HackerOne
2021-08-25 08:50:00
www.hackerone.com
How Can You Use the Integration?
This new integration reduces the manual processes of comparing and taking action on vulnerability findings between the two platforms with workflow automation. AWS customers can use the integration to:
- Aggregate and prioritize vulnerabilities from HackerOne in Security Hub: Sync all HackerOne vulnerability findings and use AWS Security Hub as the single console to manage and prioritize those findings.
- Forward findings from Security Hub and other partners to HackerOne: Compare AWS Security Hub findings with those found in reports from HackerOne to see duplicates and finding status.
The HackerOne community of ethical hackers finds vulnerabilities, generates reports, and triages all findings to reduce time to remediation and lockdown exploitable vectors. Once HackerOne has validated and prioritized a vulnerability report, customers using the AWS Security Hub and HackerOne integration will receive new vulnerabilities findings via a continuous workflow, as shown in Figure 1 below.
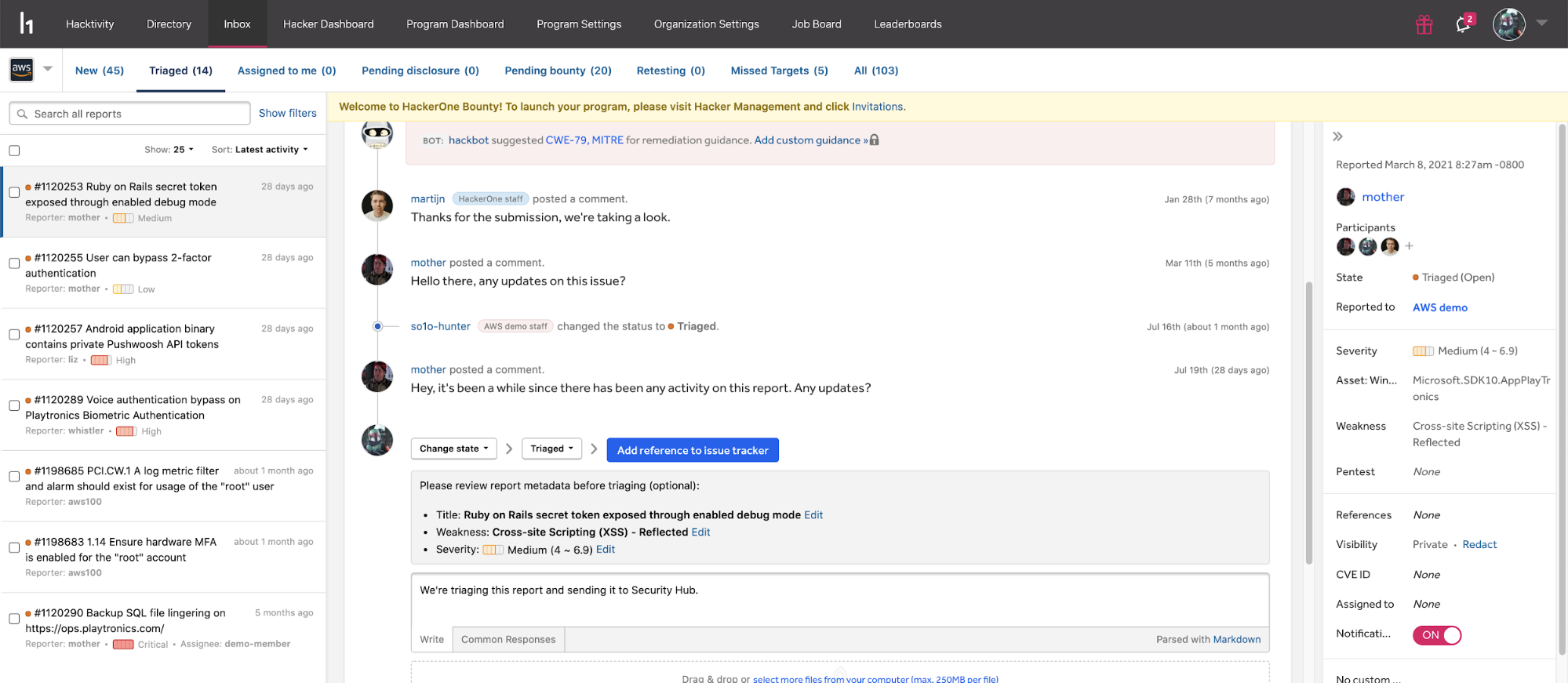
The integration will automatically push HackerOne reports to AWS Security Hub. The findings in AWS Security Hub will show severity, status, description, and more to provide security teams the context needed to make informed decisions.
Teams can compare Security Hub’s findings with reports from HackerOne to identify and remove duplicates without going back and forth between multiple consoles, as shown in Figure 2 below.
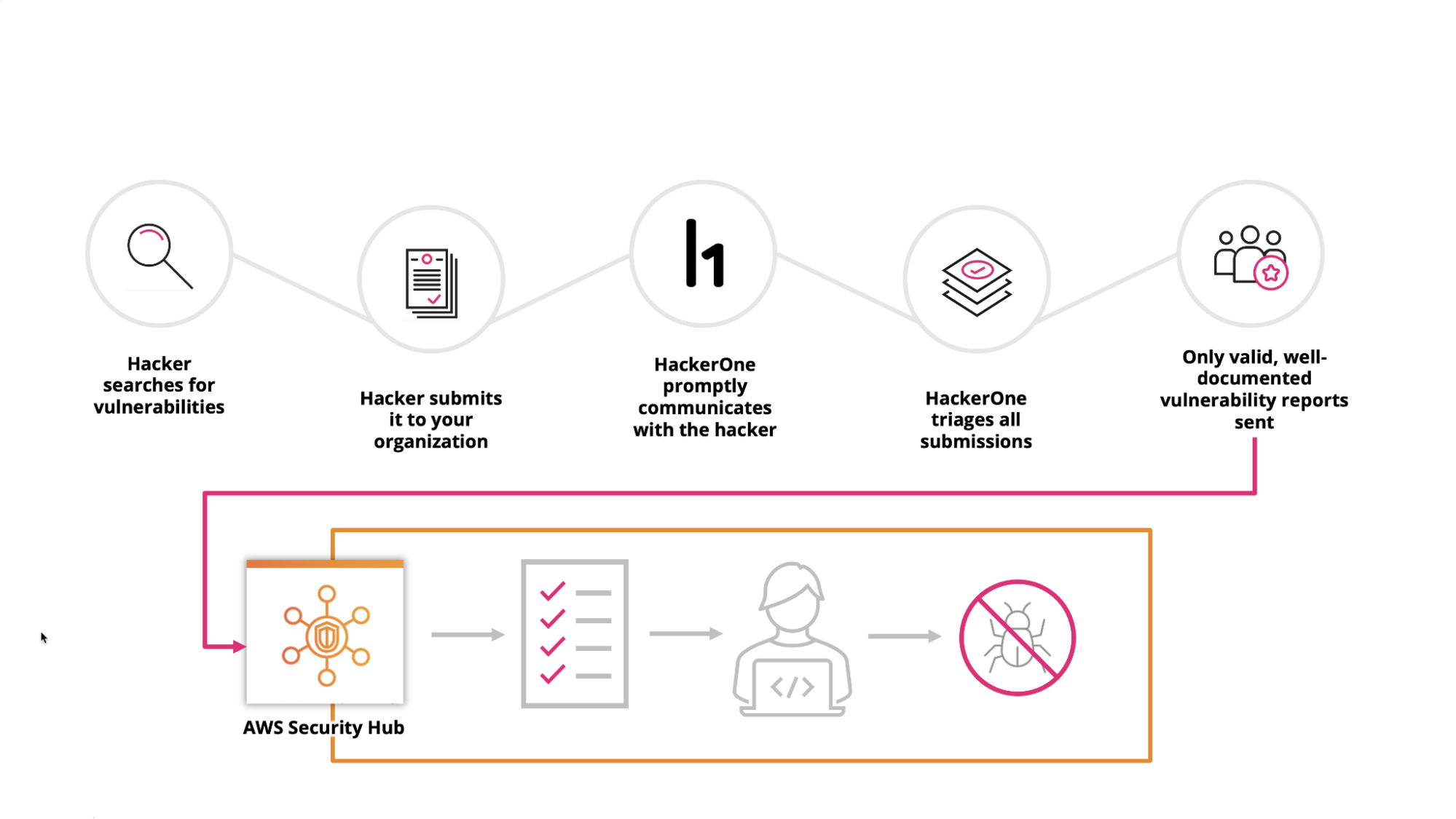
Report resolution status originating in HackerOne, but presented in Security Hub, is automatically updated in Security Hub, avoiding the need to manually verify the resolution in a separate action, as shown in Figure 3 below.
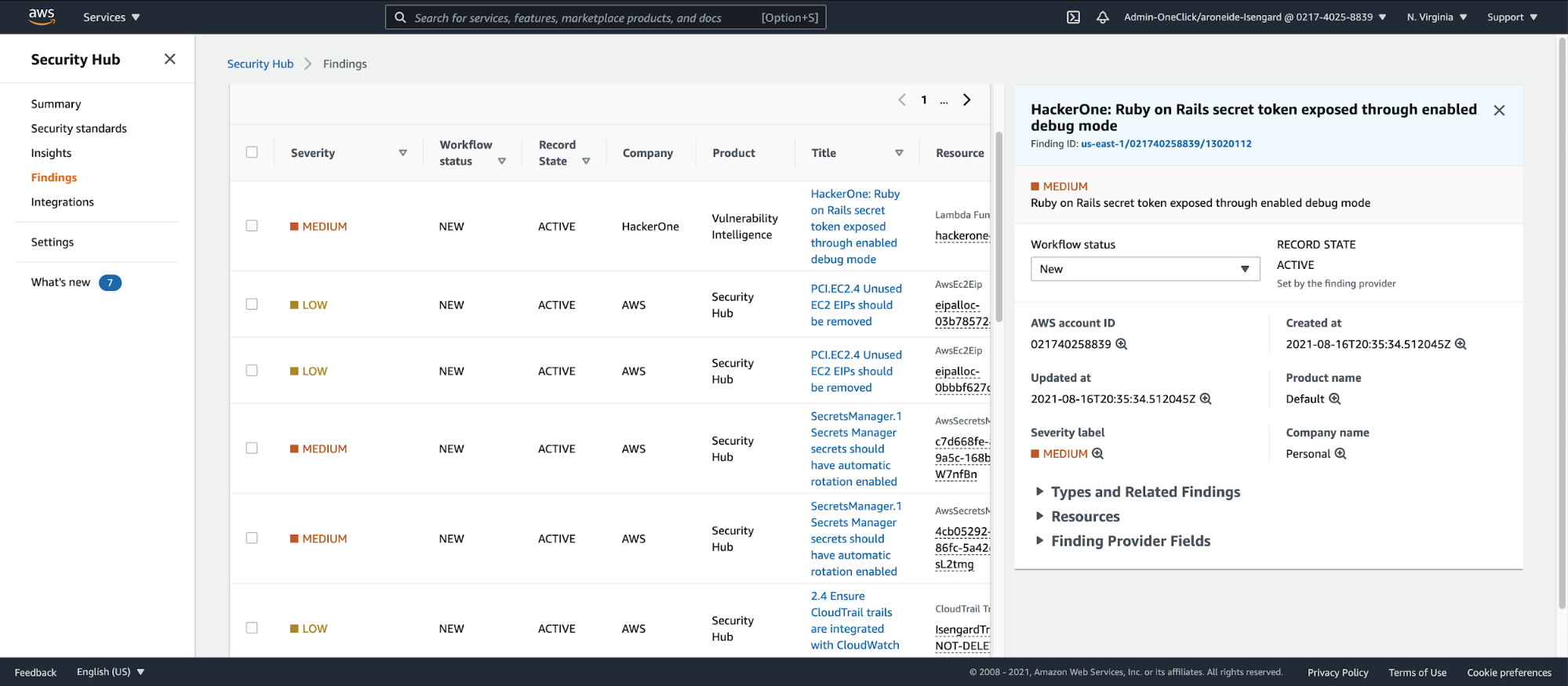
In addition, any change made to a Security Hub report will trigger an event that syncs all changes back to HackerOne, eliminating errors and saving time.
Security Hub can also forward findings to HackerOne, allowing customers to use the HackerOne platform to centrally manage both Security Hub findings and the vulnerabilities found by the HackerOne community. To provide additional context to the analysts using HackerOne, customers can click on the “Send to HackerOne” button in the Security Hub interface, as seen below in Figure 4.
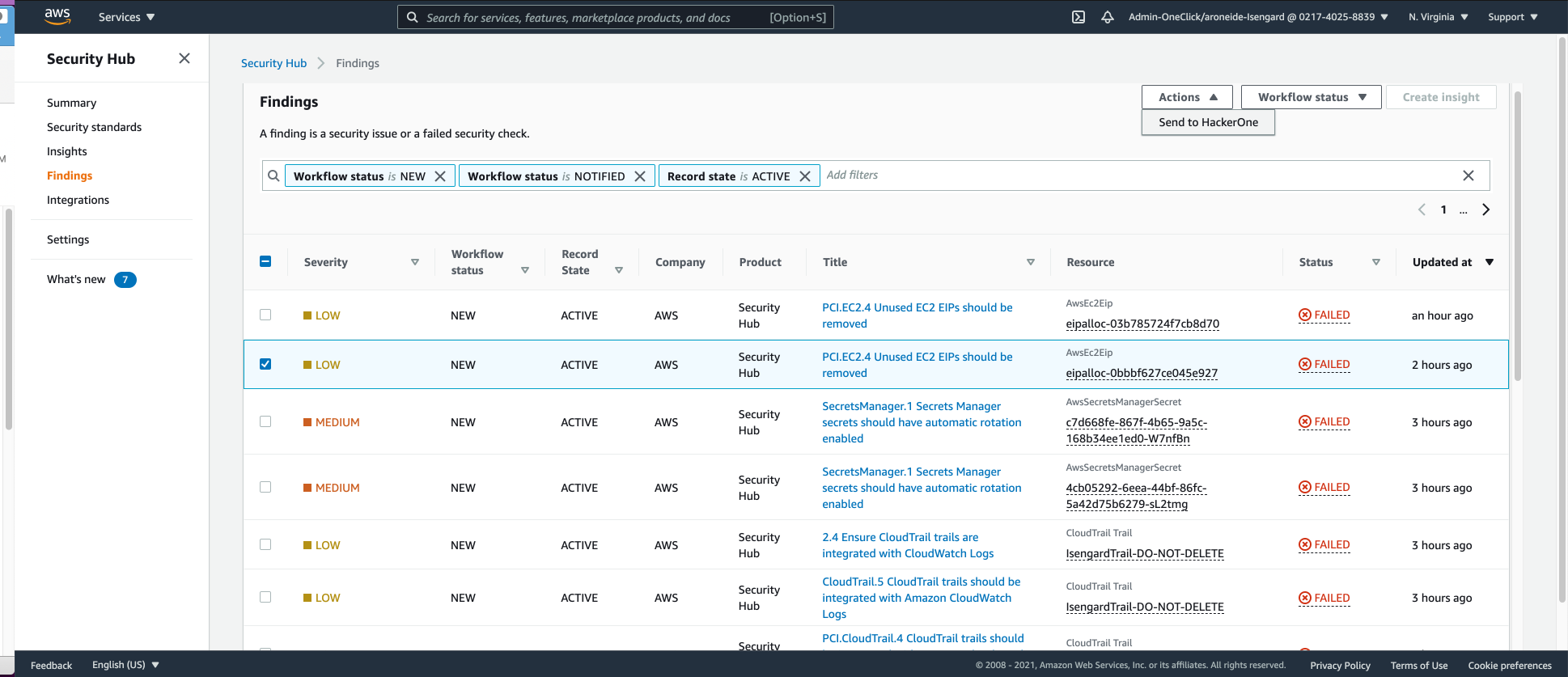
Once synced, customers can use the HackerOne platform to manage the finding workflow. They can filter synced Security Hub reports via the HackerOne Inbox, then triage, escalate, and resolve issues. Finally, they can request retests to validate fixes, ensuring proper resolution of issues.
The workflow integration between HackerOne and AWS Security Hub is easy to configure and ensures vulnerability findings reach the right people at the right time with the right status. Security teams need workflows that save time, improve efficiencies, and ultimately mitigate risk. Automating the workflows around hacker-powered vulnerability intelligence in AWS Security Hub helps security teams become more efficient. To learn more about HackerOne and AWS Security Hub together, visit the HackerOne and AWS page.
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.
























































![Japanese Movie – The X From Outer Space (Uchu Dai Kaijyu Girara) [Japan BD] SHBR-263](https://techcratic.com/wp-content/uploads/2024/11/81rV3BDVGJL._SL1024_-360x180.jpg)










