Deeba Ahmed
2024-11-15 10:08:00
hackread.com
SaaS Security firm AppOmni has identified misconfigurations in Microsoft Power Pages that can lead to severe data breaches. Learn about the common issues that expose sensitive information and how to protect your data in SaaS applications.
A recent discovery by AppOmni, a SaaS security company, revealed a security vulnerability in Microsoft Power Pages, a low-code platform over 250 million people use monthly. This issue has led to the exposure of millions of sensitive data records across various organizations in public and private sectors, “spanning financial services, healthcare, automotive and more,” explained AppOmni’s chief of SaaS security research, Aaron Costello in a report shared with Hackread.com.
This, according to researchers, includes the UK’s National Health Service (NHS), which leaked information for over 1.1 million NHS employees, including email addresses, phone numbers, and home addresses.
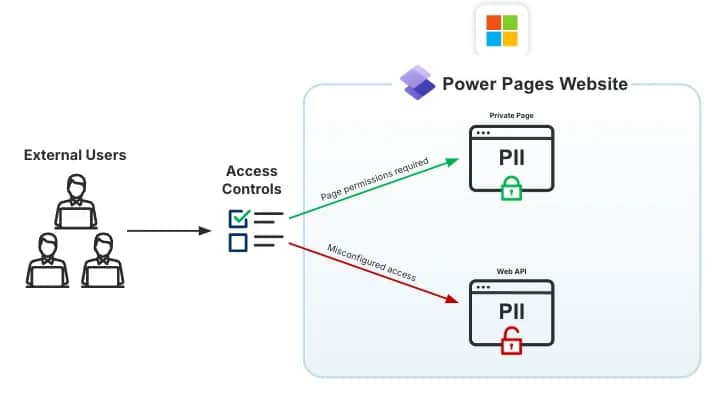
The root cause of these data leaks lies in misconfigured access controls within Power Pages for developing Dataverse-integrated applications like web portals. However, its customizable nature can expose sensitive data to the public.
How Does It Happen?
Power Pages, a powerful tool for building custom websites, relies on a layered approach to access control. This includes site-level, table-level, and column-level permissions. However, when organizations misconfigure these settings, they unintentionally expose sensitive data to the public internet.
Organizations can increase the potential attack surface by exposing more columns than necessary to the Web API. It can happen by setting the Webapi/ value to * allows access to all columns within a table, making sensitive information vulnerable, AppOmni explained in the blog post.
Enabling open registration and external authentication can grant unauthorized users access to sensitive data. That’s because, upon deployment, a site automatically allows self-registration and login by default, although these pages may not be visible on the platform. Users can register and authenticate through APIs, with ‘Authenticated Users’ having more permissions than ‘Anonymous Users’.
Another common mistake is granting global access to anonymous users, allowing anyone to view and potentially exploit sensitive information. Failing to implement column security, even if table-level permissions are correctly configured, can leave sensitive columns vulnerable to exposure. Lastly, not using data masking techniques can expose sensitive information like PII in plain text.
“These exposures are significant – Microsoft Power Pages is used by over 250 million users every month, as well as industry-leading organizations and government entities, spanning financial services, healthcare, automotive and more,” said Aaron.
“It’s clear that organizations need to prioritize security when managing external-facing websites, and balance ease of use with security in SaaS platforms – these are the applications holding the bulk of confidential corporate data today, and attackers are targeting them as a way into enterprise networks.”
The consequences of these misconfigurations can be severe, as shown by the NHS data leak. By exposing sensitive information, organizations risk compromising their reputation, facing legal repercussions, and potentially exposing their systems to further attacks.
This vulnerability also shows the risks associated with mismanaging access controls in SaaS applications, especially when dealing with sensitive data. Organizations should place proper security measures to manage security in SaaS platforms, which nowadays hold the bulk of confidential corporate data.
Additionally, regularly auditing access controls, limiting access to sensitive data, implementing strong authentication and authorization mechanisms, and staying updated on emerging security threats and vulnerabilities can significantly reduce the risk of data breaches and protect sensitive information.
RELATED TOPICS
- Nespresso Domain Hijacked to steal Microsoft Logins
- 250 million Microsoft user support records leaked in plain text
- Microsoft Bookings Flaw Enables Account Hijack, Impersonate
- Microsoft Bing server leaked user search queries, location data
- Hackers Could Exploit Microsoft Teams on macOS to Steal Data
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support Innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.
























































![Japanese Movie – The X From Outer Space (Uchu Dai Kaijyu Girara) [Japan BD] SHBR-263](https://techcratic.com/wp-content/uploads/2024/11/81rV3BDVGJL._SL1024_-360x180.jpg)