HackerOne
2016-10-05 23:46:00
www.hackerone.com
There’s been a severe lack of severity in your vulnerability reports… so we’re happy to announce the launch of report severity! Starting today, you’ll be able to assign a severity to every report on HackerOne. How does it work, you ask?
As a hacker, when first submitting your report, you’ll be able to simply choose an estimated severity for the report of Low, Medium, High, or Critical:

Severity can be somewhat subjective, so if you’d like to be a bit more data driven, we’ve added a CVSS 3.0 calculator. Using the calculator, you can specify various factors that will automatically calculate a severity for you based on the CVSS (Common Vulnerability Scoring System) standard. CVSS is a widely accepted standard used by many organizations to assess the severity of a vulnerability. Some examples of vulnerabilities and how they can be assessed via this standard are available here. Note – filling out CVSS is optional!
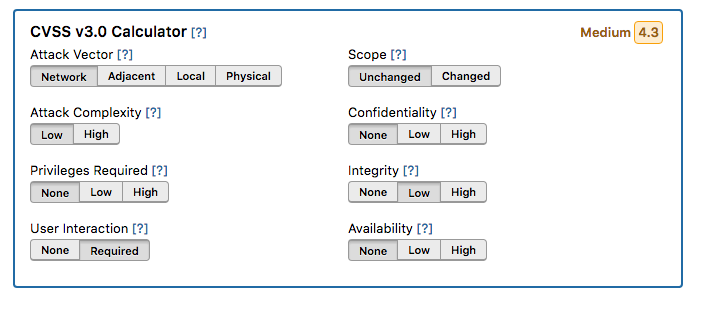
As a security team, when you receive reports with a severity, you will have the option to adjust the severity. If you do adjust the severity, we highly recommend explaining the rationale for changing the severity in a comment on the report. The CVSS calculator is also provided if you’d like to add more detail behind the severity assessment (again, totally optional).
So how can severity be used?
As a security team, there are many ways you can leverage the new report severity functionality.
Using severity to promote transparency with hackers
You can update your policy/rules page to indicate what types of issues fall into which severity, to provide more transparency to hackers participating in your program.
More specifically, your Security Page can define the CVSS Impact metrics you care about: Confidentiality, Integrity, and Availability.
- Confidentiality – Is there information that you consider particularly confidential?
- Integrity – Where is the integrity of your data critical to your business?
- Availability – Are there certain systems that require high availability?
Inversely, you can also describe which impact you care least about – for example, perhaps any vulnerability in a low traffic, third-party marketing website without any sensitive content might always be considered “Low” severity, regardless of the CVSS score.
Overall, using severity can help indicate to hackers which vulnerabilities on which properties you care the most about. This helps set expectations with hackers, enabling them to spend their time efficiently on the areas which are most important to you. We recommend adding a section to your policy with specific examples of what you consider to be “Low,” “Medium,” “High,” and “Critical” severity.
Using severity to help determine bounty amounts
Speaking of getting results in the areas that you want… you can even structure your bounty pricing around severity by offering minimums or ranges of typical bounties for “Low,” “Medium,” “High,” and “Critical” severity. If you go this route, it’s very important to spend some time, per above, fleshing out the criteria for what issues fall into what severities. This will set expectations appropriately around what types of bounties can be achieved based on your severity criteria.
Using severity to inform your internal Service Level Agreements (SLAs)
Depending on what severity scale you use internally, you can also tie this into your triage and vulnerability management processes. You can prioritize triage of “Critical” and “High” vulnerabilities, and use this severity as a common nomenclature for communicating ideal remediation timelines based on severity. In speaking with your development teams, should “Critical” vulnerabilities be fixed within a week? A few days?
Wrapping it up
Overall, report severity opens up a lot of doors for better interactions between hackers and security teams, as well as helps provide more data for vulnerability management. We’re excited to see how everyone in the HackerOne community will use this new functionality, and we’d love your feedback on what you love about it, as well as any ideas you have around it! Please let us know what you think at feedback@hackerone.com, or on Twitter – @hacker0x01.
- Sonya Juang, Peiying Wen, and the whole HackerOne team.
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support Innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.




































![Lost Lands 8: Sand Captivity CE [32] Let's Play walkthrough – Part 32](https://techcratic.com/wp-content/uploads/2024/11/1731477236_maxresdefault-360x180.jpg)


















![Teenage Mutant Ninja Turtles – Season 3, Volume 1: Alien Invasion, Ways of the Warrior [DVD]](https://techcratic.com/wp-content/uploads/2024/11/518165SCXGL-340x180.jpg)











