Deeba Ahmed
2024-12-24 11:11:00
hackread.com
KEY SUMMARY POINTs from the article
- Malicious Packages Identified: Zebo-0.1.0 and Cometlogger-0.1 are malicious Python packages discovered on PyPI.
- Sensitive Data Theft: These packages steal user data through keylogging, screenshot capturing, and information exfiltration.
- Persistence Mechanisms: They establish long-term control by creating startup scripts to re-execute on system reboot.
- Obfuscation Techniques: Advanced obfuscation methods help the packages evade detection and security systems.
- Wide Impact: These threats compromise developers and platforms reliant on PyPI, posing major privacy and security risks.
On November 24, 2024, Fortinet FortiGuard Lab’s AI-based detection system identified Python malware in two malicious Python packages, Zebo-0.1.0 and Cometlogger-0.1, targeting unsuspecting users for their data.
These packages can steal sensitive information, capture screenshots, log keystrokes, and establish unauthorized control over infected systems, researchers noted in the blog post shared with Hackread.com.
What is Zebo-0.1.0?
Zebo-0.1.0 exhibits typical malware characteristics, including functions designed for surveillance, data exfiltration, and unauthorized control, and utilizes libraries like pynput and ImageGrab, along with obfuscation techniques, indicating clear malicious intent.
The script employs obfuscation to hide its true functionality, making it harder for users or security systems to understand its actions. This obfuscation can bypass security measures, allowing the malware to run undetected.
Zebo-0.1.0 leverages pynput to log every keystroke made by the user and also captures screenshots of the desktop, potentially violating their privacy. Furthermore, the script exfiltrates sensitive information, such as keystrokes and screenshots, to a remote server, compromising user privacy.
To ensure persistence, the malware creates a Python script and a batch file in the Windows Startup folder, ensuring its re-execution upon system startup, making it difficult to remove and increasing the risk of long-term damage.
What is Cometlogger-0.1?
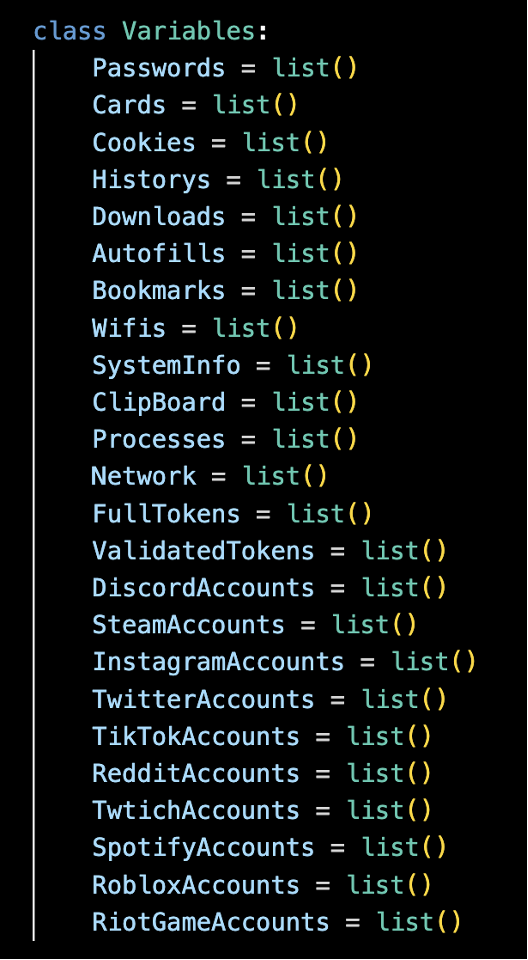
Cometlogger-0.1 maintains a long-term presence on the victim’s system and uses advanced techniques like obfuscation, keylogging, screen capturing, and data exfiltration to compromise user data. It dynamically requests a “webhook” from the user and embeds it into Python files, allowing for potential manipulation by unauthorized users. This can redirect sensitive data to malicious servers or facilitate command-and-control operations.
The script also targets various platforms like Discord, Steam, Instagram, and Twitter, stealing tokens, passwords, and account information. Additionally, it employs anti-VM detection techniques to evade analysis and incorporates dynamic file modification capabilities, enabling the injection of malicious code.
Both packages are a major threat to user privacy and security. Zebo-0.1.0 actively collects sensitive data and transmits it to remote servers. Cometlogger-0.1, on the other hand, focuses on information theft and maintaining a persistent presence on the victim’s system. The affected systems include all those platforms where PyPI packages can be installed with a High severity level, and threatens individuals or institutions whoever has installed these malicious packages.
The Python Package Index (PyPI) has become an invaluable resource for developers, offering a vast repository of reusable code. However, this convenience comes with inherent risks as malicious actors are increasingly exploiting it by publishing malicious packages that, when installed, can compromise systems. Socket Security researchers last month discovered another malicious Python package called “Fabrice” on PyPI downloaded over 37,000 times since its inception in 2021, harvesting AWS credentials from developers for three years.
To protect against these threats, it is crucial to disconnect from the internet, isolate the infected system, use reputable antivirus software, and reformat the system if necessary.
RELATED TOPICS
- Why is learning Python important in Data Science?
- 6 official Python repositories plagued with cryptomining malware
- PythonAnywhere Cloud Platform Abused for Hosting Ransomware
- Python in Threat Intelligence: Analyzing – Mitigating Cyber Threats
- NTLM Credential Theft in Python Apps Threaten Windows Security
Keep your files stored safely and securely with the SanDisk 2TB Extreme Portable SSD. With over 69,505 ratings and an impressive 4.6 out of 5 stars, this product has been purchased over 8K+ times in the past month. At only $129.99, this Amazon’s Choice product is a must-have for secure file storage.
Help keep private content private with the included password protection featuring 256-bit AES hardware encryption. Order now for just $129.99 on Amazon!
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support Innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.