Andrew Orr <andreworr@appleinsider.com>
2025-09-04 09:57:00
appleinsider.com
A newly disclosed macOS flaw could have allowed an attacker to decrypt Keychain data without a password. Here’s how it worked, before it was patched.
Apple is known for its strong emphasis on security and privacy. However, a flaw in macOS Sequoia 15.0 allowed attackers to bypass these protections.
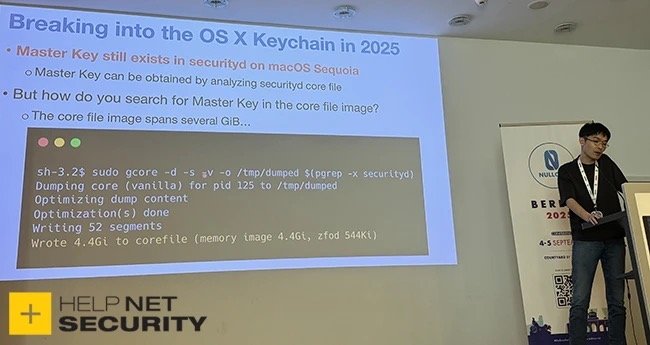
At Nullcon Berlin 2025, security researcher Koh M. Nakagawa from FFRI Security disclosed the issue. He found that Apple’s gcore debugging utility was granted a system-level entitlement, compromising essential security boundaries.
The flaw, now tracked as CVE-2025-24204, allowed anyone with access to read memory from any process, even with System Integrity Protection (SIP) enabled. The exposure revealed Keychain encryption keys and bypassed Transparency, Consent, and Control (TCC) restrictions.
It also enabled attackers to decrypt iOS apps running on Apple Silicon Macs. The vulnerability essentially undermined several of Apple’s most critical security defenses.
Fortunately, the gcore vulnerability didn’t require physical access, only the ability to run code locally on a Mac. Researchers say it wasn’t seen exploited in the wild before Apple patched it.
How the flaw was discovered
Nakagawa said he found the bug almost by accident. When Microsoft released ProcDump-for-Mac, he assumed it wouldn’t work on protected processes because SIP blocks that.
But during testing, he realized ProcDump could dump memory from nearly everything, including sensitive system processes. The secret was gcore, which had been granted the com.apple.system-task-ports.read entitlement.
What attackers could do
That entitlement gave gcore unrestricted memory access. Microsoft likely noticed it too, which is why ProcDump worked. But Nakagawa was the one who connected the dots and saw the security nightmare. “I was shocked about it,” he said.
Dumping memory from the securityd process let Nakagawa recover the master key used to encrypt the login Keychain. With that key, he could decrypt the entire Keychain without the user’s password.
Nakagawa also showed that attackers could bypass TCC, Apple’s system for controlling which apps can access files like photos or contacts. Since sandboxed apps load files into memory, attackers could dump memory and reconstruct protected documents using Apple’s vmmap tool.
Even iOS apps were vulnerable because Apple Silicon Macs can run iPhone and iPad apps whose binaries are encrypted at rest. Using gcore, Nakagawa was able to recover decrypted binaries while the apps were running, access that would normally require a jailbroken iPhone.
Apple’s response
Apple removed the problematic entitlement in macOS 15.3, released earlier in 2025. The company didn’t issue a flashy press release about it, which isn’t unusual. Security fixes often appear buried in changelogs with minimal detail.
Detection was possible through Apple’s Endpoint Security Framework, which can monitor for suspicious task_read_for_pid calls. But Nakagawa wasn’t optimistic about defenders catching such issues in real time. Even if enterprises spotted the entitlement, the only real fix was waiting for Apple’s update.
How to stay safe
If you’re running macOS Sequoia, update immediately to version 15.3 or later, since that’s where Apple removed the vulnerable entitlement. Older versions remain exposed, and there’s no workaround short of upgrading.
Users should also enable automatic updates to avoid lingering on a risky build. Keeping your Mac on the latest release is the simplest way to avoid unpatched flaws.
For extra security, consider using a password manager separate from Apple’s Keychain, so your most sensitive credentials aren’t all in one basket. It won’t protect against every macOS bug, but it adds another layer attackers have to break.
Finally, stay alert to Apple’s security advisories, which are posted on the company’s support site. They’re often light on details, but they’re the only official record of what’s been fixed and when.

Keep track of your essentials with the Apple AirTag 4 Pack, the ultimate tracking solution for your belongings. With over 5,972 ratings and a stellar 4.7-star average, this product has quickly become a customer favorite. Over 10,000 units were purchased in the past month, solidifying its status as a highly rated Amazon Choice product.
For just $79.98, you can enjoy peace of mind knowing your items are always within reach. Order now for only $79.98 at Amazon!
Help Power Techcratic’s Future – Scan To Support
If Techcratic’s content and insights have helped you, consider giving back by supporting the platform with crypto. Every contribution makes a difference, whether it’s for high-quality content, server maintenance, or future updates. Techcratic is constantly evolving, and your support helps drive that progress.
As a solo operator who wears all the hats, creating content, managing the tech, and running the site, your support allows me to stay focused on delivering valuable resources. Your support keeps everything running smoothly and enables me to continue creating the content you love. I’m deeply grateful for your support, it truly means the world to me! Thank you!
|
BITCOIN
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge Scan the QR code with your crypto wallet app |
|
DOGECOIN
D64GwvvYQxFXYyan3oQCrmWfidf6T3JpBA Scan the QR code with your crypto wallet app |
|
ETHEREUM
0xe9BC980DF3d985730dA827996B43E4A62CCBAA7a Scan the QR code with your crypto wallet app |
Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.