Waqas
2024-09-02 12:51:31
hackread.com
Tracelo, a smartphone geolocation tracker service, was breached on September 1, 2024, exposing data from both its customers and the individuals targeted by those customers.
A hacker using the alias “Satanic” claims to have breached Tracelo, a smartphone geolocation tracking service. As a result, the hacker has leaked the personal details of over 1.4 million individuals (1,459,014) on the notorious Breach Forums.

What is Tracelo?
Although a relatively new service, Tracelo claims to offer a service that can determine a person’s location using just their phone number, presenting itself as a tool for finding family members or other individuals with an emphasis on ethical practices.
However, while Tracelo states that it operates entirely online and remotely, with no need for app installations and only requires a phone number, the lack of transparency about how consent is verified raises privacy concerns.
The company insists that tracking is done responsibly, requiring explicit prior consent from the person being tracked, but critics might argue that simply sending an SMS for consent could be easily bypassed or misunderstood by users.
Moreover, Tracelo’s assurances of legality and alignment with the Information Commissioner’s Office recommendations may not fully address possible misuse, especially given that location tracking is a sensitive issue involving personal privacy and data security.
The Breach
The breach occurred on September 1, 2024. According to analysis by the Hackread.com research team, the hacker managed to extract 264 MB of data, including three CSV files: one named “saas-backend.locate_phone_infos,” another named “saas-backend.users,” and a third named “saas-stage.users.” Below is an in-depth file-by-file analysis of the leaked records:
SaaS-backend.locate_phone_infos
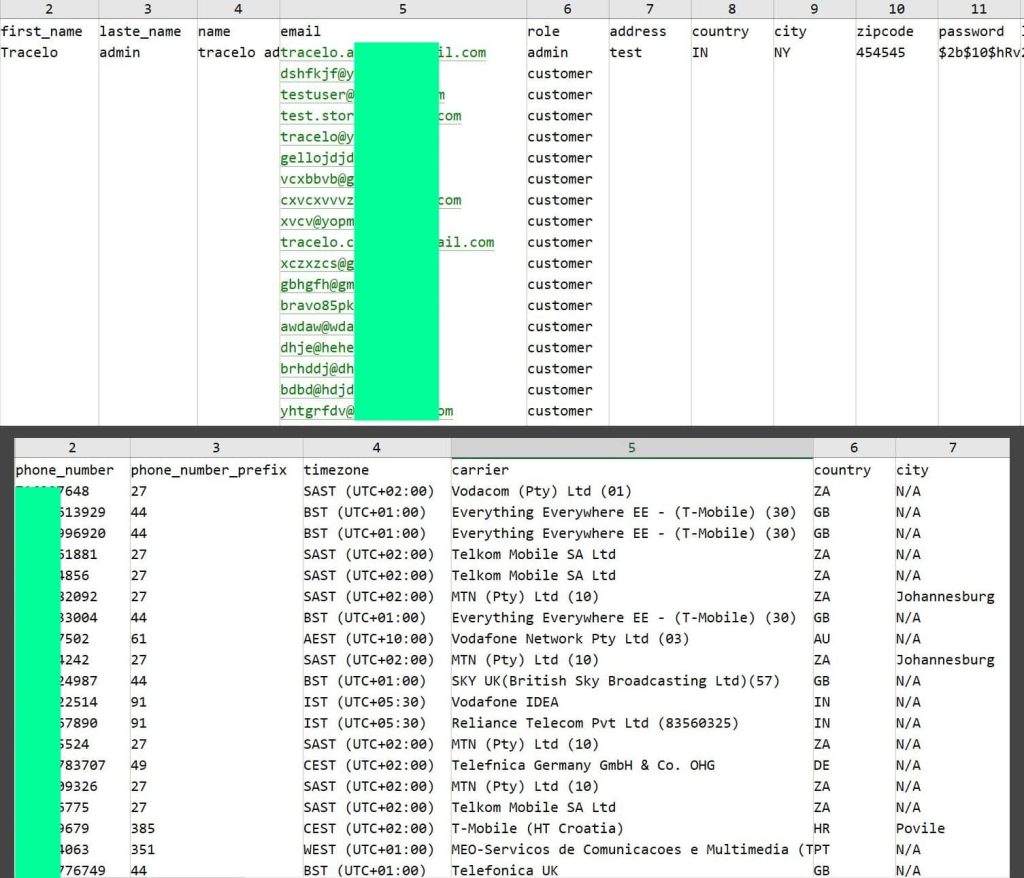
The “saas-backend.locate_phone_infos” file appears to contain the personal details of over half a million (646,442) victims worldwide, suggesting that these individuals had their locations allegedly traced. Here’s what the details contain:
- Full names
- Phone carriers
- Phone numbers
- Country, city and timezone
- A unique identifier for each record
and more…
It is important to note that Hackread.com did not find any evidence of location data being included in the information leaked during this breach.
Saas-backend.users
The file Saas-backend.users, contains personal details of almost a million (803,103) individuals/customers who registered accounts on Tracelo. This includes the following information:
- Full names
- Physical addresses
- Bcrypt password hashes
- Email addresses (803,013)
- Last login date
- Subscription type
- Google ID numbers
- Country, city and zipcodes
and more…
Saas-stage.users
The file “saas-backend.users” contains the personal details of almost a million (803,103) individuals who registered accounts on Tracelo. This data includes the following information:
- Email addresses (9,853)
- Subscription type
- Account creation date
- Bcrypt password hashes
and more…
The Irony
Hackread.com has reached out to Tracelo for comment, but ironically, this breach involves the leak of customers’ physical data. While users sought to track the location of others, the leak does not include location data of the targeted individuals but instead exposes data about the customers themselves.
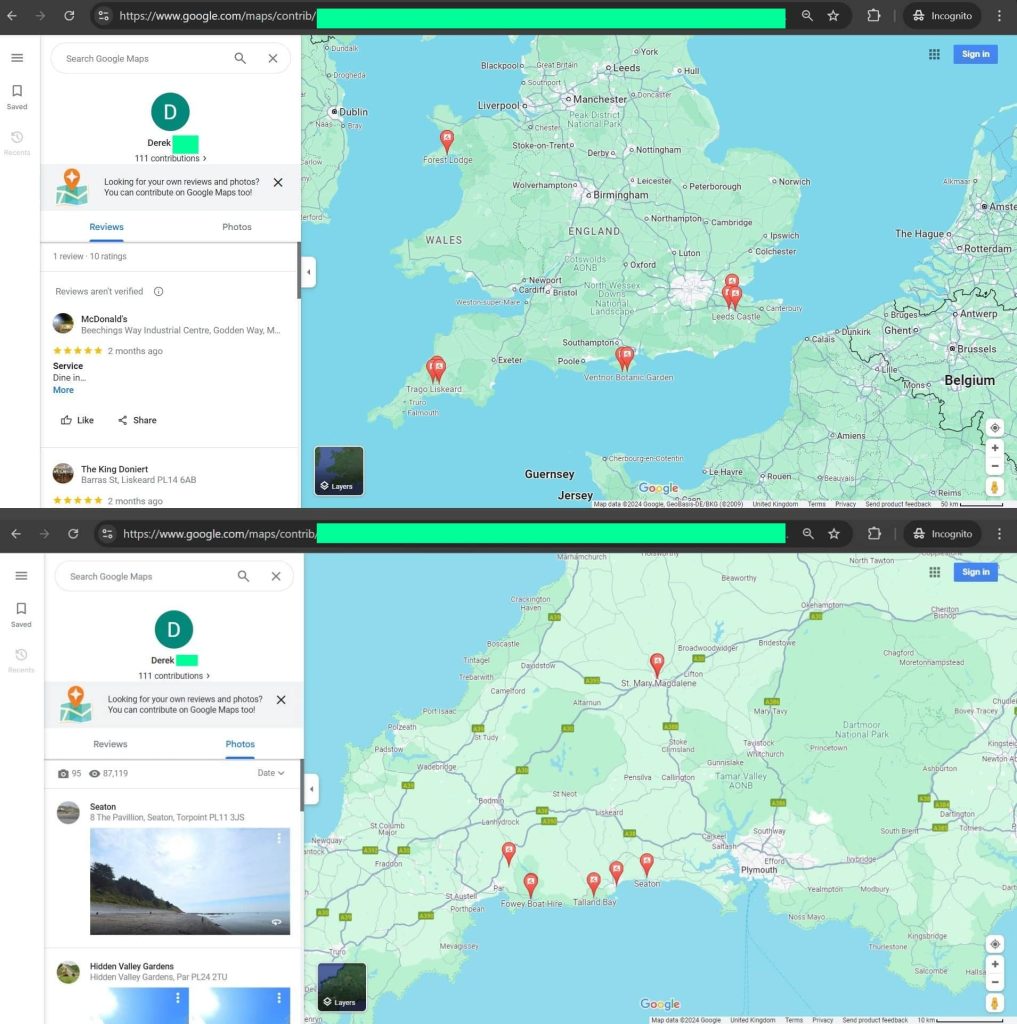
For example, the file “saas-backend.users” contains physical addresses for some customers and Google ID numbers for 619,979 individuals. A Google ID number can be used to track a person’s approximate geolocation, recent visits, frequently visited places, restaurants they go to, their feedback/reviews, and even photos they have uploaded to Google. Here’s one example of how I managed to track a Tracelo customer using their Google ID:
Watch out for phishing and vishing scams
With phone numbers and email addresses exposed in the Tracelo data breach, affected individuals should be alert against potential phishing and vishing scams (voice phishing). Cybercriminals often use this type of personal information to craft convincing fraudulent messages, posing as trusted entities to steal further sensitive information or financial data.
Additionally, Users should be cautious of unexpected emails or calls requesting personal details, passwords, or financial information. It is advised to verify the legitimacy of any communications before responding and to report suspicious activity to relevant authorities to prevent falling victim to these scams.
RELATED TOPICS
- LetMeSpy Android Spyware Service Shuts Down After Data Breach
- Ex-employee stole Israeli spyware firm NSO Group Secrets for deals
- Family Location Tracker App Life360 Breach: 443K Users’ Data Leaked
- Location Tracker Firm ‘Tile’ Data Breach: Hackers Access Internal Tools
- Parental control spyware app Family Orbit hacked; 281GB of data exposed
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.
























































![Japanese Movie – The X From Outer Space (Uchu Dai Kaijyu Girara) [Japan BD] SHBR-263](https://techcratic.com/wp-content/uploads/2024/11/81rV3BDVGJL._SL1024_-360x180.jpg)