2025-09-08 08:38:00
micahflee.com
Last week, I wrote about how Joshua Aaron’s ICEBlock app, which allows people to anonymously report ICE sightings within a 5-mile radius, is – unfortunately, and despite apparent good intentions – activism theater. This was based on Joshua’s talk at HOPE where he made it clear that he isn’t taking the advice of local community groups, that ICE sightings aren’t verified in any way, and that he doesn’t know what he’s doing when it comes to security and privacy.
In that post, in the section about his “HIGHLY secure” server that he kept mentioning, I wrote:
Without providing more details, I also discovered that his server is running outdated software with known vulnerabilities.
I was intentionally vague because I knew that his server was vulnerable at the time of writing, and I didn’t want anyone to exploit one of these vulnerabilities before he had a chance to fix it.
ICEBlock has been downloaded over one million times from the App Store. I don’t know whether Joshua’s server stores data related to these users or the reports they submit, but it might, and he certainly bragged about the security of it in his HOPE talk.
I’m publishing this because it’s important for people who are trusting ICEBlock to know that the developer is careless about computer security, even when people specifically point out security issues and give him time to fix them. Hopefully his server doesn’t have any user data. Hopefully no one will hack his server despite the fact that he’s making it easy for them to. And hopefully this blog post will compel him to finally fix the issue.
Joshua runs two Bluesky accounts: @iceblock.app, the account of the ICEBlock app, and @joshua.stealingheather.com, Joshua’s personal account. His personal account had DMs closed, but the ICEBlock account had DMs open, so I sent him DMs there.
On September 1, I wrote:
Hey Joshua, I’m one of the people who saw your HOPE talk and asked some of the questions. I’m giving you a heads up that I’m preparing to publish a blog post about the app and your talk that isn’t very flattering. But also, I wanted to give you notice that you’re running a vulnerable version of Apache on your linode server. I’m not mentioning this specifically, but you should install updates
You seem to be running Apache httpd 2.4.57. See https://httpd.apache.org/security/vulnerabilities_24.html for more details, but this version of Apache has multiple critical CVEs which could take over your server. Like for example, this one https://nvd.nist.gov/vuln/detail/CVE-2024-38476
Then, an hour and a half later, I published my blog and sent him my Bluesky post about it:
I wrote about @iceblock.app, the developer’s infuriating HOPE talk, and how it’s unfortunately basically activism theater micahflee.com/unfortunatel…
He didn’t respond from the @iceblock.app account other than blocking me. (Which, honestly, isn’t very fair, since I’m not ICE.)
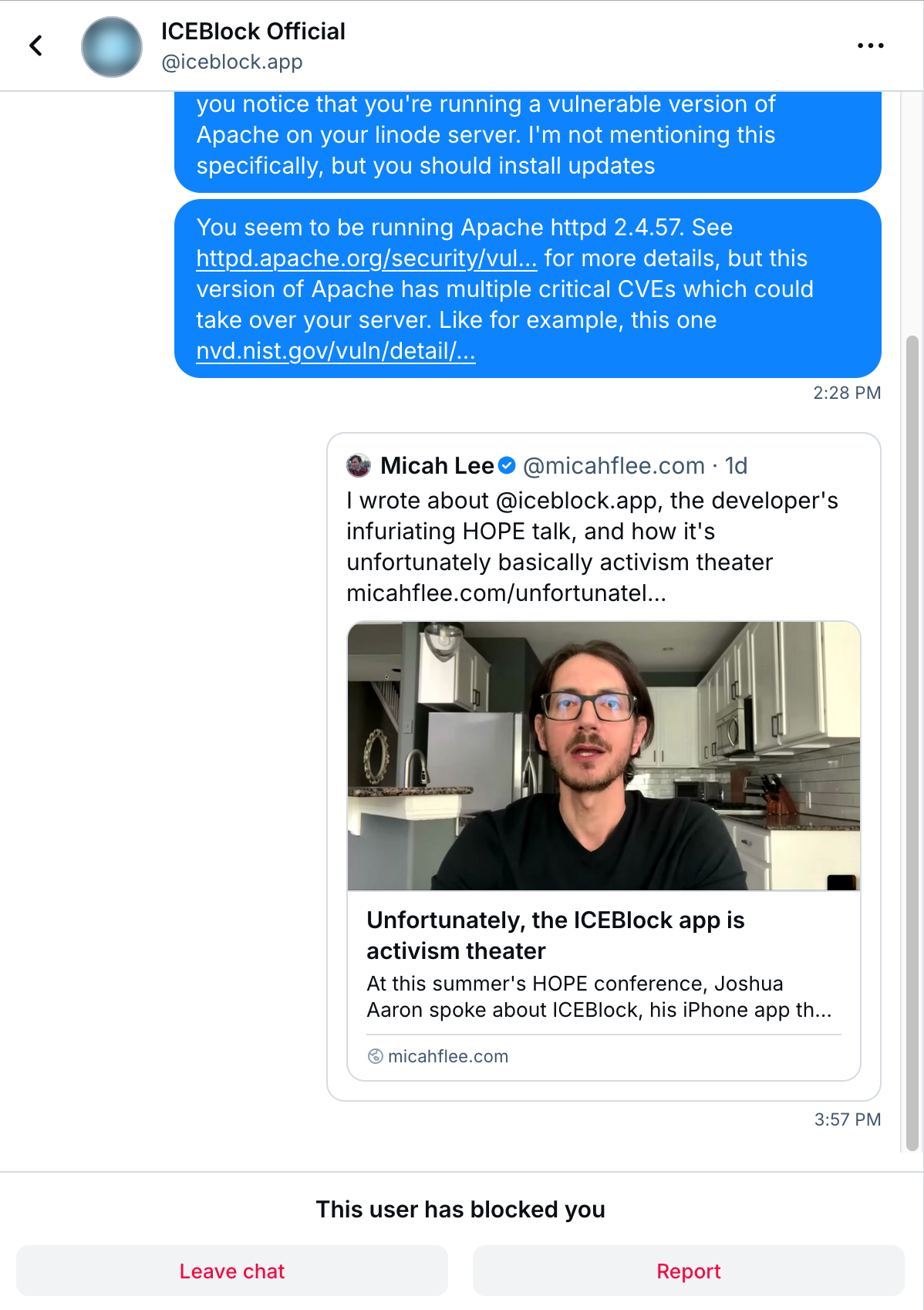
He did, however, send me a DM from his @joshua.stealingheather.com account, saying:
It would be so great if you could stop lying about me and ICEBlock. You are doing nothing to help. You don’t know me, my history, my knowledge, or anything more than hearing me at Hope.
Don’t bother responding because this will be my last and only communication with you. Do better.
To which I replied:
If I got anything wrong in my blog post, please let me know and I’d be happy to post a correction
Here’s a screenshot of the exchange.
A few days later, on September 3, I decided to check again. His server was still running Apache 2.4.57, which has multiple vulnerabilities. He ignored my report and didn’t fix it.
And just so you know, fixing this problem is extremely easy. He just needs to SSH in and run something like sudo apt update && sudo apt upgrade, wait for the Apache updated package to install, and his server would no longer be vulnerable.
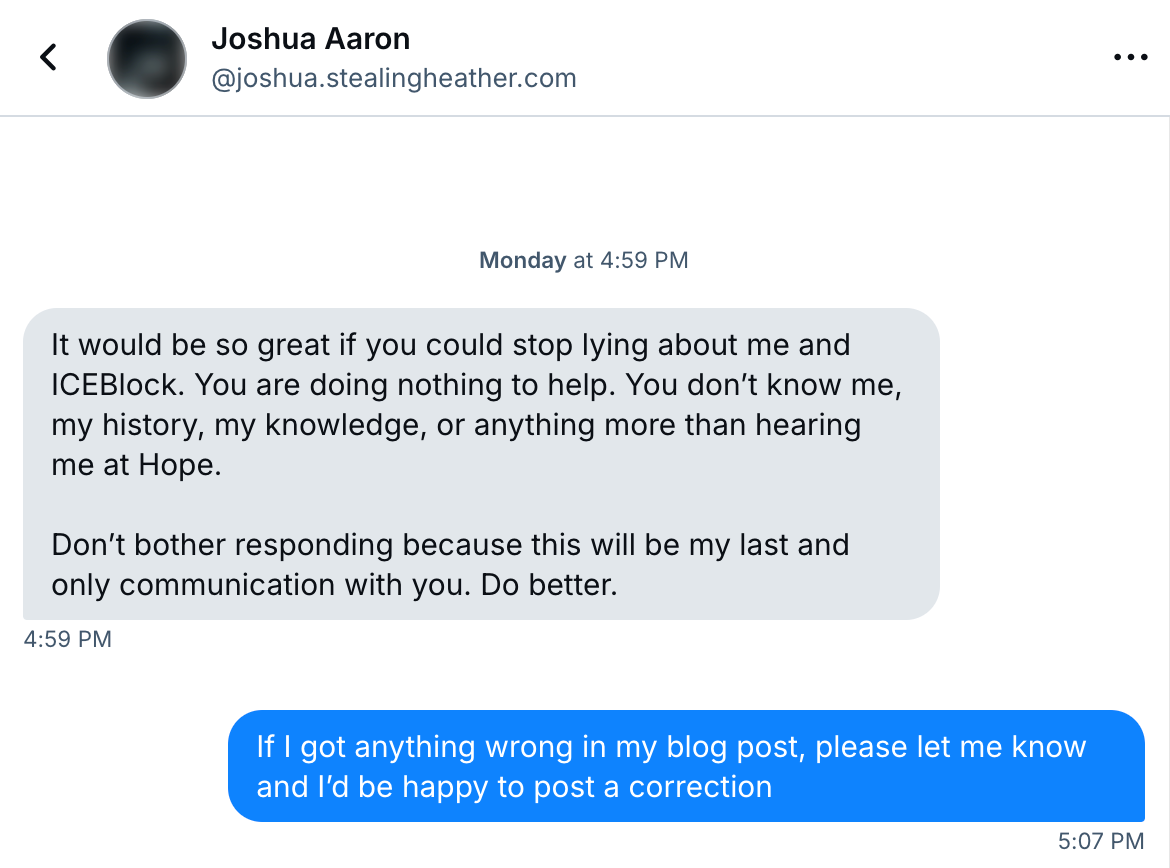
Seeing that he wasn’t taking this seriously, I decided to give him a deadline to patch his server before I publicly disclosed the vulnerability. I sent his @joshua.stealingheather.com account these messages:
Hey Joshua, I noticed that you still haven’t updated Apache on your server. I disclosed that you’re running Apache 2.4.57, which has known critical vulnerabilities, on September 1. I don’t know what data (if any) related to [ICEBlock] and its users that you store on your server. But until you update Apache, it might be trivial for anyone to hack your server and steal all of it. So, please install updates.
I’m giving you a week from when I first disclosed this before I write about it (so, September 8), which should give you more than enough time to update a package.
Just so you’re aware, I determined the version of Apache using nmap’s version detection feature. You can run
nmap -p443 -sV iceblock.appto test the version yourself, and it should show you this:PORT STATE SERVICE VERSION
443/tcp open ssl/http Apache httpd 2.4.57 ((Unix) OpenSSL/3.0.9)As a reminder, you can find the known vulnerabilities for this version of Apache here: https://httpd.apache.org/security/vulnerabilities_24.html
And, as I showed you before, just one of the vulns is CVE-2024-38476, which you can read about here: https://nvd.nist.gov/vuln/detail/CVE-2024-38476. This is a “critical” vulnerability that could potentially be used to execute scripts on your server. Please get back to me.
He didn’t get back to me. And an hour and a half later, he blocked me from this account too.
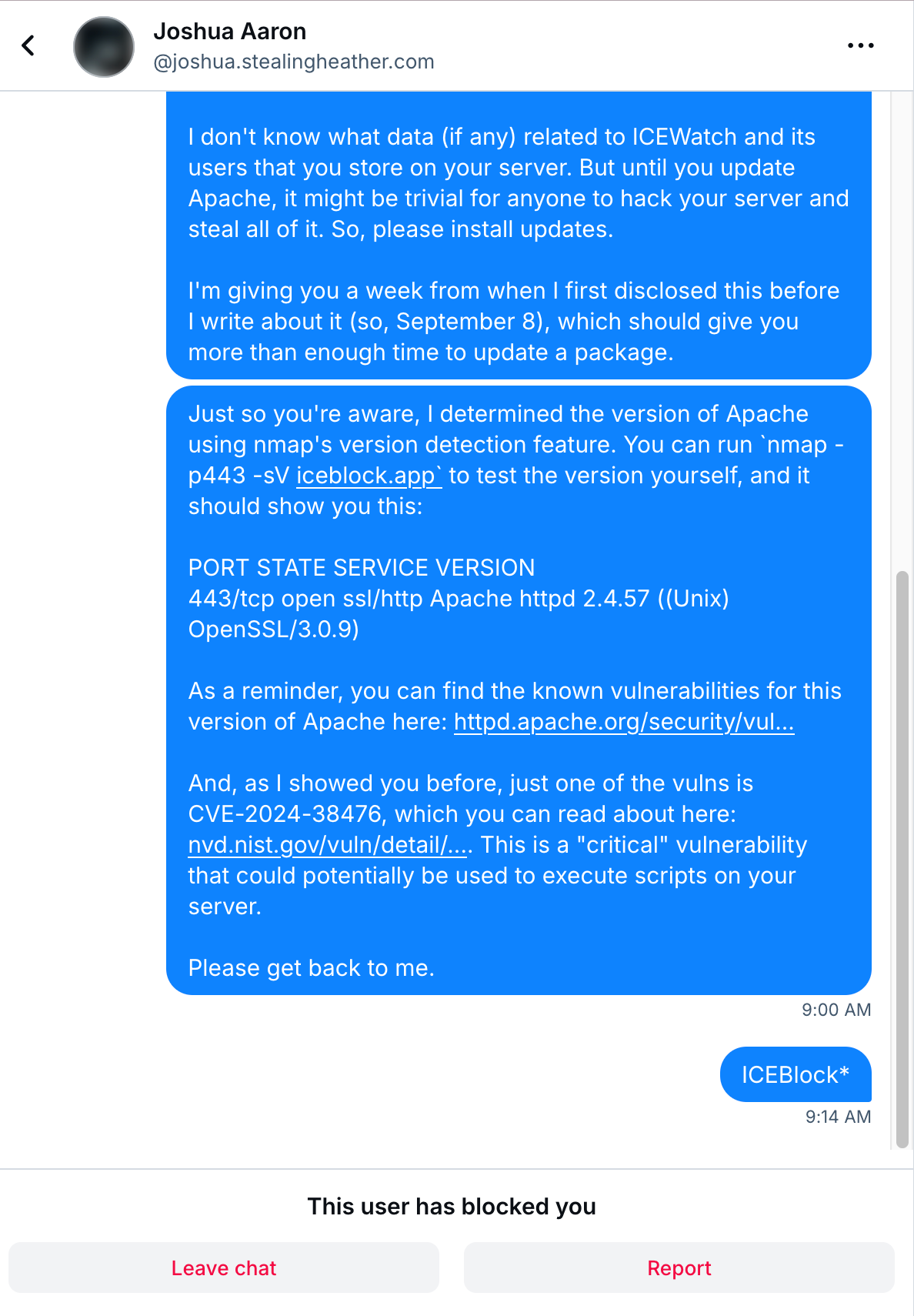
It’s now been a week, and I checked again: Joshua’s “HIGHLY secure” server is still running a version of Apache with multiple known critical vulnerabilities. And even with plenty of time to fix the issue, he still hasn’t.
I hope he isn’t storing any ICEBlock-related data on there.
Keep your files stored safely and securely with the SanDisk 2TB Extreme Portable SSD. With over 69,505 ratings and an impressive 4.6 out of 5 stars, this product has been purchased over 8K+ times in the past month. At only $129.99, this Amazon’s Choice product is a must-have for secure file storage.
Help keep private content private with the included password protection featuring 256-bit AES hardware encryption. Order now for just $129.99 on Amazon!
Help Power Techcratic’s Future – Scan To Support
If Techcratic’s content and insights have helped you, consider giving back by supporting the platform with crypto. Every contribution makes a difference, whether it’s for high-quality content, server maintenance, or future updates. Techcratic is constantly evolving, and your support helps drive that progress.
As a solo operator who wears all the hats, creating content, managing the tech, and running the site, your support allows me to stay focused on delivering valuable resources. Your support keeps everything running smoothly and enables me to continue creating the content you love. I’m deeply grateful for your support, it truly means the world to me! Thank you!
|
BITCOIN
bc1qlszw7elx2qahjwvaryh0tkgg8y68enw30gpvge Scan the QR code with your crypto wallet app |
|
DOGECOIN
D64GwvvYQxFXYyan3oQCrmWfidf6T3JpBA Scan the QR code with your crypto wallet app |
|
ETHEREUM
0xe9BC980DF3d985730dA827996B43E4A62CCBAA7a Scan the QR code with your crypto wallet app |
Please read the Privacy and Security Disclaimer on how Techcratic handles your support.
Disclaimer: As an Amazon Associate, Techcratic may earn from qualifying purchases.









































































































