Sandeep Singh
2024-11-06 12:21:00
www.hackerone.com
HackerOne’s 8th Annual Hacker-Powered Security Report states that improper access control is the second most common vulnerability reported in a bug bounty and number three reported in pentests. It makes up 9% of all vulnerability types discovered on the HackerOne platform.
Despite being considered a “low-hanging fruit” vulnerability type, improper access control can significantly impact an organization, including data breaches and theft, system disruption, third-party risk, financial damages, and legal/compliance repercussions.
Let’s look more closely at improper access control — what it is, how it’s used, and how to remediate it.
What Is Improper Access Control?
Access controls are the security measures that control access to a system, its data, and its user permissions. They define who can access what. These measures fit into three categories:
- Authentication: Proving the identity of a user.
- Authorization: Confirming a user should be allowed to access specific data or resources.
- Auditing: Tracking and logging what actions the user has taken.
Improper access control refers to issues that arise when restrictions on access to a system or data are not properly implemented, allowing unauthorized access. Improper access control can manifest in many different ways, including:
- Access rules that are too permissive, allowing access beyond what is needed for legitimate purposes
- Lack of authentication requirements, allowing anyone access without verifying identity
- Insecure default configurations that allow more access than intended
- Failure to restrict access based on roles, allowing lower-level users access to privileged functions
- Not properly revoking access when no longer needed, allowing former employees/users to obtain access to systems still
The key aspect is that improper access controls create vulnerabilities by allowing unauthorized users to access systems or data they should not have access to based on policy. Proper access controls should follow the principle of least privilege, be restrictive in granting access, and be careful about revocation.
Business Impact of Improper Access Control
- Data breaches and theft: Unauthorized access can lead to malicious actors accessing and stealing sensitive data like customer information, trade secrets, financial data, or intellectual property. This can cause significant financial, legal, and reputational damages.
- System disruption: Improper access enables compromise of critical systems. Malicious actors can launch ransomware, delete or corrupt data, or disrupt operations — hampering productivity and capabilities.
- Regulatory non-compliance: Regulations such as HIPAA, PCI-DSS, and NIST require strong access controls. Failure to meet compliance can result in heavy fines and loss of certifications needed to operate.
- Privilege abuse: Overly permissive access enables insider threats where employees/users misuse elevated privileges to compromise security for personal gain. This results in fraud or sabotage.
- Third-party risk: Poor access controls around external party access like vendors and partners enable these external threats to compromise security and increase risk surface.
What Industries Are Impacted By Improper Access Control?
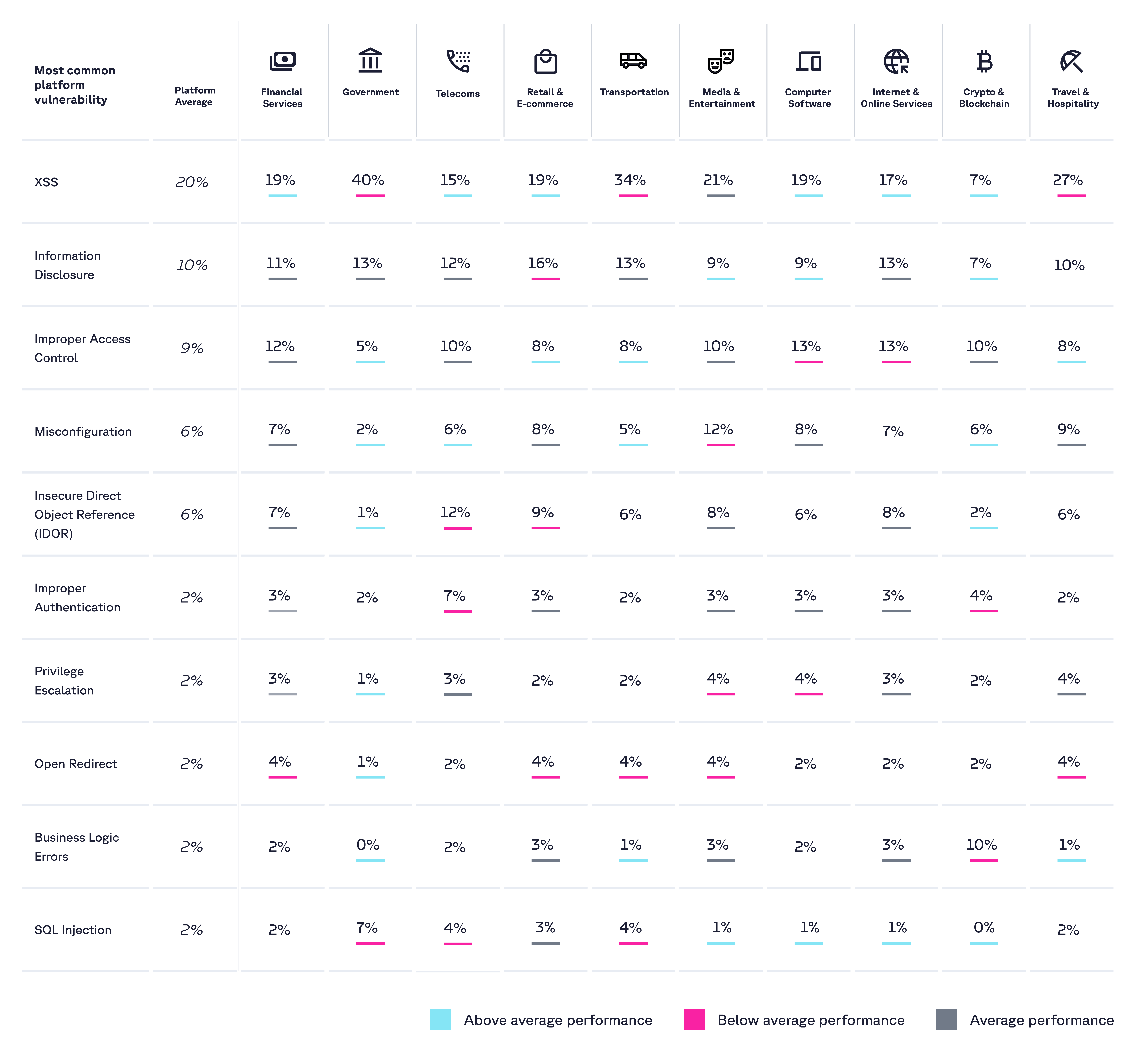
Improper access control issues do not discriminate by industry. However, it is more prominent in some industries than others. The chart below illustrates the top vulnerabilities across the HackerOne platform by industry. Improper access control only makes up 5% of vulnerabilities identified in the Government space, yet it makes up a massive 13% in Internet and Online Services. Government agencies are highly regulated when it comes to access and the protection of sensitive data. On the other hand, Internet and Online Services organizations have extensive web presences that make it challenging to manage access, so they see more low-hanging fruit vulnerabilities that have yet to be identified and remediated by their internal security teams.
Look at how many of your vulnerabilities are improper access control compared to the average for your industry.
A Real-world Example of an Improper Access Control Vulnerability
HackerOne’s Hacktivity resource showcases disclosed vulnerabilities on the HackerOne Platform. Check it out to see how specific weaknesses have been identified and fixed. The following improper access control example demonstrates how a hacker discovered a vulnerability in KAYAK that could allow an attacker to take over any account logged into the organization’s Android application.
Customer: KAYAK
Vulnerability: Improper Access Control
Severity: Critical
Summary
While researching zero-day vulnerabilities in mobile applications, the ethical hacker @retr02332 found it was possible to steal a user’s session cookie through a malicious deeplink in KAYAK v161.1. With a one-click attack, an unauthenticated, remote attacker could steal the account of any victim logged into the KAYAK mobile app for Android.
Impact
The hacker demonstrated that crafting a specific deeplink with the victim’s email address can allow an attacker to gain access to the victim’s KAYAK account in one click without any authentication. They showed the following steps to reproduce the exploit:
- Craft the following deeplink with the victim’s email address: kayak://login?email=victim@email.com
- Send the deeplink to the victim and trick them into clicking on it.
- The deeplink will automatically log the attacker into the victim’s Kayak account in the Android app without any authentication.
This allows an attacker to gain unauthorized access to the victim’s KAYAK account, view their personal information, and perform account actions as the victim.
Remediation
An initial patch was made available via the Google Play Store the day after the finding was reported to KAYAK. Thankfully, the vulnerability was introduced only very recently prior to its discovery, and the security team at KAYAK determined that it has been exploited.
In general, implementing controls focused on granting minimal necessary access, enforcing checks and balances, requiring multi-factor authentication, and user education are all key for preventing and remediating improper access control vulnerabilities.
Secure Your Organization From Improper Access Control With HackerOne
This is only one example of the pervasiveness and impact severity of an improper access control vulnerability. HackerOne and our community of ethical hackers are the best equipped to help organizations identify and remediate improper access control and other vulnerabilities, whether through bug bounty, Pentest as a Service (PTaaS), Code Security Audit, or other solutions by considering the attacker’s mindset on discovering a vulnerability.
Download the 8th Annual Hacker-Powered Security Report to learn more about the impact of the top 10 HackerOne vulnerabilities, or contact HackerOne to get started taking on improper access control at your organization.
Keep your files stored safely and securely with the SanDisk 2TB Extreme Portable SSD. With over 69,505 ratings and an impressive 4.6 out of 5 stars, this product has been purchased over 8K+ times in the past month. At only $129.99, this Amazon’s Choice product is a must-have for secure file storage.
Help keep private content private with the included password protection featuring 256-bit AES hardware encryption. Order now for just $129.99 on Amazon!
Support Techcratic
If you find value in Techcratic’s insights and articles, consider supporting us with Bitcoin. Your support helps me, as a solo operator, continue delivering high-quality content while managing all the technical aspects, from server maintenance to blog writing, future updates, and improvements. Support Innovation! Thank you.
Bitcoin Address:
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge
Please verify this address before sending funds.
Bitcoin QR Code
Simply scan the QR code below to support Techcratic.

Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.

































































































