Aman Mishra
2025-02-24 12:53:00
gbhackers.com
A significant vulnerability has been discovered in the Sliver C2 server, a popular open-source cross-platform adversary emulation and red team framework.
This vulnerability, identified as CVE-2025-27090, allows attackers to hijack TCP connections, enabling them to intercept and manipulate traffic.
The exploit leverages a Server-Side Request Forgery (SSRF) technique, which can be particularly damaging as it allows attackers to bypass network defenses and access internal services.
Impact and Affected Versions
The vulnerability affects Sliver C2 server versions from v1.5.26 to v1.5.42 and v1.6.0 prior to commit 0f340a2.

This means that any server installed since September 2022 could be vulnerable.
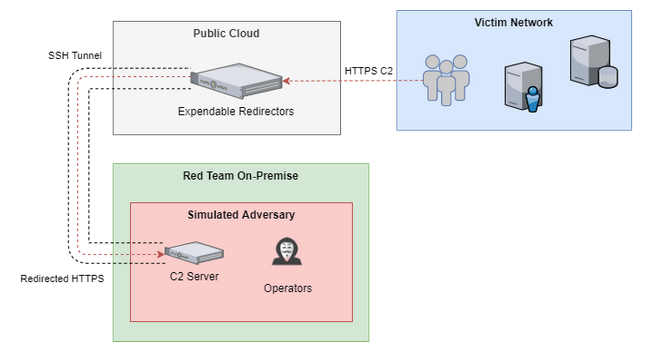
The SSRF exploit can lead to severe consequences, including the exposure of teamserver IPs behind redirectors and lateral movement within the network.
An attacker must have access to a C2 port and either a staging listener or a stager-generated implant binary to exploit this vulnerability.
Exploitation Mechanism
The exploitation process involves spoofing implant traffic to manipulate the teamserver into opening a TCP connection to an arbitrary IP and port.
This is achieved by manipulating the envelope type in the implant traffic, allowing attackers to call specific handler functions.
Key functions targeted include registerSessionHandler and tunnelDataHandler.
By registering a session and creating a reverse tunnel, attackers can establish a connection to any desired endpoint, effectively hijacking TCP traffic.
The tunnelDataHandler function is particularly critical as it allows the creation of a reverse tunnel.
By setting the CreateReverse field to true and specifying the target IP and port, attackers can coerce the teamserver into establishing a connection to an arbitrary endpoint.
According to the research, this connection can then be used to read and write traffic, effectively intercepting and manipulating data.
To mitigate this vulnerability, users are advised to update their Sliver C2 servers to the latest patched version.
The advisory and patched release are available for download, providing a fix for the SSRF vulnerability.
Users should ensure that all affected versions are updated promptly to prevent potential exploitation.
The vulnerability highlights the importance of regular security audits and updates in maintaining the integrity of critical infrastructure tools like Sliver C2.
Free Webinar: Better SOC with Interactive Malware Sandbox for Incident Response, and Threat Hunting - Register Here
Keep your files stored safely and securely with the SanDisk 2TB Extreme Portable SSD. With over 69,505 ratings and an impressive 4.6 out of 5 stars, this product has been purchased over 8K+ times in the past month. At only $129.99, this Amazon’s Choice product is a must-have for secure file storage.
Help keep private content private with the included password protection featuring 256-bit AES hardware encryption. Order now for just $129.99 on Amazon!
Help Power Techcratic’s Future – Scan To Support
If Techcratic’s content and insights have helped you, consider giving back by supporting the platform with crypto. Every contribution makes a difference, whether it’s for high-quality content, server maintenance, or future updates. Techcratic is constantly evolving, and your support helps drive that progress.
As a solo operator who wears all the hats, creating content, managing the tech, and running the site, your support allows me to stay focused on delivering valuable resources. Your support keeps everything running smoothly and enables me to continue creating the content you love. I’m deeply grateful for your support, it truly means the world to me! Thank you!
|
BITCOIN
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge Scan the QR code with your crypto wallet app |
|
DOGECOIN
D64GwvvYQxFXYyan3oQCrmWfidf6T3JpBA Scan the QR code with your crypto wallet app |
|
ETHEREUM
0xe9BC980DF3d985730dA827996B43E4A62CCBAA7a Scan the QR code with your crypto wallet app |
Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.
























































![SABRENT [3-Pack 22AWG Premium 6ft USB-C to USB A 3.0 Sync and Charge Cables [Black]…](https://techcratic.com/wp-content/uploads/2025/08/81SQ13LNwfL._SL1500_-360x180.jpg)















































