HackerOne
2016-01-13 07:37:00
www.hackerone.com
HackerOne is committed to creating a safer Internet. In that spirit, we believe that evaluating and sharing the results of our own vulnerability disclosure and bug bounty program is important. HackerOne invites hackers to share vulnerability reports they find in our software. All members of our development team rotate through triaging incoming vulnerability reports, making fixes and awarding bounties when they’re warranted. As we enter 2016, we’d like to share our 2015 stats and talk about adjustments we’re making for 2016.
Over the course of 2015, nearly 600 hackers participated in the HackerOne bounty program, submitting approximately 1,500 reports. From this, we resolved 58 valid security vulnerabilities, and awarded bounties for 38 of them. For a few vulnerabilities, we rewarded more than one hacker. This translated to rewarding 41 unique hackers a total $41,100, with an average payout of $1,082. Compared to 2014, HackerOne enjoyed a 20% increase in hacker participation during 2015. As hackers found increasingly challenging bugs in 2015, our average bounty payout was up nearly 300%.
The highest awarded hacker in our program was @danlec, who reported five valid vulnerabilities that garnered $18,000 in rewards. Of these bugs, two impressed us in particular. The first was an XSS related to React components and the other an XSS in the Markdown parser we use. We awarded $5,000 for each of these, which is also the largest payout amount the HackerOne program has made to a hacker. We have publicly disclosed the vulnerability reports so that others can learn from them.
On the response front, the HackerOne team improved its resolution time by two days, bringing average resolution down to 18 days, while averaging an initial response time to hackers of 16 hours.
Compared to our more than 400 customers, HackerOne ranked in the 90th percentile based on our HackerOne Success Index (HSI). The HSI is a method to measure the effectiveness of HackerOne-powered vulnerability disclosure and bug bounty programs. It includes six dimensions, ranging from 0 to 10, by which programs can benchmark their success.
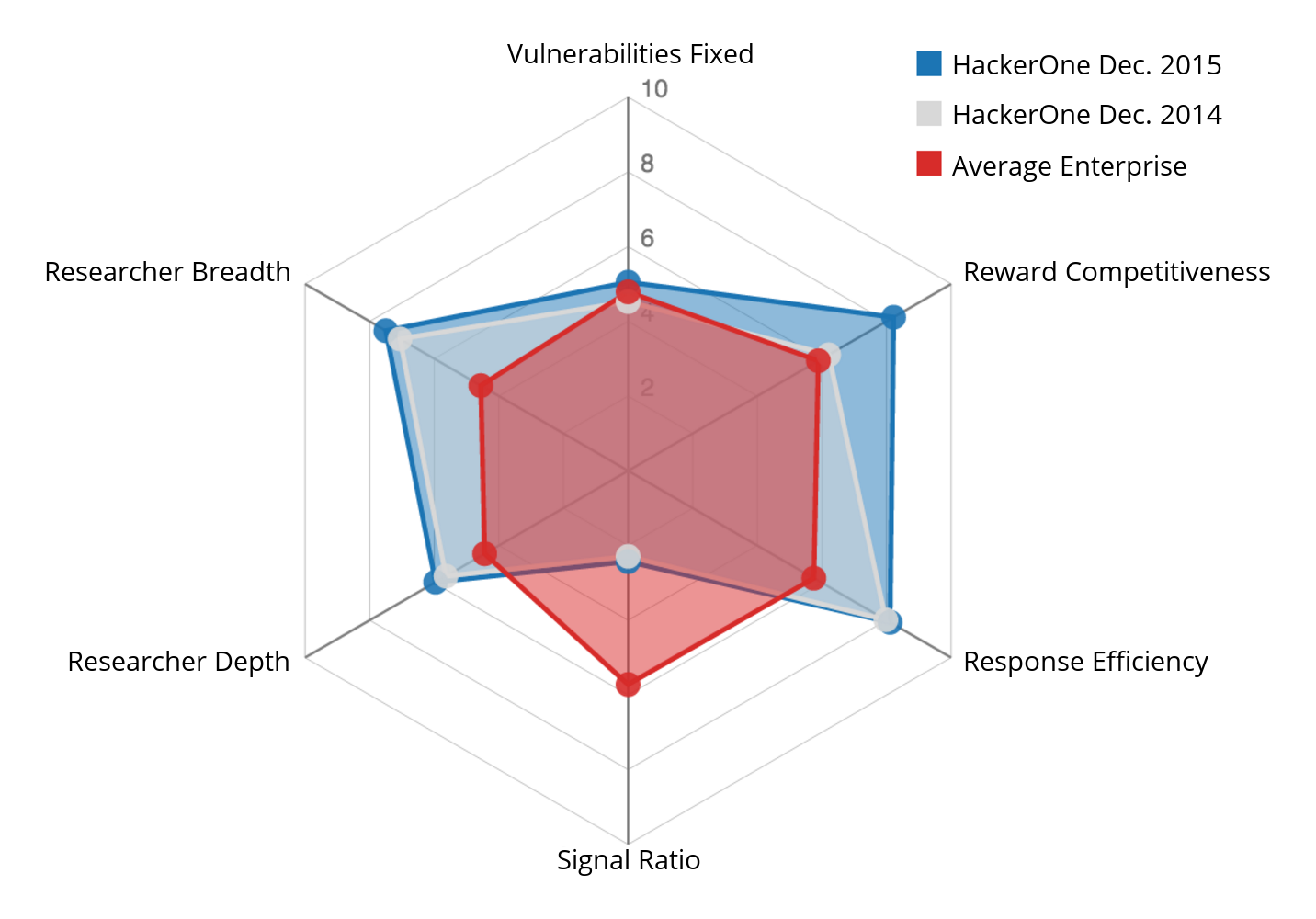 HackerOne’s HSI in 2014 and 2015 compared to the Enterprise Average HSI.
HackerOne’s HSI in 2014 and 2015 compared to the Enterprise Average HSI.
The above HSI spider chart offers a visualization of HackerOne’s own bug bounty program. We show HackerOne’s 2014 scores in grey, compared to those of the average Enterprise-sized companies, in red. In blue we show HackerOne’s 2015 scores. HackerOne outperforms the enterprise group in Researcher Breadth, Response Efficiency and Reward Competitiveness. It performs on par in Vulnerabilities Fixed, which is a solid outcome, given that larger companies stand to find and fix more vulnerabilities than a company of HackerOne’s smaller size. Where HackerOne has traded off performance, as measured by the HSI, is on Signal Ratio. This is a choice as the company runs a public program and pays very well for researcher time. This attracts the maximum number of hackers to submit vulnerability reports to us. We believe that this extra level of continuous probing of our attack surface results in more secure software. In short, we are glad to manage a large volume of incoming reports to achieve a more secure perimeter.
We look forward to resolving even more issues with the help of the hacker community in 2016. As an important next step in the evolution of our program, HackerOne is increasing the minimum bounty for severe issues to $10,000. Our goal remains to continue to encourage additional eyes on HackerOne and to reward the talented individuals that continue to help us identify and help us resolve vulnerabilities. Want more information or looking to submit a bug? You can find our program here: https://hackerone.com/security. If you run a program on HackerOne and would like to learn how you rank on the HackerOne Success Index, just reach out to us through support@hackerone.com and we’ll be happy to review your program with you.
Happy hacking in the new year!
– Jobert Abma
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty solutions encompass vulnerability assessment, crowdsourced security testing and responsible disclosure management. Discover more about our hacker powered security testing solutions or Contact Us today.
Keep your files stored safely and securely with the SanDisk 2TB Extreme Portable SSD. With over 69,505 ratings and an impressive 4.6 out of 5 stars, this product has been purchased over 8K+ times in the past month. At only $129.99, this Amazon’s Choice product is a must-have for secure file storage.
Help keep private content private with the included password protection featuring 256-bit AES hardware encryption. Order now for just $129.99 on Amazon!
Help Power Techcratic’s Future – Scan To Support
If Techcratic’s content and insights have helped you, consider giving back by supporting the platform with crypto. Every contribution makes a difference, whether it’s for high-quality content, server maintenance, or future updates. Techcratic is constantly evolving, and your support helps drive that progress.
As a solo operator who wears all the hats, creating content, managing the tech, and running the site, your support allows me to stay focused on delivering valuable resources. Your support keeps everything running smoothly and enables me to continue creating the content you love. I’m deeply grateful for your support, it truly means the world to me! Thank you!
|
BITCOIN
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge Scan the QR code with your crypto wallet app |
|
DOGECOIN
D64GwvvYQxFXYyan3oQCrmWfidf6T3JpBA Scan the QR code with your crypto wallet app |
|
ETHEREUM
0xe9BC980DF3d985730dA827996B43E4A62CCBAA7a Scan the QR code with your crypto wallet app |
Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.


























































![SABRENT [3-Pack 22AWG Premium 6ft USB-C to USB A 3.0 Sync and Charge Cables [Black]…](https://techcratic.com/wp-content/uploads/2025/08/81SQ13LNwfL._SL1500_-360x180.jpg)













































