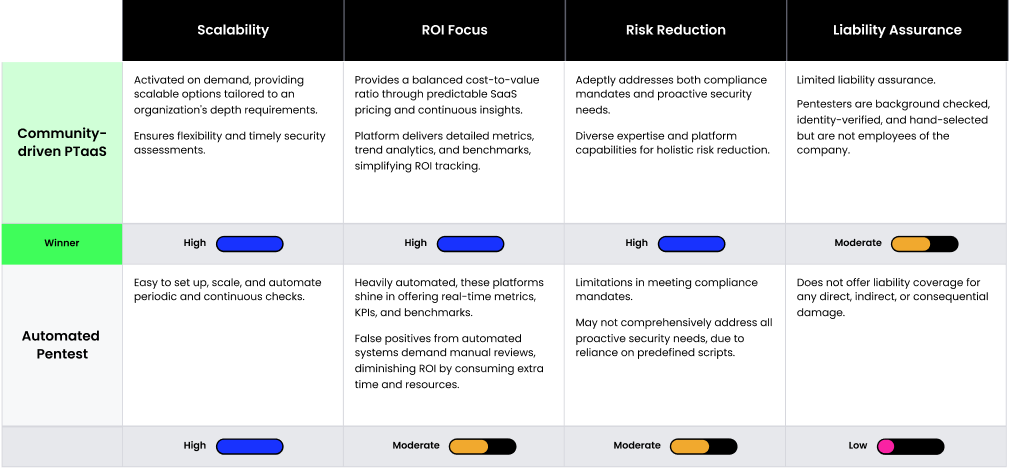
When evaluating community-driven PTaaS against the automated pentesting model, community-driven PTaaS emerges as a standout solution. It’s a flexible approach tailored to meet an organization’s unique requirements and is competitively priced. Community-driven PTaaS is the premier choice for comprehensive testing combined with in-depth analysis, all while ensuring a swift setup and completion of the assessment.
The Power of PTaaS With HackerOne
HackerOne Pentest transcends routine compliance checks, delivering in-depth insights, efficiency, and actionable results tailored to your business and security needs.
“We walked away from HackerOne’s pentest engagement with greater confidence that our assets are secure and compliant, due to the collaborative and attentive nature of the testers. The onboarding and testing portion was more seamless compared to other pentest vendors we’ve engaged with. Everything from the real-time dashboard view to the communicative Slack channel was highly received by our internal stakeholders.”
— Rachel Curran, Director of Risk and Compliance, Logikcull
If you’re ready to learn more about how community-driven PTaaS measures up against other pentesting methodologies, download the eBook: The Pentesting Matrix: Decoding Modern Security Testing Approaches. Or, tell us about your pentesting requirements, and one of our experts will contact you.
Support Techcratic
If you find value in our blend of original insights (Techcratic articles and Techs Got To Eat), up-to-date daily curated articles, and the extensive technical work required to keep everything running smoothly, consider supporting Techcratic with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to future updates and improvements. I am committed to continually enhancing the site and staying at the forefront of trends to provide the best possible experience. Your generosity and commitment are deeply appreciated. Thank you!
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending any funds to ensure your donation is directed correctly.
Bitcoin QR Code
Your contribution is vital in supporting my efforts to deliver valuable content and manage the technical aspects of the site. To donate, simply scan the QR code below. Your generosity allows me to keep providing insightful articles and maintaining the server infrastructure that supports them.

Privacy and Security Disclaimer
- No Personal Information Collected: We do not collect any personal information or transaction details when you make a donation via Bitcoin. The Bitcoin address provided is used solely for receiving donations.
- Data Privacy: We do not store or process any personal data related to your Bitcoin transactions. All transactions are processed directly through the Bitcoin network, ensuring your privacy.
- Security Measures: We utilize industry-standard security practices to protect our Bitcoin address and ensure that your donations are received securely. However, we encourage you to exercise caution and verify the address before sending funds.
- Contact Us: If you have any concerns or questions about our donation process, please contact us via the Techcratic Contact form. We are here to assist you.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.













































![J1772 Charging Adapter for Tesla Model 3 Y S X [Safety Certified] 80 Amp 240V AC Fast…](https://techcratic.com/wp-content/uploads/2024/11/71Mii9k40bL._AC_SL1500_-360x180.jpg)















![Japanese Movie – The X From Outer Space (Uchu Dai Kaijyu Girara) [Japan BD] SHBR-263](https://techcratic.com/wp-content/uploads/2024/11/81rV3BDVGJL._SL1024_-360x180.jpg)






