2025-01-14 21:34:00
www.techspot.com
TL;DR: USB-C support on the latest iPhones gives users one less proprietary cable to worry about, however, it could also pave the way for future security vulnerabilities. Although no hacking incidents targeting the device’s USB-C controller have been reported yet, early research suggests that accessing the controller’s firmware and executing code is technically feasible.
Security researcher Thomas Roth recently uncovered several vulnerabilities in Apple’s ACE3 USB-C controller for the iPhone 15 and 16. Although no immediate action is required from users, and these vulnerabilities don’t affect Android devices, Roth’s findings underscore the possibility of future attack methods being developed.
At the 38th Chaos Communication Congress in Hamburg last month, Roth demonstrated two advanced techniques – side-channel analysis and electromagnetic fault injection – on Apple’s USB-C controller. Notably, he successfully dumped the firmware.
While extracting the firmware alone won’t directly enable cyberattacks, it provides malicious actors with an opportunity to analyze the code, identify vulnerabilities, and potentially develop malware to exploit them. Apple has opted not to take action at this time, citing the complexity of Roth’s methods. However, if attackers use the dumped firmware as a foundation for discovering security flaws, the company may be forced to respond.
One potential response could involve revising the hardware in future iPhone models. Any emerging issues would likely impact iPhones expected in the next few years, including the rumored iPhone SE 4, which is expected to debut this March, and the iPhone 17 family anticipated later this year. More radical hardware revisions, such as the long-rumored foldable iPhone, could include enhanced security measures to address such risks.

Apple was forced to add USB-C support on the iPhone to comply with recent European regulations mandating all mobile devices to include USB-C charging ports. Formal standardization benefits consumers by eliminating the need for proprietary cables, though in this instance it could be argued it’s opened the door to new security challenges for Apple to pay attention to.
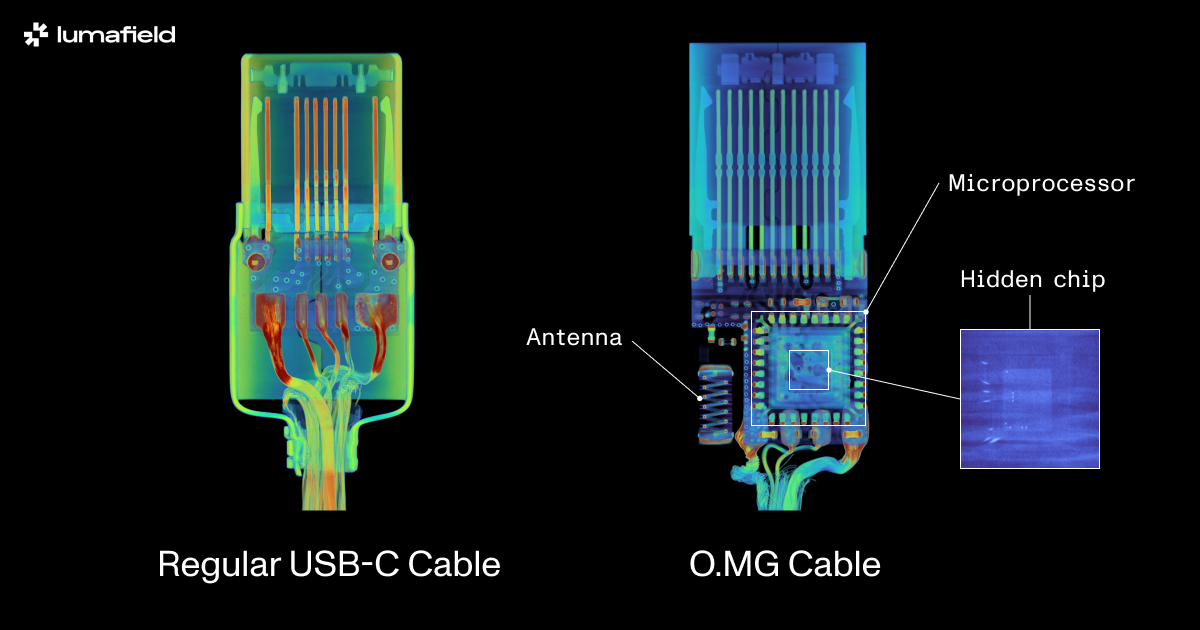
New X-ray scanning techniques have revealed that USB-C cables could contain a surprising amount of hidden hardware. Cables produced by disreputable manufacturers could be used to distribute malware or steal data, and distinguishing these from legitimate cables might require advanced tools that average consumers do not have. Exposing the firmware for Apple’s USB-C controller could facilitate similar attacks in the future.
However, there is a silver lining. Dumping the firmware has also produced positive outcomes. Independent repair specialists have already used Roth’s research to gain valuable insights into diagnosing and repairing Macs.
Apple and other tech companies have faced criticism in the past for obstructing user or third-party repair efforts, often requiring customers to pay exorbitant fees for authorized service. Roth’s findings could help shift the balance toward greater repairability and transparency.

Keep your entertainment at your fingertips with the Amazon Fire TV Stick 4K! Enjoy streaming in 4K Ultra HD with access to top services like Netflix, Prime Video, Disney+, and more. With an easy-to-use interface and voice remote, it’s the ultimate streaming device, now at only $21.99 — that’s 56% off!
With a 4.7/5-star rating from 43,582 reviews and 10K+ bought in the past month, it’s a top choice for home entertainment! Buy Now for $21.99 on Amazon!
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support Innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.