Waqas
2024-08-31 08:53:00
hackread.com
The Voldemort Malware campaign is spreading globally with over 20,000 phishing emails sent to more than 70 organizations, with a peak of 6,000 emails sent in a single day.
A newly identified malware campaign, dubbed “Voldemort,” has been spreading stealthily across the globe, targeting organizations in various sectors including insurance, aerospace, transportation, and education.
The campaign, which began on August 5, 2024, has already sent over 20,000 phishing emails to more than 70 organizations, with a peak of 6,000 emails sent in a single day. The malicious activity is thought to be part of a sophisticated cyber espionage effort, according to a recent report by Proofpoint.
A Sophisticated Attack Chain
The Voldemort campaign employs a complex attack chain, combining both common and unusual techniques. One of the most notable aspects is the use of Google Sheets for command and control (C2) operations—an uncommon method that highlights the creativity of the threat actors.
Attack Overview:
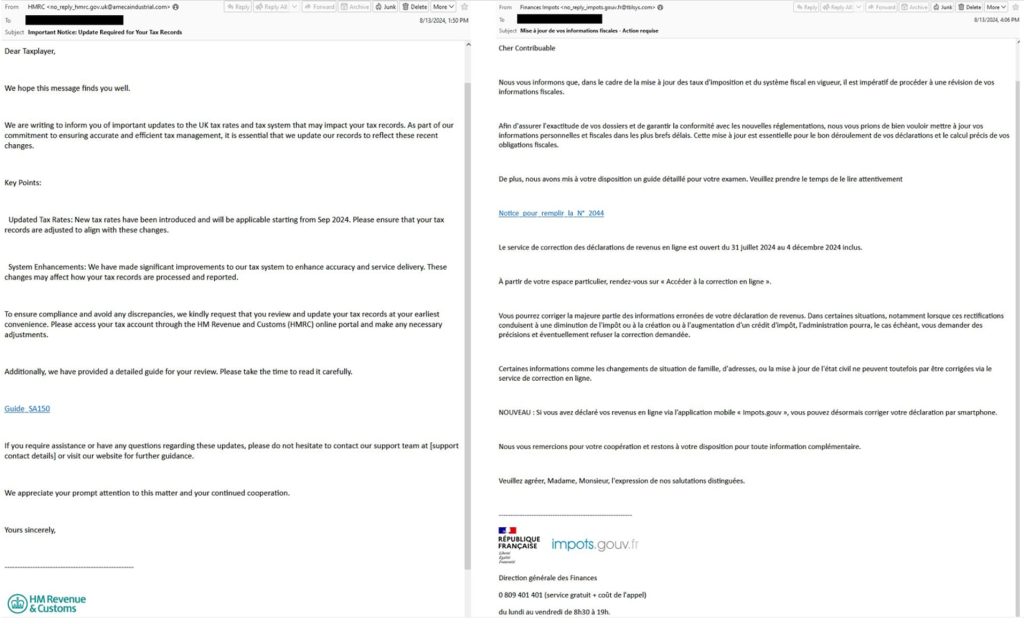
According to Proofpoint’s technical blog post shared with Hackread.com ahead of publishing, the attack campaign begins with phishing emails that seem to originate from legitimate tax agencies. These emails contain links directing the recipient to a landing page hosted on InfinityFree or directly to a malicious file.
When victims click the “View Document” button on the landing page, the browser’s User Agent is checked. If the system is identified as Windows, the user is redirected to a search-ms URI, which silently prompts Windows Explorer to display a shortcut (LNK) file or a ZIP file disguised as a PDF.
If the victim executes the LNK file, it triggers a series of actions leading to the deployment of the Voldemort malware. This malware is capable of collecting system information, uploading files, and executing additional commands from a command-and-control (C2) server.
Unusual Techniques with Cybercrime Vibes
While the campaign’s characteristics suggest a focus on cyber espionage, some tactics are more commonly associated with cybercriminal activity. For instance, the abuse of Windows search protocols (search-ms) to deploy remote access trojans (RATs) is a technique increasingly seen in cybercrime.
Additionally, the campaign’s use of Cloudflare Tunnels—specifically the TryCloudflare feature—enables the threat actors to create one-time tunnels without needing an account, adding another layer of anonymity and making detection more challenging.
The Voldemort Backdoor
Voldemort is a custom backdoor written in C, featuring advanced capabilities for information gathering. It leverages CiscoCollabHost.exe, a legitimate executable vulnerable to DLL hijacking, to load the malicious DLL. The malware then communicates with its C2 server using Google Sheets, where it can execute commands such as downloading files, executing programs, and more.
The malware also employs a unique string decryption method and dynamically invokes APIs, techniques often seen in more sophisticated threats like Cobalt Strike.
Attribution: A Mystery
So far, Proofpoint has not been able to attribute this campaign to any known threat actor with high confidence. The mix of advanced espionage techniques and more common cybercrime tactics complicates the attribution process. The large scale of the campaign, combined with the high level of customization in the malware, suggests that it could be the work of an advanced persistent threat (APT) group.
Commenting on this, Mr. Mayuresh Dani, Manager, Security Research, at Qualys Threat Research Unit advised organisations worldwide to implement proper security measures to tackle Voldemort malware and other such threats.
“Organizations should take reactive and proactive means of protecting employee data starting with implementing spam filters – with strict settings for certain users at risk. AI and LLMs’ spam and language filters should be employed for first time email senders from unknown/untrusted domain names,” Mayuresh said.
“They should also enforce user education that will help weed out any spurious emails that are eventually delivered. As a reactive means, they should monitor leaks sources for key resources in the company and have them scrubbed,” he advised.
Why It Matters
The Voldemort malware campaign uses mixed techniques, making it difficult to differentiate between cybercrime and espionage. The campaign’s ability to evade detection using unconventional C2 methods like Google Sheets, its global reach, and high-profile targets show that cybercriminals will always be a step ahead unless users master the basics of cybersecurity to protect themselves.
RELATED TOPICS
- Unicode QR Code Phishing Scam Bypasses Traditional Security
- Facebook, Meta, Apple, Amazon Most Impersonated in Phishing
- Hackers Sent 927,000 Phishing Emails with Malicious OAuth Apps
- Phishing Attacks Target East European Bank Users on iOS, Android
- Nespresso Domain Hijacked in Phishing, Targeting Microsoft Logins
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.












































![2024 Upgrade Tesla Model Y Sunshade Roof [Never Sag, No Gaps, Nano Ice-Crystal Coatings]…](https://techcratic.com/wp-content/uploads/2024/11/61USyoncEvL._AC_SL1500_-360x180.jpg)











![Japanese Movie – The X From Outer Space (Uchu Dai Kaijyu Girara) [Japan BD] SHBR-263](https://techcratic.com/wp-content/uploads/2024/11/81rV3BDVGJL._SL1024_-360x180.jpg)