johnk
2019-12-13 18:30:00
www.hackerone.com
It’s that time of the year again. Time to dig out your wrinkled “No, I can’t fix your computer” t-shirt from the bottom of the drawer. You can avoid Uncle John’s curiosity about the best free antivirus software — but you can’t avoid the holiday increase in vulnerability reports.

Running the largest hacker-powered security platform for the better part of ten years, and more than 120,000 vulnerabilities, has its advantages. Prominent among them is…data! And who among us doesn’t love a little holiday security data story?
So, grab your favorite Star Wars blanket, find a nice spot by the (Kindle) fire, and lets unwrap a few gifts of data-driven insight a little early this year, shall we?
During the last two holiday seasons, HackerOne observes the following security trends:
- An increase in overall vulnerability reports during the two weeks after Thanksgiving
- During Thanksgiving week, clients in the internet and online services industry in particular saw a higher volume of reports
- We also found a surge in Cross-site Scripting (XSS) weakness types in the week after Thanksgiving
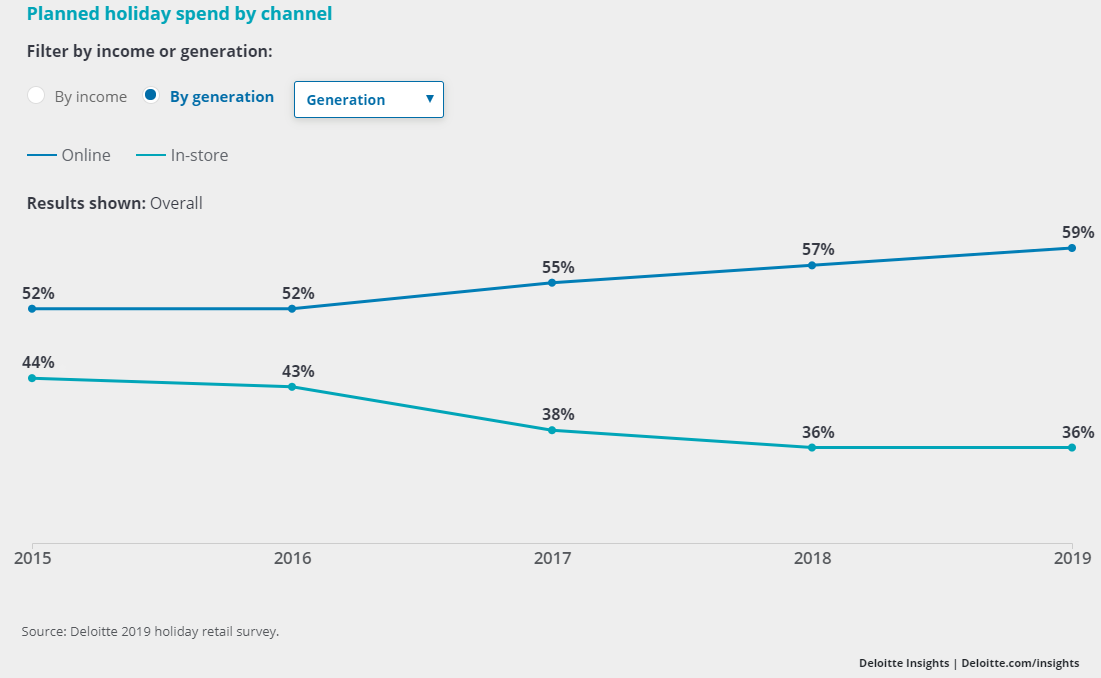
All three of these observations make sense when one considers the mega trend towards online shopping, which the good folks at Deloitte track nicely in their Annual Holiday Retail Survey As the following chart shows, across all age groups, the consultancy expects online shopping to hit 59% of total this year, and Millennials will do shopping mall decimating 64% of their shopping online.
Cross-Site Scripting (XSS) actually topped the recent HackerOne analysis of the 10 Most Impactful and Rewarded Vulnerability Types. Across all industries, HackerOne customers paid out 27.9 percent of total bounties for XSS reports.
Like the black sheep of the family, XSS really gets in your face during the holidays. Attackers can use XSS to send a malicious script to an unsuspecting user. The end user’s browser has no way to know that the script should not be trusted, and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. These scripts can even rewrite the content of the HTML page.
Fortunately, HackerOne’s international community of friendly hackers is adept at finding the vulnerability. For example, in March of this year, a hacker demonstrated a vulnerability on a leading payment services site. The hacker showed the company’s security team the ability to use request smuggling to convert a page request into a cached redirect. If the cached redirect were accessed by a legitimate user, an attacker’s content would be rendered instead of the requested page. While this would not impact any back-end data, this could interfere with the integrity of certain pages, including potential interference with the sign-in page. Thanks to the hacker’s ingenuity, this bug was found and fixed before any shoppers were harmed.
Why not make one of your New Year Resolutions to put a HackerOne Bounty program in place? Then, when the holidays roll around next year, you’ll have a kicking new comeback for cousin Pete’s request for computer help — “Did you shop online this year? Well, I made that safer for you.”
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support Innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.



































































