Divya
2025-02-20 08:23:00
gbhackers.com
Cybersecurity experts have raised alarms about the Rhadamanthys Infostealer, a sophisticated malware now being distributed through Microsoft Management Console (MMC) files with the MSC extension.
This new tactic, confirmed by the AhnLab Security Intelligence Center (ASEC), exploits the flexibility of MSC files, which are XML-based and capable of executing scripts, commands, and programs.
The malware’s innovative use of MMC highlights the growing threat posed by attackers leveraging legitimate tools for malicious purposes.
Two Methods of Exploitation
The Rhadamanthys Infostealer employs two distinct methods to spread via MSC files:
- Exploiting apds.dll Vulnerability (CVE-2024-43572):
This method involves exploiting a vulnerability in the apds.dll file. Specifically, attackers use the resource named “redirect.html” within apds.dll to execute malicious code.
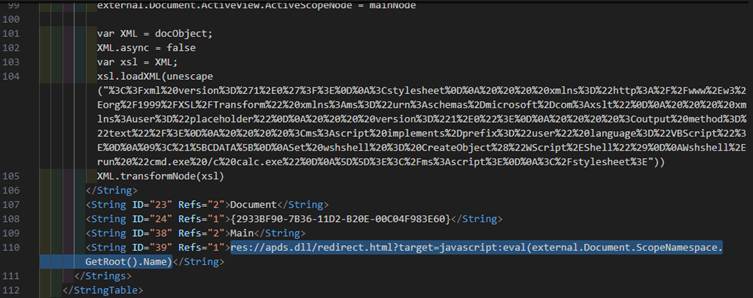

By embedding a specific syntax (res://apds.dll/redirect.html?target=javascript:eval(…)) in the MSC file, the malware accesses and executes code directly within the vulnerable DLL.

This approach bypasses MMC and allows attackers to execute arbitrary commands. However, this vulnerability has been patched, reducing its current effectiveness.
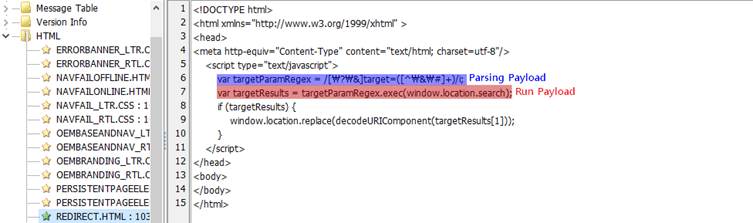
- Using Console Taskpad:
The second method leverages MMC’s Console Taskpad feature, which interprets and executes commands embedded between

Unlike the DLL exploitation method, this technique does not rely on vulnerabilities but instead uses MMC’s legitimate task execution capabilities.
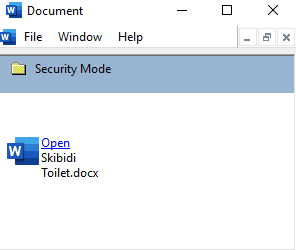
Attackers disguise malicious MSC files as seemingly harmless documents, such as MS Word files.
When opened, these files trigger a PowerShell script download from an external source, which subsequently executes the Rhadamanthys Infostealer.
Although patches have mitigated some vulnerabilities like CVE-2024-43572, the continued use of Console Taskpad for malware distribution underscores the need for vigilance. To protect against such threats:
- Avoid opening MSC files from unknown or untrusted sources.
- Ensure that all software is updated with the latest security patches.
- Use robust antivirus solutions capable of detecting unconventional attack vectors.
- Educate users about phishing tactics and suspicious file formats.
The rise in MSC-based malware campaigns highlights how attackers adapt their methods to exploit overlooked tools like MMC.
As cybercriminals continue refining their techniques, organizations must remain proactive in securing their systems against evolving threats like Rhadamanthys Infostealer.
Free Webinar: Better SOC with Interactive Malware Sandbox for Incident Response, and Threat Hunting - Register Here
Keep your files stored safely and securely with the SanDisk 2TB Extreme Portable SSD. With over 69,505 ratings and an impressive 4.6 out of 5 stars, this product has been purchased over 8K+ times in the past month. At only $129.99, this Amazon’s Choice product is a must-have for secure file storage.
Help keep private content private with the included password protection featuring 256-bit AES hardware encryption. Order now for just $129.99 on Amazon!
Help Power Techcratic’s Future – Scan To Support
If Techcratic’s content and insights have helped you, consider giving back by supporting the platform with crypto. Every contribution makes a difference, whether it’s for high-quality content, server maintenance, or future updates. Techcratic is constantly evolving, and your support helps drive that progress.
As a solo operator who wears all the hats, creating content, managing the tech, and running the site, your support allows me to stay focused on delivering valuable resources. Your support keeps everything running smoothly and enables me to continue creating the content you love. I’m deeply grateful for your support, it truly means the world to me! Thank you!
|
BITCOIN
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge Scan the QR code with your crypto wallet app |
|
DOGECOIN
D64GwvvYQxFXYyan3oQCrmWfidf6T3JpBA Scan the QR code with your crypto wallet app |
|
ETHEREUM
0xe9BC980DF3d985730dA827996B43E4A62CCBAA7a Scan the QR code with your crypto wallet app |
Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.









































































































