Emma Whitford
2023-10-31 12:50:51
www.hackerone.com
1. Unprepared to Manage Incoming Vulnerability Reports
Naturally, the purpose of running a bug bounty program is to identify vulnerabilities beyond what your security team can find — and remediate them. However, when launching a bug bounty program, many security teams are unprepared for just how many vulnerabilities will be identified and struggle to work to address them. Without the right scoring systems in place, it can be very challenging for security teams to prioritize incoming vulnerability reports and remediate them in an organized way.
Solution: Organize and Prepare Your Activity and Scoring Platform
Security teams need an effective vulnerability activity and prioritization scoring platform to help manage the reports that come in from bug bounty hackers. HackerOne’s platform provides all the necessary insights, organization, scoring, and resources to empower security teams to effectively address vulnerabilities.
For example, our Hacktivity platform includes a CVE (Common Vulnerabilities and Exposures) Discovery feature that offers customers insights into which CVEs are being actively reported by hackers. In addition, the platform utilizes both CVSS (Common Vulnerability Scoring System) and EPSS (Exploit Prediction Scoring System) scoring, empowering strategic prioritization based on comprehensive factors.
HackerOne Customer Success Managers (CSMs) also work closely with organizations to scale hacker invites to the appropriate amount for their unique needs and goals, avoiding overwhelming security teams with an unmanageable number of hackers and reports.
2. Untested Attack Surface
One of the reasons many security teams are unprepared for what a bug bounty program will yield is they don’t have a thorough understanding of the security of their attack surface. While a bug bounty program is the right goal, security teams often skip some earlier steps, such as code reviews and pentests, that help shed light on what to expect from future bug bounty reports.
Solution: Run Code Reviews and Pentests
Each code review, performed by a specialized cohort of the HackerOne community, takes a median of 88 minutes to complete and surfaces an average of 1.2 vulnerabilities. Eighteen percent of security fixes are incomplete, making them one of the most essential types of code changes to audit.
While bug bounty is generally an ongoing program, pentests typically follow a structured methodology that encompasses a comprehensive, time-bound examination of the system, focusing on identifying vulnerabilities that adversaries could exploit.
The top vulnerabilities identified through code reviews and pentests often overlap with that of bug bounty, identifying common vulnerabilities like:
- Misconfiguration
- Cross-site scripting (XSS)
- Information disclosure
- Improper access control
In addition, the smaller scope and timeframe dedicated to code reviews and pentests make them important stepping stones toward understanding your attack surface and preparing for a bug bounty program. HackerOne pentesters can also be added to an organization’s ongoing bug bounty program, developing anchor hackers that drive even greater value.
Download the 7th Annual Hacker Powered Security Report
3. Unclear Business Case
Let’s be clear: there absolutely is a clear business case for implementing a bug bounty program. The issue is that many security leaders are challenged to articulate that business case to stakeholders and board members, and that’s a difficult conversation to have without the right information. As a result, security teams don’t receive the budgetary resources they need, and the program is run ineffectively.
Solution: Calculate Measurable ROI
It’s no secret that board members speak in the language of dollars and cents, and without a calculated breakdown of cost savings and ROI, security teams won’t be granted the appropriate budget to effectively run their bug bounty program.
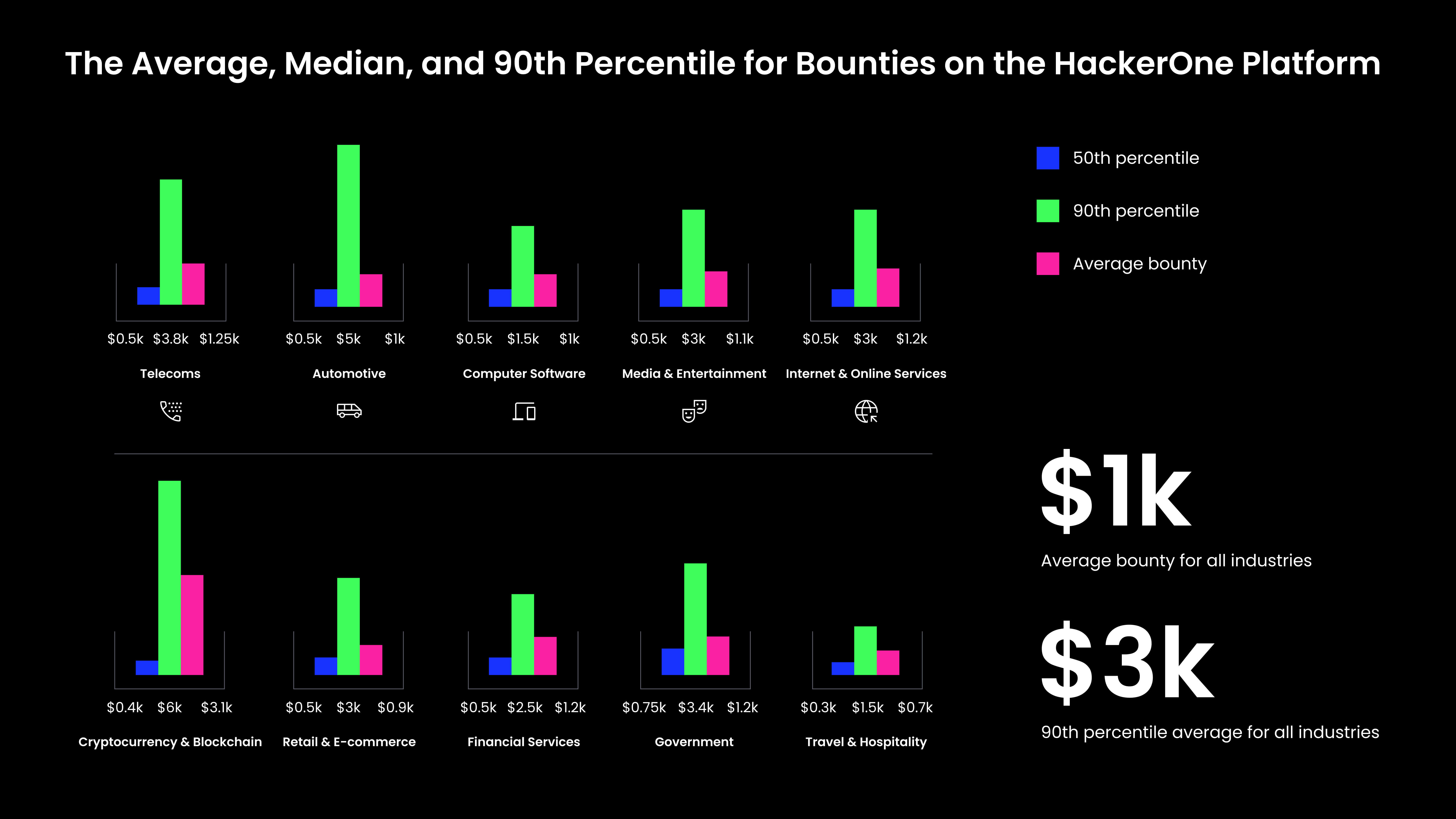
According to the 7th Annual Hacker Powered Security Report, the median price of a bug on the HackerOne platform is $500, up from $400 in 2022. The average bounty in the 90th percentile is up from $2,500 to $3,000. The cost of these vulnerabilities going unnoticed and being exploited, however, is significantly more than the cost of the bounty.
HackerOne customers consistently factor in cost savings when measuring the success of their bug bounty programs, with 59% valuing the estimated savings of reputational or customer-related incidents and 54% valuing the financial savings estimated from avoiding risk.
“Since 2019, Zoom has worked with 900 hackers, of which 300 have submitted vulnerabilities that we have had to quickly move on. We’ve paid out over $7 million. It’s a substantial investment but the returns are worth it: we find world-class talent to find real-world solutions before it’s a real-world problem.”
— Michael Adams, CISO, Zoom
4. Misaligned Incentives
While there are more factors than financial compensation, 80% of hackers hack for money (up from 71% in 2022). With this in mind, the level of financial incentivization is important when establishing bounties. Many organizations might think they know what the appropriate amount is for any given bug bounty, but they find a lack of engagement in their program from the hacker community. That’s because 48% of hackers will opt not to join a program if the bounties are too low.
Solution: Price Bounties With Peer Benchmark Data
Security teams don’t have to price bounties on an island. Peers in every industry have embraced the power of bug bounty and ethical hacking. It’s essential for teams to examine average bounty costs within their industry because the averages can be vastly different from one sector to the next. For example, you can see from the Hacker Powered Security Report below that the average bounty for Travel & Hospitality is $700, while in Cryptocurrency & Blockchain, it’s over $3,000.
5. Failure to Build Hacker Relationships
While money is certainly a significant factor for hackers when selecting a bug bounty program, it’s not the only thing they find important. In fact, there are many things that can put a hacker off of a program.
As you can see, slow response times (60%) and poor communication (55%) are actually more important than low bounties (48%) for hackers being discouraged from a bug bounty program.
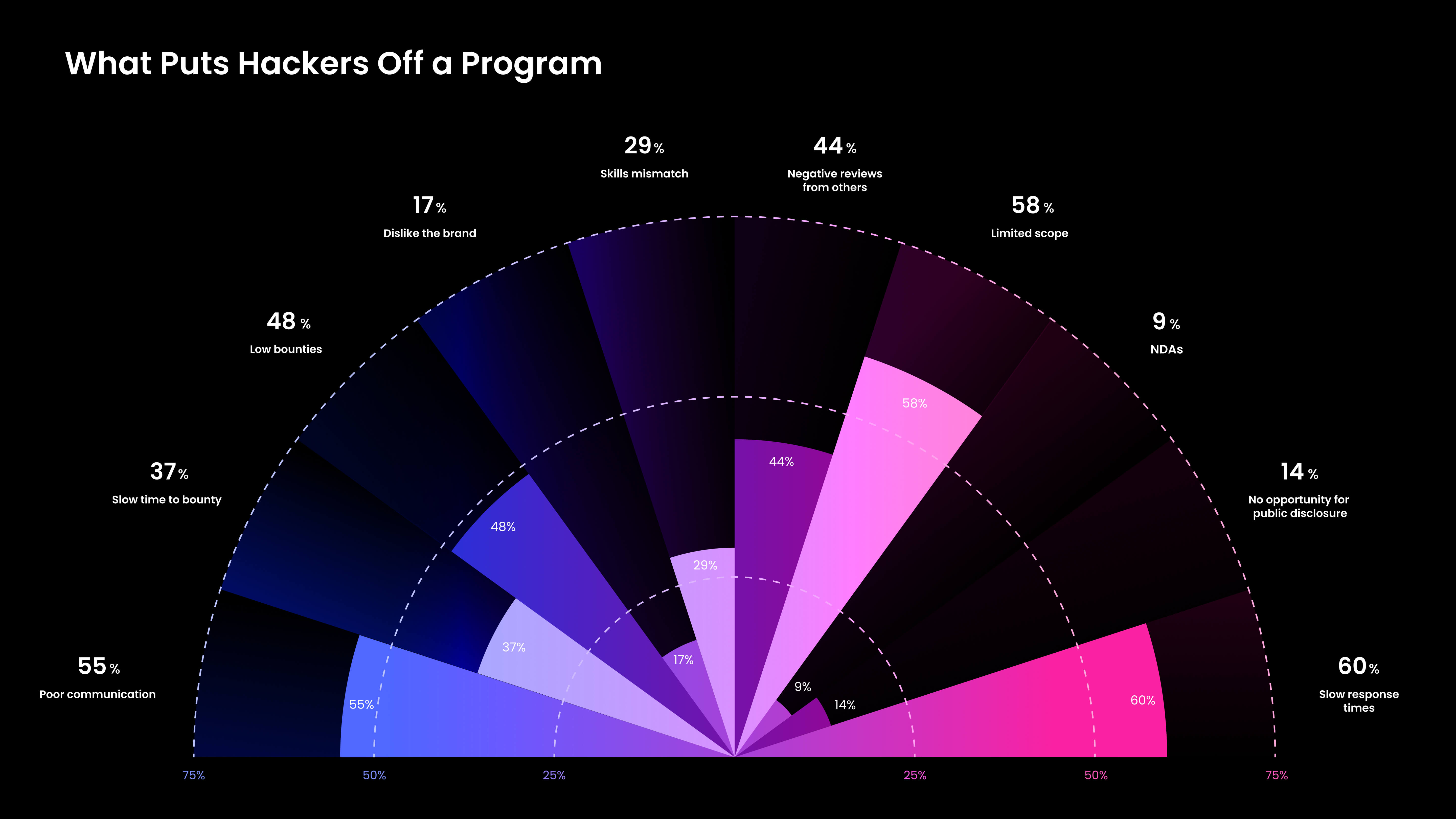
Solution: Make Your Program Work for Hackers
Hackers are more likely to spend time on your program when they have a relationship with your organization’s security team. So, your bug bounty program should offer more than just the bounty payment. In order to attract the best hackers, you need to communicate effectively, offer a varied scope through which hackers can learn, and invest the time to quickly remediate the vulnerabilities they identify.
“When I’m looking at a new program, I will look at the metrics in terms of time to triage and bounty and to what degree the program is hitting those metrics. I would advise companies to have both a public and private program. The public program will screen and interview researchers that can be moved into the private program where you can provide them with more access and resources. A private program allows you to have an elite group of hackers really digging in and finding those critical vulnerabilities. For example, some hackers specialize in reconnaissance and finding those corners of infrastructure that no one is thinking about and looking in the corners, then you have other hackers that have hundreds of servers scanning for vulnerabilities. Novelty and scale are important for delivering impactful reports.”
— Tom Anthony, Hacker
HackerOne: Combining Bug Bounty Expertise With a Deep Hacker Community
It’s challenging for security leaders to check all of these boxes in order to run the most effective bug bounty program. Managing the reports, receiving the budget, setting the right bounties, and building hacker relationships can all seem too daunting to do correctly and simultaneously.
At HackerOne, we provide the best combination of in-house expertise to run the right bug bounty program for your organization’s unique needs, with an extensive hacker community ready to go to work for you. If you want to learn more about how to run the most effective bug bounty program for your organization, download the 2023 Hacker Powered Security Report or contact our team at HackerOne today.
Source Link
Support Techcratic
If you find value in our blend of original insights (Techcratic articles and Techs Got To Eat), up-to-date daily curated articles, and the extensive technical work required to keep everything running smoothly, consider supporting Techcratic with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to future updates and improvements. I am committed to continually enhancing the site and staying at the forefront of trends to provide the best possible experience. Your generosity and commitment are deeply appreciated. Thank you!
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending any funds to ensure your donation is directed correctly.
Bitcoin QR Code
Your contribution is vital in supporting my efforts to deliver valuable content and manage the technical aspects of the site. To donate, simply scan the QR code below. Your generosity allows me to keep providing insightful articles and maintaining the server infrastructure that supports them.

Privacy and Security Disclaimer
- No Personal Information Collected: We do not collect any personal information or transaction details when you make a donation via Bitcoin. The Bitcoin address provided is used solely for receiving donations.
- Data Privacy: We do not store or process any personal data related to your Bitcoin transactions. All transactions are processed directly through the Bitcoin network, ensuring your privacy.
- Security Measures: We utilize industry-standard security practices to protect our Bitcoin address and ensure that your donations are received securely. However, we encourage you to exercise caution and verify the address before sending funds.
- Contact Us: If you have any concerns or questions about our donation process, please contact us via the Techcratic Contact form. We are here to assist you.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.


































































