Deeba Ahmed
2024-09-30 09:58:43
hackread.com
Darktrace AI detected and stopped a thread hijacking attack in real-time, preventing email account compromise and data theft. The attack involved a hidden email rule diverting messages from the intended recipient.
Cybersecurity experts have observed a rise in thread hijacking attacks, which criminals use to infiltrate email conversations and steal sensitive data. This technique is particularly stealthy due to its near-invisibility to conventional security measures and human detection.
In thread hijacking attackers gain access to a user’s email account, monitor conversations, and infiltrate conversations between individuals or organizations, exploiting trust within these threads.
In a recent incident, Darktrace’s AI technology detected and halted a thread hijacking attack in real-time, targeting a major company. The attack vector in this case is an email sent to a SaaS (Software-as-a-Service) user hours before a new email rule was created, allegedly a reply to a previous email regarding tax and payment details, which Darktrace AI detected as anomalous. The hidden email rule was created to divert specific messages away from the intended recipient.
Attack Details
According to Darktrace’s blog post shared with Hackread.com ahead of publishing on Monday, a user’s email account was compromised by an attacker possibly through phishing, malware, or exploiting weak passwords. They monitored the user’s email threads looking for exploitable ongoing conversations and then inserted themselves into conversations by replying to existing emails. Because the email appeared to come from a trusted source within an ongoing thread, it bypassed many traditional security filters and raised less suspicion.
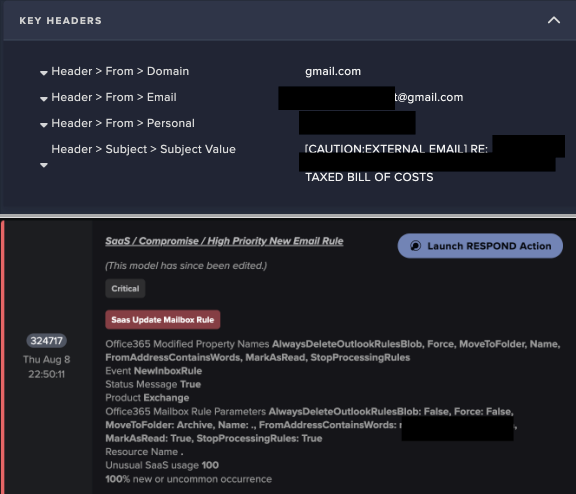
The attacker created a new mailbox rule to forward emails to an archive folder, making it harder for the customer to notice the malicious activity. Using the trust established in the conversation, the attacker attempted to manipulate the user into clicking on malicious links or providing sensitive information.
“This evasion technique is typically used to move any malicious emails or responses to a rarely opened folder, ensuring that the genuine account holder does not see replies to phishing emails or other malicious messages sent by attackers.”
Darktrace
Darktrace’s Response
Darktrace’s Self-Learning AI detected the anomaly on August 8, 2024, which was a suspiciously named “.” mailbox rule. Darktrace’s RESPOND tool took immediate action by disabling the compromised SaaS user for 24 hours, preventing further escalation of the attack.
Additionally, a Proactive Threat Notification was sent to the Darktrace SOC team, allowing them to investigate the incident and inform the customer. Overall, the incident highlights the importance of advanced threat detection and response tools like Darktrace to protect organizations from sophisticated cyberattacks like thread hijacking.
RELATED TOPICS
- How AI is Tightening Cybersecurity for Businesses
- LockBit 3.0 Posts Dubious Claims of Breaching Darktrace
- IT and Cybersecurity Jobs in the Age of Emerging AI Technologies
- Email Hacking Reigns as Top Cybersecurity Threat, Indusface Study
- The Future of Phishing Email Training for Employees in Cybersecurity
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support Innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.

















































![for 2024 Tesla Model 3 Highland Screen Protector [Anti-glare] 15″ Touchscreen & 8″ Rear…](https://techcratic.com/wp-content/uploads/2024/11/71WUBhnbTQL._AC_SL1500_-360x180.jpg)







![Colony: Season One [DVD]](https://techcratic.com/wp-content/uploads/2024/11/91fkO93oDFL._SL1500_-360x180.jpg)










