Sandeep Singh
2024-03-21 12:00:13
www.hackerone.com
HackerOne’s 7th Annual Hacker-Powered Security Report states that information disclosure is the third most common vulnerability reported in both bug bounty and pentest. It makes up 11% of all vulnerability types discovered on the HackerOne platform.
Despite being considered a “low-hanging fruit” vulnerability type, information disclosure can significantly impact an organization, including data breaches and theft, exposure of personal identifiable information (PII), financial damages, and legal/compliance repercussions.
Let’s look more closely at information disclosure — what it is, how it’s used, and how to remediate it.
What Is Information Disclosure?
An information disclosure vulnerability is a type of software vulnerability that allows an unauthorized user or attacker to access sensitive data or information that should be protected. This could include:
- Revealing system data like usernames, passwords, access keys, encryption keys, etc.
- Exposing source code, configuration files, or other internal application details
- Leaking personal or private data about users
- Disclosing technical details that could aid an attacker
Information disclosure flaws often result from a lack of robust controls, insecure design, and coding practices like:
- Improper input/output filtering
- Insufficient authorization checks
- Failure to properly handle exceptions and errors
- Lack of data security practices
- Misconfigurations or outdated/vulnerable software components
They can provide attackers with intel to mount further attacks or directly expose confidential data. Preventing information disclosures requires techniques like secure input validation, proper error handling, and protecting sensitive data through obfuscation, encryption, and strict access controls.
Business Impact of Information Disclosure
1. Financial Losses:
- Exposure of sensitive data like trade secrets, intellectual property or customer information can directly lead to financial losses and competitive disadvantages.
- Regulatory fines and penalties for violating data privacy laws like GDPR or HIPAA.
- Cost of security incident response, customer notifications, legal fees, etc.
2. Reputational Damage:
- Loss of customer trust if their personal data is leaked, leading to churn and difficulties acquiring new customers.
- Damage to brand reputation and public perception of the company’s security practices.
- Negative media attention surrounding the data breach.
3. Business Disruption:
- Information disclosures may force systems to be taken offline for incident response.
- Outage of critical applications and services until the vulnerability is remediated.
- Productivity losses from dealing with the security incident.
4. Compliance Violations:
- Leaks of regulated data like payment information and health records can result in non-compliance penalties.
- Potential government audits and increased scrutiny of security practices.
What Industries Are Impacted By Information Disclosure?
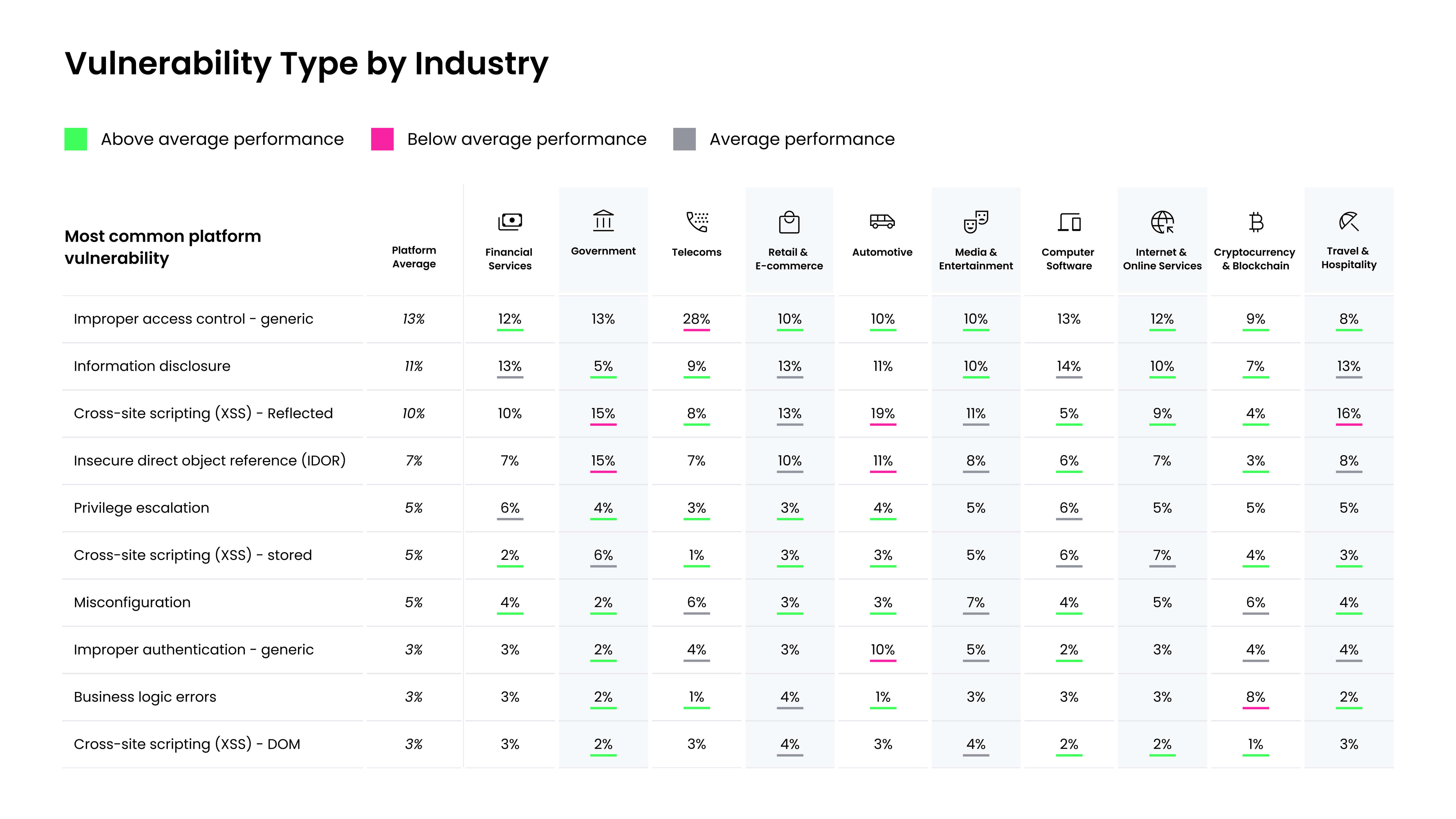
Information disclosure issues do not discriminate by industry. However, it is more prominent in some industries than others. The chart below illustrates the top vulnerabilities across the HackerOne platform by industry. Information disclosure only makes up 5% of vulnerabilities identified in the Government space, yet it makes up a much higher 14% in the Computer Software industry. Government organizations and agencies have stricter-than-average regulations in place when it comes to protecting private or sensitive information, so it stands to reason that the Government space would see fewer information disclosure vulnerabilities.
Look at how many of your vulnerabilities are improper access control compared to the average for your industry.
A Real-world Example of an Information Disclosure Vulnerability
HackerOne’s Hacktivity resource showcases disclosed vulnerabilities on the HackerOne Platform. Check it out to see how specific weaknesses have been identified and fixed. The following information disclosure example demonstrates how a hacker discovered a vulnerability in Basecamp that led to the leakage of AWS keys and user cookies via uninitialized memory leaks.
Customer: Basecamp
Vulnerability: Information Disclosure
Severity: High
Summary
A high-severity vulnerability was reported by hacker @neex that allows a malicious actor to gain access to sensitive information such as AWS keys and user cookies from Basecamp servers. This vulnerability existed due to an uninitialized memory leak in an outdated version of the librsvg library used by Basecamp. The issue stems from the way Basecamp handled certain SVG images, which could lead to the leakage of arbitrary memory contents that could have contained sensitive data.
Impact
The exposure of sensitive information such as AWS keys and user cookies to an unauthorized actor can have severe consequences. AWS keys could be misused to access and compromise Basecamp cloud infrastructure, leading to a full breach. Leaked user cookies could have led to account hijacking and unauthorized access to user data and accounts on Basecamp.
Steps to Reproduce
- Prepare a malicious SVG image that exploits the uninitialized memory leak in the outdated librsvg version used by Basecamp.
- Submit or upload the malicious SVG image to Basecamp in a way that triggers its processing.
- Observe the leaked memory contents, which may include AWS keys, user cookies, and other sensitive information.
Remediation
To remediate this vulnerability, the hacker recommended:
- As the first and the easiest fix for this particular bug, update the librsvg to the latest version.
- Another possible quick-fix option would be to forbid uploading SVG avatars or to skip preview generation for them. Note that the previews are not generated for the SVG files anywhere except the avatars, thus, exploiting librsvg issues is impossible using these endpoints.
- As a long-term solution, move image preview generation to an isolated environment. Converting every image in another process inside a networkless docker would eliminate all the class of image converter-related issues.
Reward
The hacker received a $8,868 bounty and gratitude from the Basecamp team for helping them avoid an incident.
“Great work here. Thanks for the brilliant report and all your patience and help with it.”
— Basecamp
Secure Your Organization From Information Disclosure With HackerOne
This is only one example of the pervasiveness and impact severity of an information disclosure vulnerability. HackerOne and our community of ethical hackers are the best equipped to help organizations identify and remediate information disclosure and other vulnerabilities, whether through bug bounty, Pentest as a Service (PTaaS), Code Security Audit, or other solutions by considering the attacker’s mindset on discovering a vulnerability.
Download the 7th Annual Hacker Powered Security Report to learn more about the impact of the top 10 HackerOne vulnerabilities, or contact HackerOne to get started taking of information disclosure at your organization.
Support Techcratic
If you find value in our blend of original insights (Techcratic articles and Techs Got To Eat), up-to-date daily curated articles, and the extensive technical work required to keep everything running smoothly, consider supporting Techcratic with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to future updates and improvements. I am committed to continually enhancing the site and staying at the forefront of trends to provide the best possible experience. Your generosity and commitment are deeply appreciated. Thank you!
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending any funds to ensure your donation is directed correctly.
Bitcoin QR Code
Your contribution is vital in supporting my efforts to deliver valuable content and manage the technical aspects of the site. To donate, simply scan the QR code below. Your generosity allows me to keep providing insightful articles and maintaining the server infrastructure that supports them.

Privacy and Security Disclaimer
- No Personal Information Collected: We do not collect any personal information or transaction details when you make a donation via Bitcoin. The Bitcoin address provided is used solely for receiving donations.
- Data Privacy: We do not store or process any personal data related to your Bitcoin transactions. All transactions are processed directly through the Bitcoin network, ensuring your privacy.
- Security Measures: We utilize industry-standard security practices to protect our Bitcoin address and ensure that your donations are received securely. However, we encourage you to exercise caution and verify the address before sending funds.
- Contact Us: If you have any concerns or questions about our donation process, please contact us via the Techcratic Contact form. We are here to assist you.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.

















































![2024 Upgrade Tesla Model Y Sunshade Roof [Never Sag, No Gaps, Nano Ice-Crystal Coatings]…](https://techcratic.com/wp-content/uploads/2024/11/61USyoncEvL._AC_SL1500_-360x180.jpg)









![Japanese Movie – The X From Outer Space (Uchu Dai Kaijyu Girara) [Japan BD] SHBR-263](https://techcratic.com/wp-content/uploads/2024/11/81rV3BDVGJL._SL1024_-360x180.jpg)








