alice@hackerone.com
2023-05-19 18:00:00
www.hackerone.com
There is a lot of focus, rightly so, on the consumer IoT space. We have had a lot of incidents in the past few years through connected devices with security flaws that often never received a software update. The vulnerabilities in these products stretch back many years. The people who made them — likely unknowingly — did so without designing in security. For many enterprises operating within the digital economy, speed-to-market is the primary business driver, which means that security is often considered a secondary design requirement, if at all. This might sound cynical, but many of the products that you see in online retailers are just this – re-badged white-label products from companies that you’ve never heard of at impossibly low prices. Then there are some of the big companies – often with the same types of vulnerabilities, but with more established and inherent consumer trust. Incredibly, some of the bigger names that you’ve heard of still fail to allow vulnerability reporting in a standardized way. I always say that you can think of this as the tip of the iceberg. If this is the public face of their product security, what does that say about the product itself, the bits that you can’t easily see; their engineering processes and their teams?
What About Other Sectors?
We have focussed on the consumer IoT space, but we have often wondered what it is like in other domains. Our report broke down sub-categories of products and we found variances – for example the TV industry demonstrably has got its act together. Where action has been taken, sometimes this can be traced back to specific incidents where the industry has been frightened into action, or by other factors such as influence from other domains. The adoption of Android into TVs also brings with it the experience of the smartphone industry and particularly Google’s leadership in promoting Coordinated Vulnerability Disclosure (CVD). We can point to potential influencing factors.
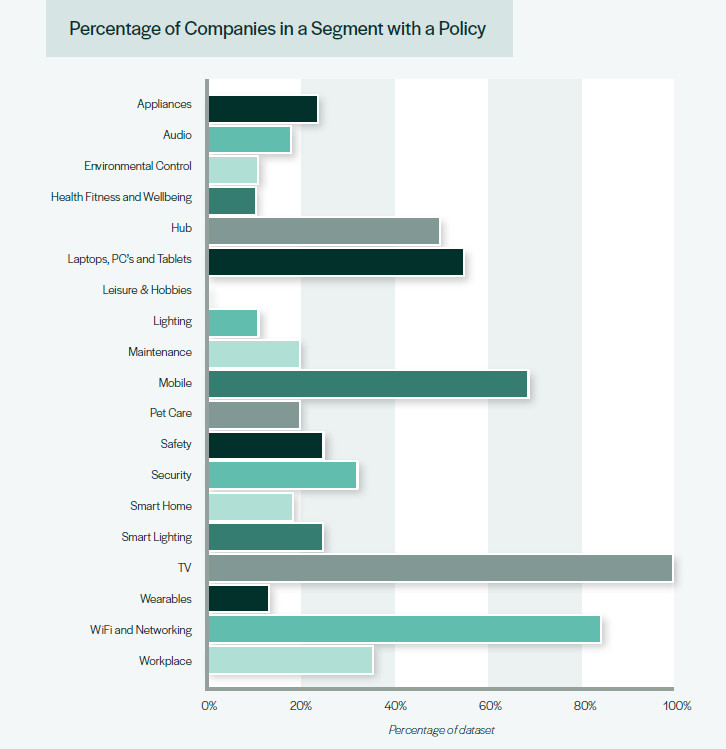
Image from the 5th annual IoT vulnerability disclosure report showing a breakdown of consumer IoT segments of companies with vulnerability disclosure policies.
Since Charlie Miller and Chris Valasek’s very public Jeep-Chrysler remote-control car hack in 2015, the automotive industry has almost been shamed into taking cyber security seriously. Prior to that, elements of the industry were amongst the most aggressive in taking down security researchers through legal threats. They’ve seen an almost Damascene conversion in terms of their approach to security. But does that apply to the entire vendor stack? There is a huge supply chain beneath the automotive OEMs and while incoming standards on cyber security are changing things, it is a big ask to expect some of these companies to change the things that they have been doing in the same old way for many decades. With cyber security skills at a premium, can these companies afford to hire the right people even if they can find them?
Many of the same technologies appear in other sectors – for example mining vehicles all run with the same insecure CANbus architectures that we’ve seen exploited in cars. CANbus appears all over the place – in the agriculture sector, industrial equipment, yachts and even in space. All of these different sectors have huge supply chains of their own and they’re all using broadly the same technologies as everyone else – the same chipsets, the same or even older, legacy operating systems. They suffer the same issues – lack of secure-by-default configurations, default passwords and almost zero implementation of secure coding.
So, what do we think the results would look like if we looked at these sectors? Any different to the 72.89% of the consumer IoT industry that has no form vulnerability disclosure policy?
For full insights , download the fifth annual report into the State of Vulnerability Disclosure Policy (VDP) Usage in Global Consumer IoT in 2022
Support Techcratic
If you find value in our blend of original insights (Techcratic articles and Techs Got To Eat), up-to-date daily curated articles, and the extensive technical work required to keep everything running smoothly, consider supporting Techcratic with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to future updates and improvements. I am committed to continually enhancing the site and staying at the forefront of trends to provide the best possible experience. Your generosity and commitment are deeply appreciated. Thank you!
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending any funds to ensure your donation is directed correctly.
Bitcoin QR Code
Your contribution is vital in supporting my efforts to deliver valuable content and manage the technical aspects of the site. To donate, simply scan the QR code below. Your generosity allows me to keep providing insightful articles and maintaining the server infrastructure that supports them.

Privacy and Security Disclaimer
- No Personal Information Collected: We do not collect any personal information or transaction details when you make a donation via Bitcoin. The Bitcoin address provided is used solely for receiving donations.
- Data Privacy: We do not store or process any personal data related to your Bitcoin transactions. All transactions are processed directly through the Bitcoin network, ensuring your privacy.
- Security Measures: We utilize industry-standard security practices to protect our Bitcoin address and ensure that your donations are received securely. However, we encourage you to exercise caution and verify the address before sending funds.
- Contact Us: If you have any concerns or questions about our donation process, please contact us via the Techcratic Contact form. We are here to assist you.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.














































![2024 Upgrade Tesla Model Y Sunshade Roof [Never Sag, No Gaps, Nano Ice-Crystal Coatings]…](https://techcratic.com/wp-content/uploads/2024/11/61USyoncEvL._AC_SL1500_-360x180.jpg)










![Japanese Movie – The X From Outer Space (Uchu Dai Kaijyu Girara) [Japan BD] SHBR-263](https://techcratic.com/wp-content/uploads/2024/11/81rV3BDVGJL._SL1024_-360x180.jpg)









