Spencer Chin
2023-08-31 12:42:04
www.hackerone.com
Pentesting has been around for decades, but it hasn’t undergone the revolution that other security practices have. Organizations tend to rely on pentesting as a tool to just “check-the-box” for compliance, rather than something that actually protects their brand and customers.
Traditional pentesting engagements are slow, take up excessive bandwidth, and don’t deliver impactful results. In this blog, I will look at the common mistakes organizations make with their pentests and show how by leveraging the power of the pentester community and the efficiency of a Pentest as a Service (PTaaS) platform, pentesting can add real value to your organization.

Problem 1: Pententers Are Inexperienced
When customers tell me about their experiences with traditional vendors, they mention that they often don’t get an entire team of experienced pentesters. More often than not, they get a team mostly composed of junior pentesters with limited experience who work with a more senior pentester with more experience. As a result, the senior pentester is forced to split their time between testing, teaching, and reporting, and the customer doesn’t get the full value.
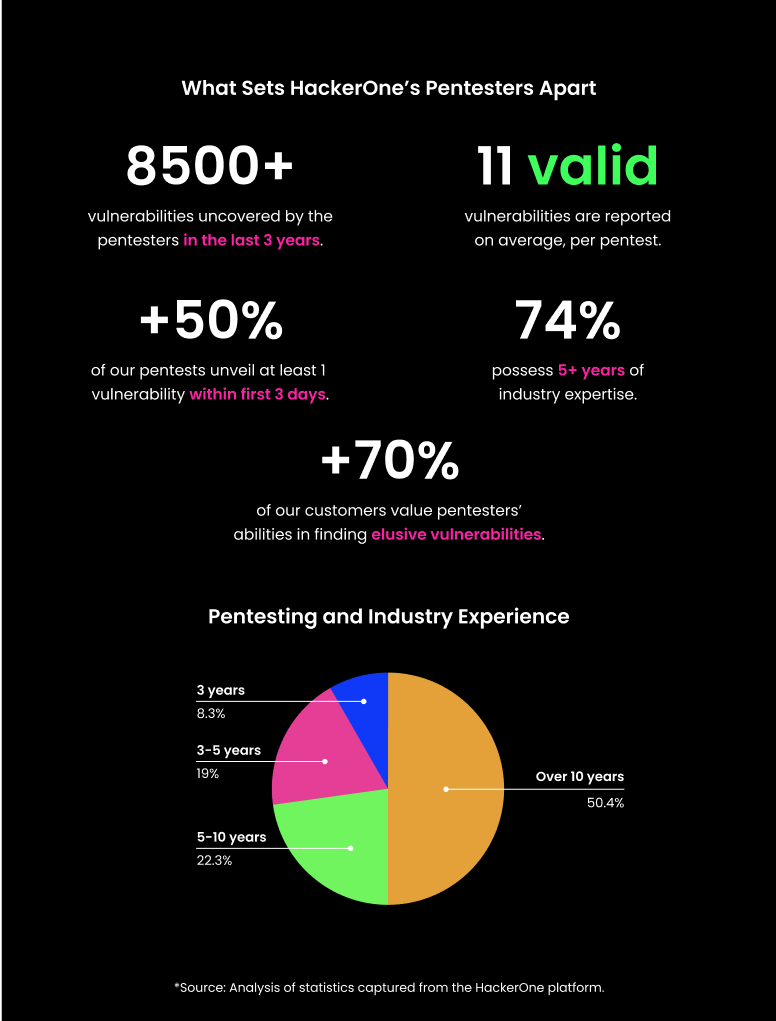
HackerOne pentesters are an elite subset of our community that is hand-selected and vetted by our Community team. As part of the vetting process, the Community team evaluates their past professional pentest experience, their performance on other HackerOne programs, and their certifications and other credentials. Due to the high standards we maintain for our pentesters, 65% of our community has over 5 years of experience with pentesting. This means that our customers are getting experienced, credentialed testers with every pentest.
Problem 2: Pentesting Is Too Checklist-Driven
Pentesting is methodology-driven by nature, but oftentimes traditional pentest firms are more focused on moving through a checklist than actually finding vulnerabilities. Because most of our Pentest Community also participates in Bug Bounty Programs, they are used to thinking like a real-world adversary and identifying hard-to-find vulnerabilities in your systems before criminals do. We also encourage this creativity by budgeting unstructured testing time to go alongside the time budgeted for the HackerOne pentest methodology.
Problem 3: Limited Pool of Talent
Customers are used to rotating traditional pentest vendors in order to get a fresh perspective on the assets they are testing. This is because these vendors typically don’t have a deep bench of talent, meaning the only way to get a new perspective is to bring in another vendor. However, bringing on other vendors means that the security team has to spend time getting them onboarded and reduces their focus on improving the security of their products.
Because of HackerOne’s community model, we have hundreds of pentesters on our bench. This means that our customers can rotate pentesters to get a fresh perspective, without needing to onboard another vendor. Because of the depth and breadth of talent among our pentesters, they have a broad range of experience across many different types of assets and vulnerability classes. This means that we can source the right talent for our customer’s tests in a short period of time. By leveraging experienced security researchers for pentesting, 20% of HackerOne vulnerability findings in a pentest are high or critical severity, which is roughly double the industry standard.
Problem 4: Slow Time To Results
Organizations are often frustrated with the amount of time it can take to kick off a pentesting program and receive tangible results.

The time it takes to identify and report vulnerabilities is one of the most common complaints of pentesting. Industry-standard pentests take at least two weeks after the pentest concludes to get results together and deliver them to the customer. With HackerOne’s pentests:
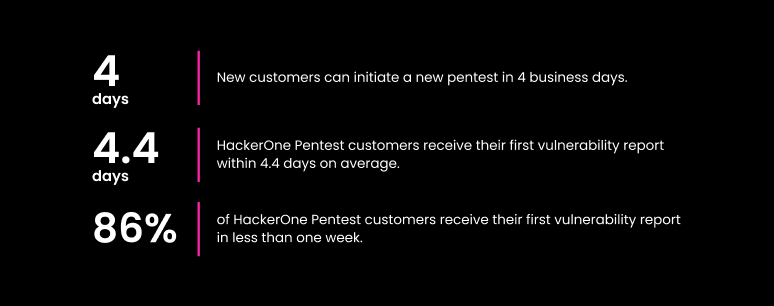
Because of our PTaaS platform, customers also receive these vulnerability findings in real time. This means that oftentimes they have remediated the vulnerability and had it retested by the time that the pentest concludes.
Problem 5: No Visibility Throughout The Process
Another consistent shortcoming of pentesting is the lack of visibility into real-time activity and results. Many organizations don’t have access to a centralized location through which to view performance and communicate with pentesters.

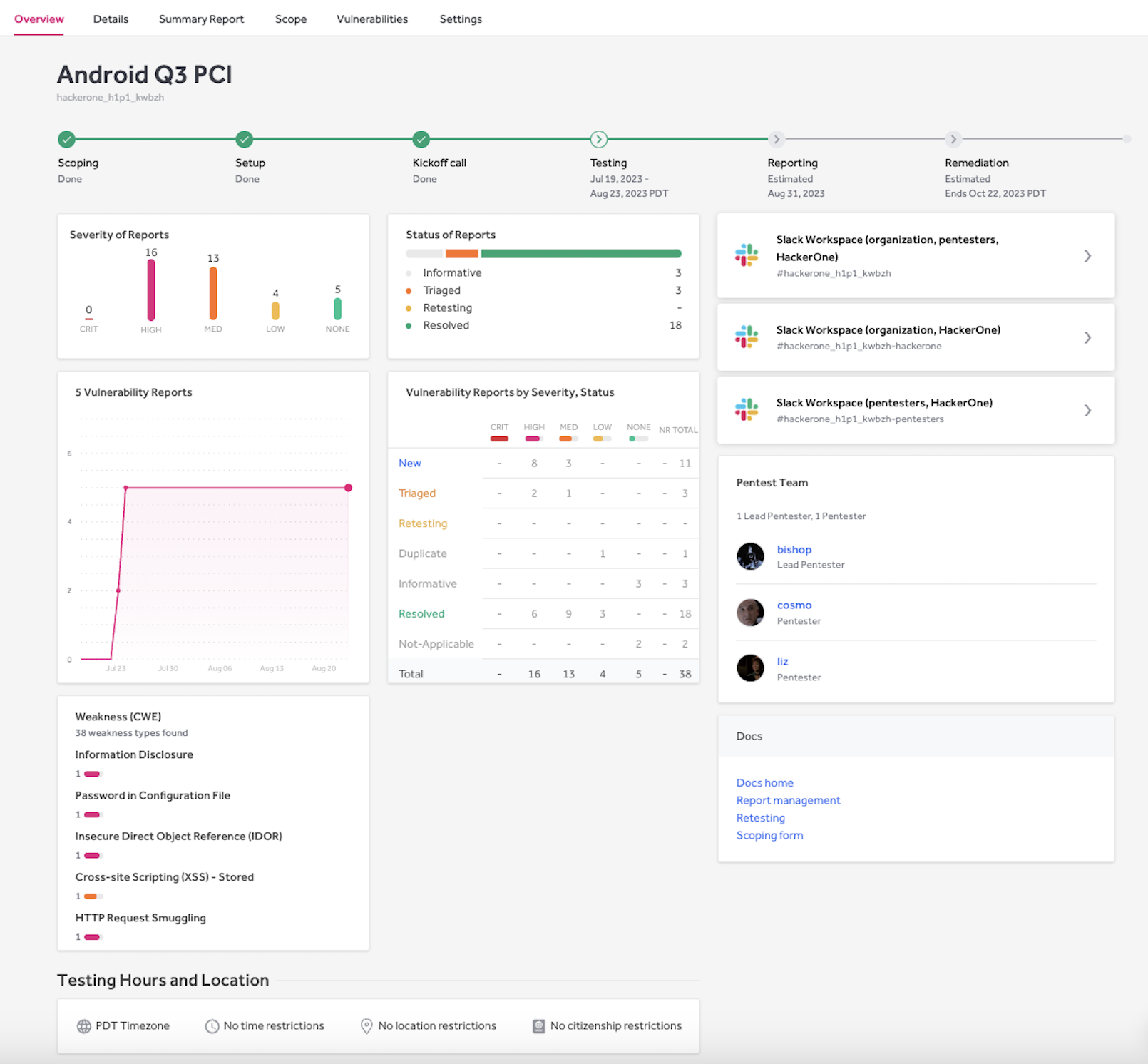
Our community of pentesters reports their findings using the HackerOne PTaaS platform. The platform gives our customers real-time visibility into the progress of each pentest, so that they understand where a pentest is at any given point in time. Customers also manage all aspects of their pentest engagements through the platform, from scoping to testing and reporting to remediation. This makes it very easy for our customers to launch a pentest quickly because it is all done out of the platform, rather than coordinated via back-and-forth emails.
Problem 6: Lack of Communication With Pentesters
A traditional pentest tends to be a black box in the sense that there is very little communication that happens throughout the test. The test kicks off and runs for a few weeks, concludes, and then a report is delivered a couple of weeks after that.
With HackerOne’s Pentest, those responsible for their organization’s pentests have a direct line of communication with both the pentesters and our Technical Engagement Managers, who manage the pentest, via Slack. You get regular status updates from your pentest team, and the open communication helps the tests run efficiently.
Problem 7: Pentesting Isn’t Integrated With Remediation
Even with a streamlined platform and communication with pentesters, the results are only as good as an organization’s ability to quickly and efficiently address vulnerabilities. This requires thoughtful integrations into ongoing tools and processes.
For organizations that want to integrate with their ticketing systems and other SDLC tools, the platform offers over 20 bidirectional, purpose-built integrations, plus APIs to add more. This helps streamline the remediation process- no more copying and pasting vulnerabilities from a PDF report in order to get them to your development team for a fix!
Combine the Convenience of PTaaS With the Power of the Pentest Community
Combining the security expertise of our pentester community with the efficiencies of our PTaaS platform reduces threat exposure across your attack surface. Perhaps most importantly, we find customers really value the direct engagement and practical knowledge that comes from working with our skilled pentesters. It energizes and educates security teams because it’s a very interactive and transparent process.
If you’d like to see how our pentesters can uplevel your pentest program or your broader security program, reach out to the team at HackerOne.
Support Techcratic
If you find value in our blend of original insights (Techcratic articles and Techs Got To Eat), up-to-date daily curated articles, and the extensive technical work required to keep everything running smoothly, consider supporting Techcratic with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to future updates and improvements. I am committed to continually enhancing the site and staying at the forefront of trends to provide the best possible experience. Your generosity and commitment are deeply appreciated. Thank you!
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending any funds to ensure your donation is directed correctly.
Bitcoin QR Code
Your contribution is vital in supporting my efforts to deliver valuable content and manage the technical aspects of the site. To donate, simply scan the QR code below. Your generosity allows me to keep providing insightful articles and maintaining the server infrastructure that supports them.

Privacy and Security Disclaimer
- No Personal Information Collected: We do not collect any personal information or transaction details when you make a donation via Bitcoin. The Bitcoin address provided is used solely for receiving donations.
- Data Privacy: We do not store or process any personal data related to your Bitcoin transactions. All transactions are processed directly through the Bitcoin network, ensuring your privacy.
- Security Measures: We utilize industry-standard security practices to protect our Bitcoin address and ensure that your donations are received securely. However, we encourage you to exercise caution and verify the address before sending funds.
- Contact Us: If you have any concerns or questions about our donation process, please contact us via the Techcratic Contact form. We are here to assist you.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.























































![Teenage Mutant Ninja Turtles – Season 3, Volume 1: Alien Invasion, Ways of the Warrior [DVD]](https://techcratic.com/wp-content/uploads/2024/11/518165SCXGL-340x180.jpg)












