Divya
2025-03-19 01:58:00
gbhackers.com
A critical vulnerability in Windows File Explorer has been discovered, allowing attackers to capture NTLM hashes and potentially exploit them for network spoofing attacks.
The vulnerability, identified as CVE-2025-24071, involves the automatic processing of specially crafted .library-ms files within compressed archives like RAR or ZIP.
When these files, containing paths to attacker-controlled SMB servers, are extracted, Windows Explorer initiates an implicit NTLM authentication handshake, leaking sensitive credentials without requiring user interaction, as per a report by CTI monster.
CVE-2025-24071: Overview of the Vulnerability
CVE-2025-24071 is a significant issue in Windows File Explorer that exploits the automatic processing of .library-ms files.
These XML-based files define search and library locations and are trusted by Windows Explorer.
When a .library-ms file containing an SMB path is extracted from a compressed archive, Windows Explorer attempts to resolve this path automatically to gather metadata and index file information.
This process triggers an NTLM authentication handshake with the attacker-controlled SMB server, leaking the victim’s NTLMv2 hash without any explicit user interaction.


The vulnerability is particularly dangerous because it does not require the user to open or execute the extracted file; simply extracting it from the archive is enough to trigger the NTLM hash leak.
This makes it a powerful tool for attackers seeking to compromise network security through pass-the-hash attacks or offline NTLM hash cracking.
Technical Explanation
- Automatic File Processing: Upon extraction from a compressed archive, Windows Explorer and the SearchProtocolHost.exe service automatically process the .library-ms file. This involves opening the file, reading its contents to extract metadata, and querying file information. These operations occur without any explicit user interaction and can be observed using tools like Procmon.
- SMB Communication: The extraction process triggers SMB communication attempts. Using Wireshark with an SMB filter, researchers can capture the SMB2 Negotiate Protocol Request and the SMB2 Session Setup Request, which clearly show the initiation of an NTLM authentication handshake between the victim’s system and the attacker-controlled SMB server.
Proof of Concept (PoC)
A Proof of Concept (PoC) for CVE-2025-24071 has been released on GitHub.
It demonstrates how attackers can exploit this vulnerability to capture NTLM hashes by creating a specially crafted .library-ms file and embedding it within a RAR or ZIP archive.
The PoC can be executed using Python, requiring minimal input such as the target file name and the attacker’s IP address.
python poc.py
# Enter file name: your_file_name
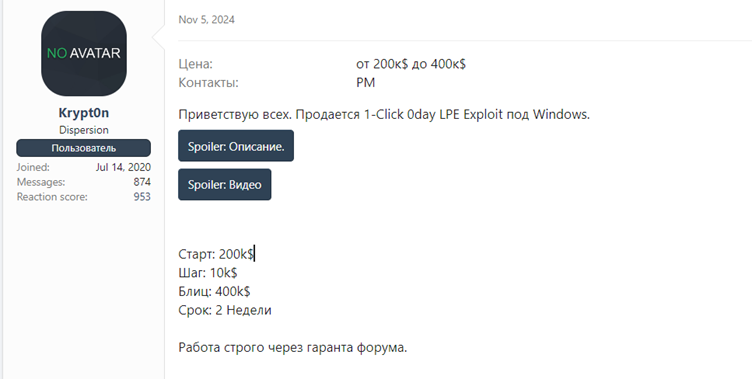
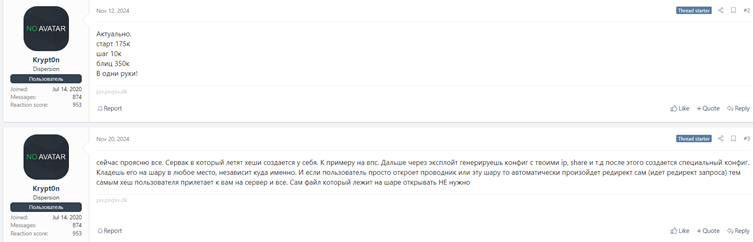
# Enter IP: attacker_IPCVE-2025-24071 is reportedly being exploited in the wild. According to information from forums like xss.is, threat actors are utilizing this vulnerability for credential theft.
The threat actor known as “Krypt0n” is linked to its exploitation and has developed malware known as “EncryptHub Stealer.”
The vulnerability’s potential for exploitation is underscored by its offer for sale on dark web forums, further emphasizing the urgency of patching affected systems.
Mitigation and Patch
Microsoft addressed CVE-2025-24071 in its March Patch Tuesday update. Users are advised to ensure their Windows systems are updated with the latest security patches to prevent exploitation.
As the vulnerability is actively being exploited, immediate action is crucial to protect against potential network spoofing attacks.
The discovery and exploitation of CVE-2025-24071 highlight the ongoing challenges in securing Windows systems against sophisticated threats.
By understanding how vulnerabilities like this one are exploited and taking proactive steps to patch and protect systems, users can significantly reduce the risk of falling victim to such attacks.
Are you from SOC/DFIR Teams? – Analyse Malware Incidents & get live Access with ANY.RUN -> Start Now for Free.
Keep your files stored safely and securely with the SanDisk 2TB Extreme Portable SSD. With over 69,505 ratings and an impressive 4.6 out of 5 stars, this product has been purchased over 8K+ times in the past month. At only $129.99, this Amazon’s Choice product is a must-have for secure file storage.
Help keep private content private with the included password protection featuring 256-bit AES hardware encryption. Order now for just $129.99 on Amazon!
Help Power Techcratic’s Future – Scan To Support
If Techcratic’s content and insights have helped you, consider giving back by supporting the platform with crypto. Every contribution makes a difference, whether it’s for high-quality content, server maintenance, or future updates. Techcratic is constantly evolving, and your support helps drive that progress.
As a solo operator who wears all the hats, creating content, managing the tech, and running the site, your support allows me to stay focused on delivering valuable resources. Your support keeps everything running smoothly and enables me to continue creating the content you love. I’m deeply grateful for your support, it truly means the world to me! Thank you!
|
BITCOIN
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge Scan the QR code with your crypto wallet app |
|
DOGECOIN
D64GwvvYQxFXYyan3oQCrmWfidf6T3JpBA Scan the QR code with your crypto wallet app |
|
ETHEREUM
0xe9BC980DF3d985730dA827996B43E4A62CCBAA7a Scan the QR code with your crypto wallet app |
Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.


































![THYMESIA | 16 MINUTES OF GAMEPLAY | [1080P 60 FPS]](https://techcratic.com/wp-content/uploads/2025/08/1756247055_maxresdefault-360x180.jpg)






































































