HackerOne
2015-04-14 09:41:00
www.hackerone.com
Research Highlights
HackerOne has been working with economics and policy researchers from MIT and Harvard to study the economic forces behind the 0day market. Here’s what we found:
- The vulnerability market is not controlled by price alone — many levers exist that tip the scales between offense and defense.
- Bug bounties are still effective to help find vulnerabilities faster, especially for less mature software.
- Creating incentives for tools and techniques that support vulnerability discovery is a more efficient way for defenders to drain the offense stockpile of 0day vulnerabilities.
Find this surprising? Want to know how to compete as a defender in a market not entirely defined by price? Read on.
Software vulnerabilities have been traded for thanks, tshirts, and more recently for cold hard cash.
When a popular product is launched, a high-stakes race begins between the offense and defense markets to find software vulnerabilities. In this case, “offense” and “defense” refer to how the vulnerability is intended to be used once it is found. More and more organizations are seeing that incenting security research with programs like bug bounties are an effective way to find vulnerabilities in any attack surface. But as we know, the defenders are not the only ones buying vulnerabilities that hackers find.
Once a vulnerability is discovered, it can be used in a variety of ways. While it was common in the past, the number of independent security researchers disclosing bugs to companies without pay is waning, as more and more opportunities to monetize their skills become available. Over the years, bug bounties have proven to be an effective way to incent researchers to find and report individual vulnerabilities to the defense players. As the stakes and cash have risen in the market for vulnerabilities, the opportunity to sell to both offense and defense markets has increased.
The defense players will try to mitigate the risk or patch the vulnerability, while offensive use of a vulnerability can range from nation-state-sponsored attacks, to surveillance of civilian populations by their governments, to use in law enforcement operations, to criminal activity, to hacktivism, to simply causing mayhem. Some of the leaked Snowden documents confirmed what most in the security industry already know: governments, including the U.S., are major players in purchasing vulnerabilities at high prices to use for offense purposes. These same governments are also tasked with defending national security and critical infrastructure, and the choices they make of whether to turn a security hole over to the appropriate software vendor to fix it, or to add it to a stockpile of potential weapons is an interesting conundrum.
The offense buyers are in a position to outspend the defense buyers, so how do defenders hope to gain any advantage in this market? What are the market dynamics in play, and how can the defenders tip the scales in their favor?
If one can’t outbid them, how might one outsmart them?
Many have offered proposals that hinge on money as the key lever. A common argument when pricing bug bounties comes in the form of “you’ll never outbid the black market.” At the 2014 Black Hat Conference in Las Vegas, Dan Geer proposed that the government should buy all vulnerabilities at six figure prices to compete directly with offense market prices. These purchased vulnerabilities would then be handed over to the affected vendors to help drain the swamp of vulnerabilities, according to Geer.
As Geer notes, however, this approach will only work if vulnerabilities are scarce. Incenting more eyes to look for security bugs will help drain the offense stockpile, which is true, especially in less mature software. Vulnerabilities being scarce or dense all depends on the maturity of the software.
However, if an organization operating in the open, and focused on defense, offered six figure sums for vulnerabilities, regardless of whether the bounties are for mature software or not, this would introduce an entirely new problem. These potentially large payouts would create perverse incentives, especially for less mature software. After a short time, the only pool being drained would be the developer and tester talent pool – leaving their salaried jobs in order to live off their bounty earnings. Sell a couple bugs per year, and talented developers who can write fuzzers and determine which bugs are exploitable won’t need to work much harder to earn much higher paydays than any software maker could sustainably afford to pay them. Consequently, no one would be left to actually fix the bugs. This means that defenders can certainly get bugs faster by creating incentives for individual vulnerabilities, but an important limit to recognize here is that there is a ceiling on the prices they can offer without creating perverse incentives and undesirable consequences.
For defenders, there is a logical price ceiling for vulnerabilities, above which only offense-use buyers can go.
Why doesn’t this happen now, when offense market prices are already that high? Why would only a defense market at those prices be so disruptive? Because much of the offense market operates in the shadows, and one can never talk about their discoveries, so it doesn’t attract as many players as a public bounty program does. Not all hackers are primarily motivated by money. Even those who sell to governments, often do so selectively, intentionally choosing sides, even if the “other side” might pay them more money. Human behavior is always more complex than simply attributing decisions to greed and nothing more, and hackers are no exception.
What the creation of a six figure bug bounty for individual bugs by the defense market does is remove the undesirable effects of working in shadows. With that comes the additional undesirable consequence of incenting developers and testers to abandon their software in favor of finding more individual vulnerabilities in it. Under this model, we create incentives to identify vulnerabilities, without ensuring the resources needed to fix discovered flaws.
So if competing directly on price won’t work as a broad strategy for defense to gain an edge over offense, what are the other levers of the vulnerability economy?
If not price, what is the most efficient way for defenders to drain the offense stockpile of vulnerabilities?
The research: System Dynamics Modeling Revealing New Defense Incentive Strategies
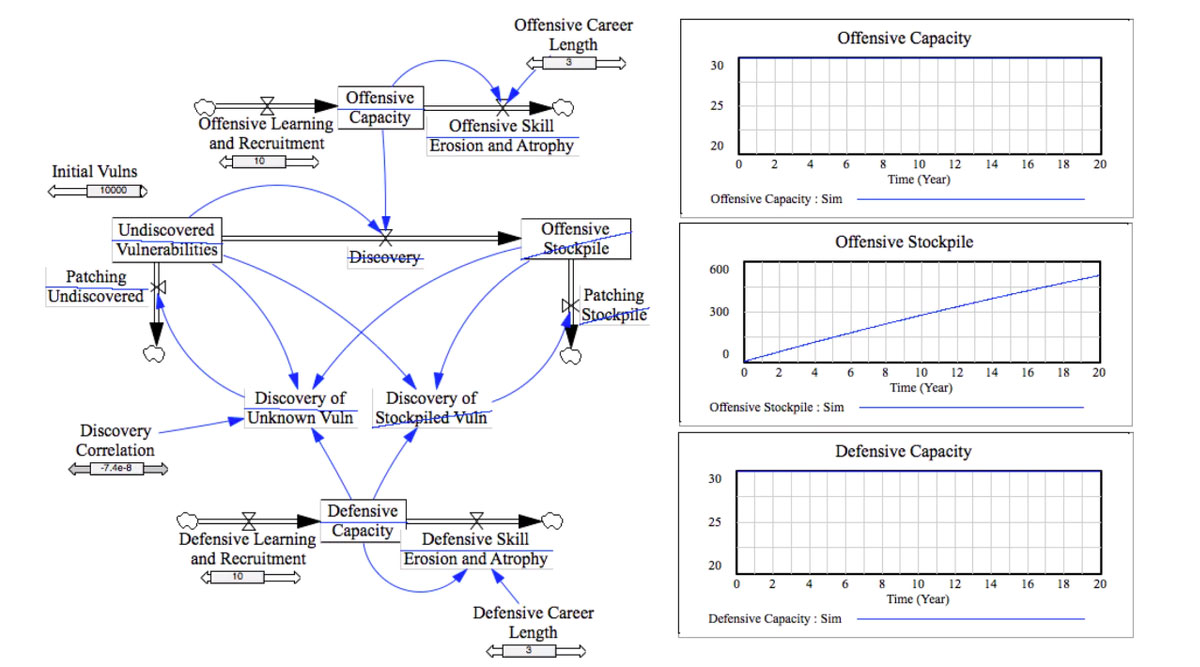 Image: Cyber Vulnerability Discovery Correlation Model
Image: Cyber Vulnerability Discovery Correlation Model
To begin to address these questions, Dr. Michael Siegel, Principal Researcher, Massachusetts Institute of Technology (MIT), Sloan School, and I set out to identify the true levers that impact the 0day vulnerability market. “At a high level, these models depend on understanding system and behavior. To do this we look at key sources of information including theory represented by research, we talk to subject matter experts and we look at what we can learn from the data,” according to Siegel.
System dynamics is a method for modeling complex systems, allowing for better understanding of problems. We worked with James Houghton at the Sloan School of Management, MIT to develop the model and analytics. Dr. Ryan Ellis at Harvard Kennedy School helped to articulate some of the broader policy questions. Lastly, Collin Greene at Facebook provided discussion and input, and the research work at MIT and Harvard was funded by a grant from Facebook.
The goal: To build a model that could answer the question of which lever works better for draining the offensive stockpile of vulnerabilities, or in other words, what can help defenders to find and fix as many of the same vulnerabilities that the offense market already has. The key to giving an edge to defense is not just to find and fix as many bugs as possible, but specifically to increase “bug collisions” in finding the same vulnerabilities as the offense researchers have found and get them fixed. A terrific real-world example of this approach in action is in effect by Google with its Project Zero initiative.
Dr. Siegel, Dr. Ellis, and James Houghton at MIT worked with my inputs to create the first system dynamics model of the 0day market to examine these levers. The effect on the offense stockpile of vulnerabilities is modeled by looking at defense and offense demonstrating the forces of supply and demand at work in the world of vulnerability discovery.
The Results
We want to maximize the discovery correlation and dry up the offensive stockpile.
– Dr. Michael Siegel, MIT
The counterintuitive outcome of creating this model is two-fold:
- More eyes only get you so far. Defenders throwing more bodies or money towards trying to find more vulnerabilities than the offense side can help, but not as efficiently as other measures. Bounties for individual bugs are great for this, and are especially effective for less mature software that hasn’t had much external scrutiny.
- Automation and efficiency helps defenders more than simply having more expert defenders. Defenders can more quickly drain the offense stockpile of vulnerabilities when they have access to better tools and techniques for vulnerability discovery. More mature vendors should consider augmenting their standard bug bounty programs to include special incentives for tools and techniques that help them find vulnerabilities more efficiently.
What is the broader implication for policy makers in governments that are tasked with defense, yet are building up offense capabilities? Governments need to broaden the focus.
For policy makers in government, who currently debate whether or not to disclose a specific vulnerability to the vendor to get it fixed to protect national security, or add it to their own offensive stockpile to use against domestic targets or other nations, this is an important question, but not the most pressing question. The conversation should broaden to include in this debate the idea of making tools and techniques available to defenders.
This problem translates to every type of organizations and technology, not just those that develop software.
– Dr. Michael Siegel, MIT
Now What
What Can We Do As An Industry?
For organizations: Individual organizations that want to reduce the number of security bugs overall should first invest in their Security Development Lifecycle, and then offer individual bug bounties as an ongoing security quality assurance measure to catch the vulnerabilities they missed. It’s also a way to find great defenders with the hacker mindset to hire. For more mature software, organizations should try creating incentives for tools and techniques in addition to any individual bug bounty to specifically increase the rate at which they can find the same bugs as the offense side has stockpiled.
For hackers: Good news! With more security research payment options than ever, hackers should invest in the work that motivates them. Ideally, hackers will have the best of all worlds, and they won’t have to choose between being paid and contributing to the greater good of the Internet. Research into better tools and techniques should open up even more avenues to be paid for expertise, in addition to the avenues for payment already available for individual bugs.
For governments: Many offense-oriented hackers who sell to governments will say that they don’t use tools for most of their vulnerability discovery. This is simply because they are that skilled. For defenders of varying skill levels to scale, tools are the most efficient way to try to catch up. Governments playing roles in both defense and offense should also try to help defenders gain access to better tools for vulnerability discovery.
For the Internet: Facebook and Microsoft, with the help of HackerOne, sponsor a program called the The Internet Bug Bounty (IBB) , a not-for-profit public benefit entity established to recognize and reward security research that improves critical Internet infrastructure including the OpenSSL library, the Apache and Nginx Web servers and the Ruby, Python, PHP and Perl programming languages, among others.
We are pleased to announce an expansion in the scope of the Internet Bug Bounty to include a bounty for tools and techniques that aid in vulnerability discovery and determining exploitability. We’d like to encourage hackers to make these tools available to the world, so that defenders can scale their efforts more efficiently. If you’d like to [nominate](panel@internetbugbounty.org) a tool or technique for a bounty under this program expansion, please include a publicly-available link to the tool and write-up, preferably pointing to resolved bugs found using this tool or technique. Example tools include but are not limited to fuzzers, debugger plugins, and especially ways to help determine exploitability of bugs more efficiently.
What’s next?
It has not escaped our notice that there are many more models to be made and research to do with the 0day market. Siegel, Houghton, Ellis and I plan to continue our work in this area and welcome other ideas and contributions to this and related work, expanding the research to include interested organizations’ data on the success of their incentive programs. Dr. Siegel and I will be presenting this model of the 0day market at RSA 2015 If you are interested in sponsoring or making a financial contribution to this ongoing research, please reach out to Michael.
In the end, the tug of war between attackers and defenders will always exist. How we structure incentives toward making offense more expensive for attackers and giving more defenders an advantage is the question. There are more levers to tip the scales from one side to the other than just money, and defenders need to begin to use them.
The Wolves of Vuln Street are among us, yet we are studying the dynamics of the pack to make the shepherds of Internet defense more effective.
– Katie Moussouris, Chief Policy Officer
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support Innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.





























![Pioneer [Blu-ray]](https://techcratic.com/wp-content/uploads/2024/11/81EmJG9mivL._SL1500_-360x180.jpg)






































