Divya
2025-01-22 00:35:00
gbhackers.com
A potential security flaw in IBM i Access Client Solutions (ACS) has raised serious concerns about password leakage, leaving users vulnerable to exploitation.
Research published yesterday by a vulnerability assessment team revealed that the *WINLOGON authentication feature in IBM ACS is questionably storing Windows credentials, potentially exposing plaintext passwords.
This alarming discovery has prompted immediate calls for action from the IT and cybersecurity communities.
The Core Issue
The IBM i Access Client Solutions platform, long used for integrating IBM i systems with Windows environments, relies on Windows credentials for authentication under its *WINLOGON option.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
This feature, designed for convenience, eliminates the need to repeatedly prompt users for credentials.
However, the research reveals that earlier versions of the ACS “Application Package” (before updates in 2024) store Windows passwords in the Windows Registry using weak obfuscation.
While newer versions of ACS have introduced access control lists (ACLs) to secure these Registry entries, the stored passwords remain vulnerable to reverse engineering.
Attackers with administrative access can extract these critical credentials, bypassing Microsoft’s Local Security Authority (LSA) protections.
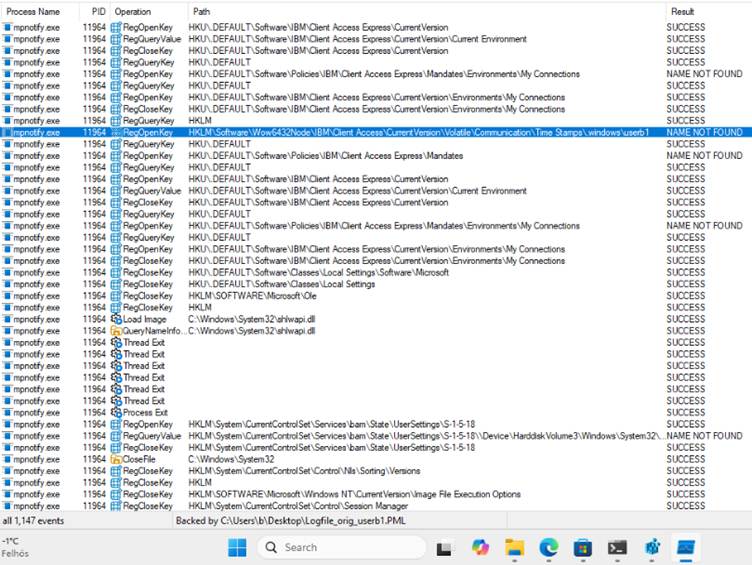
As per a report by Silent Signal, the researchers noted that ACS writes obfuscated password data to this key in the Windows Registry:
HKLM\SOFTWARE\Wow6432Node\IBM\Client Access\CurrentVersion\Volatile\Communication\Time Stamps\.windows\


What makes this particularly troubling is the ease with which the obfuscation can be reversed.
According to the findings, the encryption technique uses predictable, timestamp-based keys that are stored alongside the password data, rendering the mechanism ineffective against sophisticated attackers.
Microsoft’s Mitigation Adds Complexity
This issue is compounded by changes introduced in Windows 11 24H2. Microsoft enabled LSA Protection by default as part of their system updates, blocking legacy *WINLOGON authentication mechanisms.

Under these new protections, the Local Security Authority Subsystem Service (LSASS) rejects passwords passed to it by older ACS versions.
However, while this change prevents ACS from directly accessing credentials via LSA, it does not resolve the underlying problem of already stored plaintext passwords.
A deeper inspection of the Registry hive may reveal residual password data in backups, even on systems that have applied updates.
Plaintext password storage not only undermines Microsoft’s efforts to secure user credentials against local threats but also introduces risks for organizations implementing IBM i systems.
Attackers who gain administrator access to systems running older versions of ACS could potentially extract these credentials and use them for lateral movement, escalating their attacks within a network.
Moreover, the IBM ACS situation highlights broader challenges in single sign-on (SSO) solutions. With modern threats in mind, proper credential handling is essential, but IBM’s reliance on outdated mechanisms leaves users exposed.


While IBM has since deprecated *WINLOGON and discouraged its use, the ramifications of the legacy feature remain significant, especially for organizations still running older ACS versions.
To mitigate the risks, cybersecurity experts recommend the following:
- Update IBM ACS Versions: Ensure all systems are running the latest version of ACS and avoid using outdated implementations of the Application Package.
- Scan for Vulnerabilities: Use tools to search for “Function Admin Timestamp” Registry values and remove any remnants of stored passwords.
- Enable LSA Protection: On Windows systems, ensure Local Security Authority protections are enabled to prevent potential exploitation of this vulnerability.
- Transition to Secure Authentication Methods: Organizations should implement robust single sign-on (SSO) mechanisms, such as Kerberos, even if the configuration is more complex.
The discovery of this vulnerability illustrates the risks of legacy authentication and password storage methods.
IBM must prioritize secure-by-design principles in its product development, while users must remain vigilant in keeping systems up to date.
As a precaution, organizations should act quickly to audit their systems for implementation of the *WINLOGON feature and ensure proper credential hygiene.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
Keep your files stored safely and securely with the SanDisk 2TB Extreme Portable SSD. With over 69,505 ratings and an impressive 4.6 out of 5 stars, this product has been purchased over 8K+ times in the past month. At only $129.99, this Amazon’s Choice product is a must-have for secure file storage.
Help keep private content private with the included password protection featuring 256-bit AES hardware encryption. Order now for just $129.99 on Amazon!
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support Innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.






































![Lost Lands 8: Sand Captivity CE [37] Let's Play walkthrough – BONUS – Part 37](https://techcratic.com/wp-content/uploads/2025/04/1745476412_maxresdefault-360x180.jpg)
































