Naz Bozdemir
2024-02-20 14:11:12
www.hackerone.com
In evaluating the myriad of security testing methodologies available, we consider them against three pivotal metrics to ascertain their overall efficacy and alignment with organizational needs:
- Quality/Effectiveness: Effectiveness measures the method’s ability to provide reliable and accurate vulnerability detections, comprehensive system coverage, compliance with standards, and a diverse testing team for nuanced perspectives.
- Speed/Efficiency: Efficiency concerns the method’s operational benefits, such as the ease and rapidity of obtaining pentesting services, the immediate delivery of results and analytics, continuous and transparent communication, and effortless SDLC integration.
- Value: Value explores the method’s ROI, focusing on scalability, both tangible and intangible outcomes from pentesting efforts, and its success in risk mitigation.
With these comparison categories in mind, let’s explore the “Speed” factor more closely and see how each security testing alternative measures up.
Security Testing Alternatives
The landscape of security testing is diverse, where players offer a variety of methodologies and security testing alternatives that cater to different organizational needs. Understanding these alternatives is crucial for selecting the one that best fits your security strategy, but it’s not an easy task. Here are the primary security testing methods currently in use:
- Traditional Pentesting via Consultancies: Pentesting services are delivered by professional service providers, primarily leveraging their in-house salaried pentesters or long-term contractors.
- Traditional Pentest as a Service (PTaaS): Essentially, traditional pentesting with an added user interface.
- Community-driven Pentest as a Service (PTaaS): A modern evolution of pentesting, harnessing the collective expertise of a global community of vetted security researchers.
- Automated Pentesting: Including autonomous approaches powered by generative AI (GenAI) algorithms and advanced machine learning models, uses predefined scripts or tools to systematically scan and assess systems for vulnerabilities based on recognized signatures or patterns.
The Problem With Pentest Speed
Organizations are often frustrated with the lengthy timelines associated with initiating a pentesting program and receiving tangible results. This frustration stems from the complex setup processes, the need for detailed scoping, and ad-hoc coordination efforts with the external pentesting firm and internal teams.

The time it takes to identify and report vulnerabilities is one of the most common complaints of pentesting. Industry-standard pentests take four to seven weeks to start and seven to 10 days after the pentest concludes to get results together in a spreadsheet and deliver a final PDF report to the customer — but does it need to be this slow and archaic?
“I wouldn’t choose a provider only because of streamlined procurement, but it is a huge part of it. If I have to deal with weeks and weeks of figuring out how to pay an invoice, I could spend that time doing something a lot more important. It is SaaS, so I expect a SaaS experience, not a services experience.”
— Robert Kugler, Head of Security and Compliance, Cresta
Measuring Pentest Method Speed
When evaluating security testing options, the pace at which they deliver results and how seamlessly they integrate into existing SDLC processes is paramount. This comparison breaks down each approach, assessing the performance and the speed of the testing, as well as the feedback mechanisms.
- Procurement: Refers to the ease and speed with which pentesting services can be procured, set up, and initiated, reducing administrative overhead and delays
- Real-time Results & Analytics: Focuses on the capability to provide immediate updates, insights, and results as the testing progresses—ensuring stakeholders are always informed and can make timely decisions
- Communication: Ensures proactive and real-time communication with the technical project manager overseeing the test and the testers throughout the process
- Platform Integrations: Highlights the ability of the pentesting solution to seamlessly integrate with SDLC
- Retesting: Refers to the process of reassessing previously identified vulnerabilities for effective remediation
Our methodology evaluates different pentesting approaches against key dimensions of effective security testing, using a scale of Low to High. While the results do highlight a preferred method, it’s essential to understand that our scoring system reflects the general attributes of each security testing type. The actual effectiveness of an approach may vary based on business priorities, technology stack, and other unique factors. As you interpret the findings, remember that Speed is only one of three factors, and it may or may not resonate most with your specific business objectives.
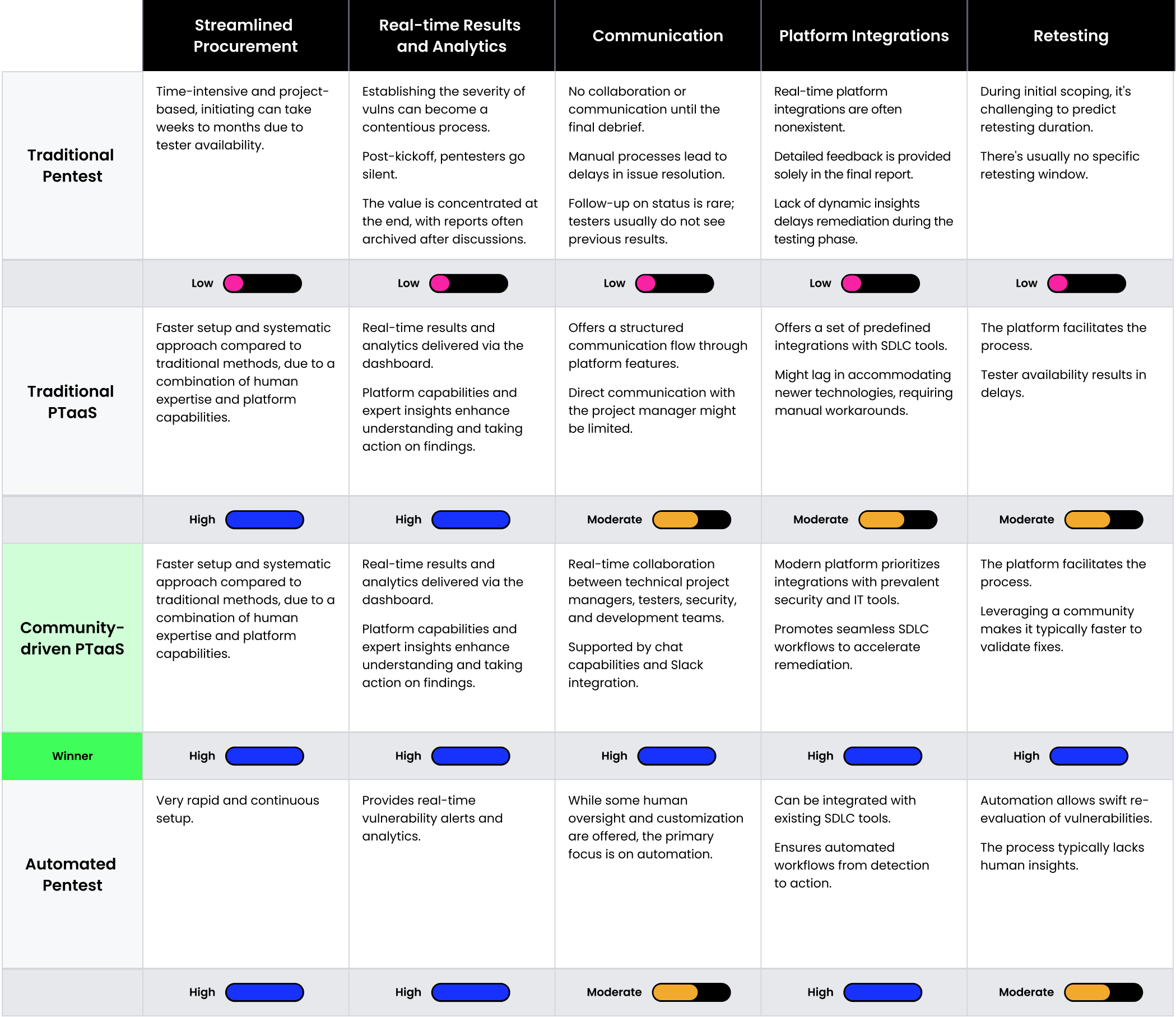
In the context of pentesting, efficiency is not just about meeting objectives—it’s about doing so through coordinated, easily repeatable processes. Together, the components listed above assess whether the pentesting process, from procurement to results delivery, is streamlined, ensuring an integrated execution that optimizes both time and resources.
“It makes a lot of sense to work with a PTaaS provider because that traditional consultancy is just not scalable. Imagine I need a review next week, and, at the same time, I have a bunch of questions from my team about the vulnerability and how we implement the fix. A traditional consultancy doesn’t have that bandwidth. You need to have that very large talent pool that you can tap into in order to deliver these services.”
— Robert Kugler, Head of Security and Compliance, Cresta
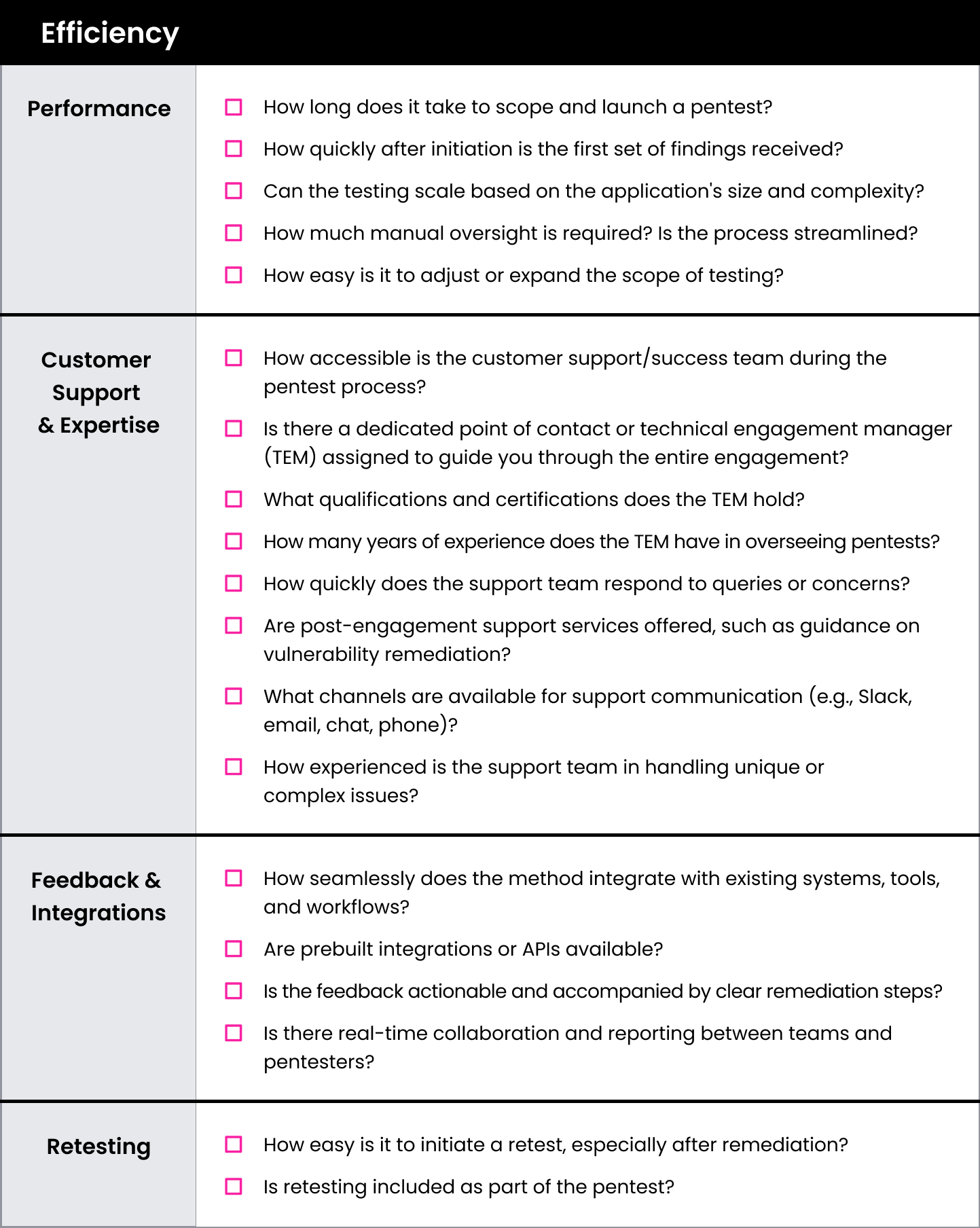
Security Testing Speed Evaluation Matrix
This checklist can be used to evaluate the speed of each of the four security testing options: traditional pentesting, bug bounty, modern pentesting via Pentest as a Service (PTaaS), and automated and autonomous pentesting.
The Power of PTaaS With HackerOne
When scoring against Speed, PTaaS stands out as a flexible approach that can adapt to an organization’s specific needs, and is priced accordingly. PTaaS is the best option when combining robust testing and deep analysis with the opportunity to quickly set up and complete an assessment.

- 4 days: New customers can initiate a new pentest in 4 business days.
- 4.4 days: HackerOne Pentest customers receive their first vulnerability report within 4.4 days on average.
- 86% of HackerOne Pentest customers receive their first vulnerability report in less than one week.

HackerOne Pentest transcends routine compliance checks, delivering in-depth insights, efficiency, and actionable results tailored to your business and security needs. If you’re ready to learn more about how PTaaS measures up in other criteria, download the eBook: The Pentesting Matrix: Decoding Modern Security Testing Approaches. Or, tell us about your pentesting requirements, and one of our experts will contact you.
Support Techcratic
If you find value in our blend of original insights (Techcratic articles and Techs Got To Eat), up-to-date daily curated articles, and the extensive technical work required to keep everything running smoothly, consider supporting Techcratic with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to future updates and improvements. I am committed to continually enhancing the site and staying at the forefront of trends to provide the best possible experience. Your generosity and commitment are deeply appreciated. Thank you!
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending any funds to ensure your donation is directed correctly.
Bitcoin QR Code
Your contribution is vital in supporting my efforts to deliver valuable content and manage the technical aspects of the site. To donate, simply scan the QR code below. Your generosity allows me to keep providing insightful articles and maintaining the server infrastructure that supports them.

Privacy and Security Disclaimer
- No Personal Information Collected: We do not collect any personal information or transaction details when you make a donation via Bitcoin. The Bitcoin address provided is used solely for receiving donations.
- Data Privacy: We do not store or process any personal data related to your Bitcoin transactions. All transactions are processed directly through the Bitcoin network, ensuring your privacy.
- Security Measures: We utilize industry-standard security practices to protect our Bitcoin address and ensure that your donations are received securely. However, we encourage you to exercise caution and verify the address before sending funds.
- Contact Us: If you have any concerns or questions about our donation process, please contact us via the Techcratic Contact form. We are here to assist you.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.

















































![2024 Upgrade Tesla Model Y Sunshade Roof [Never Sag, No Gaps, Nano Ice-Crystal Coatings]…](https://techcratic.com/wp-content/uploads/2024/11/61USyoncEvL._AC_SL1500_-360x180.jpg)









![Japanese Movie – The X From Outer Space (Uchu Dai Kaijyu Girara) [Japan BD] SHBR-263](https://techcratic.com/wp-content/uploads/2024/11/81rV3BDVGJL._SL1024_-360x180.jpg)








